Moriarty
@rudrakshsaini2
I like cats , computers and ctf’s | Captain @thehackerscrew1 | Slutt datafag
ID: 1172556085384736768
https://www.thehackerscrew.team 13-09-2019 17:02:22
1,1K Tweet
1,1K Takipçi
1,1K Takip Edilen



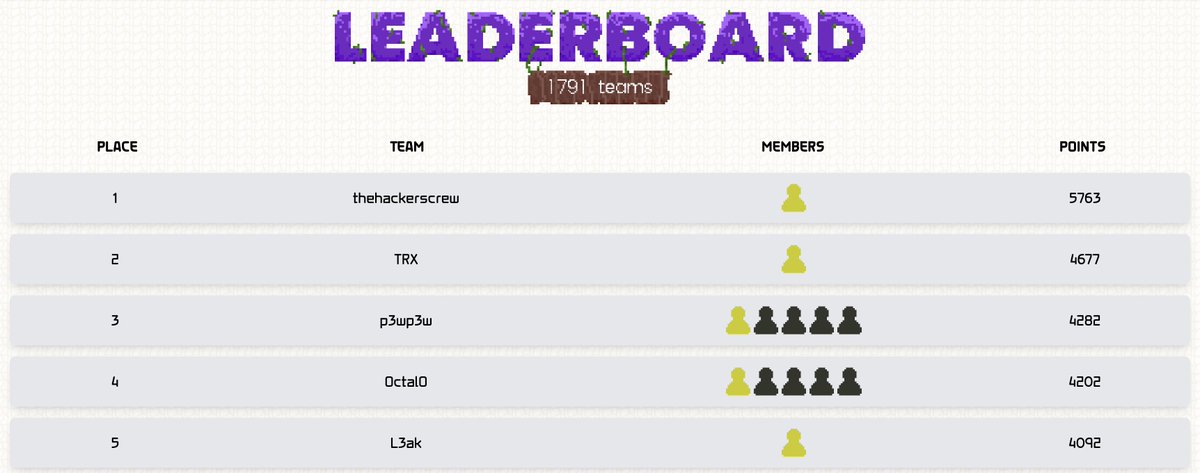
This weekend we participated in TFCCTF by The Few Chosen & NSSCTF by Norske Nøkkelsnikere and placed 🥇in both! Winning TFCCTF we also qualified for DefCamp finals in Bucharest, Romania. Huge thanks to both teams for organizing wonderful event and congratulations to other winners🥳










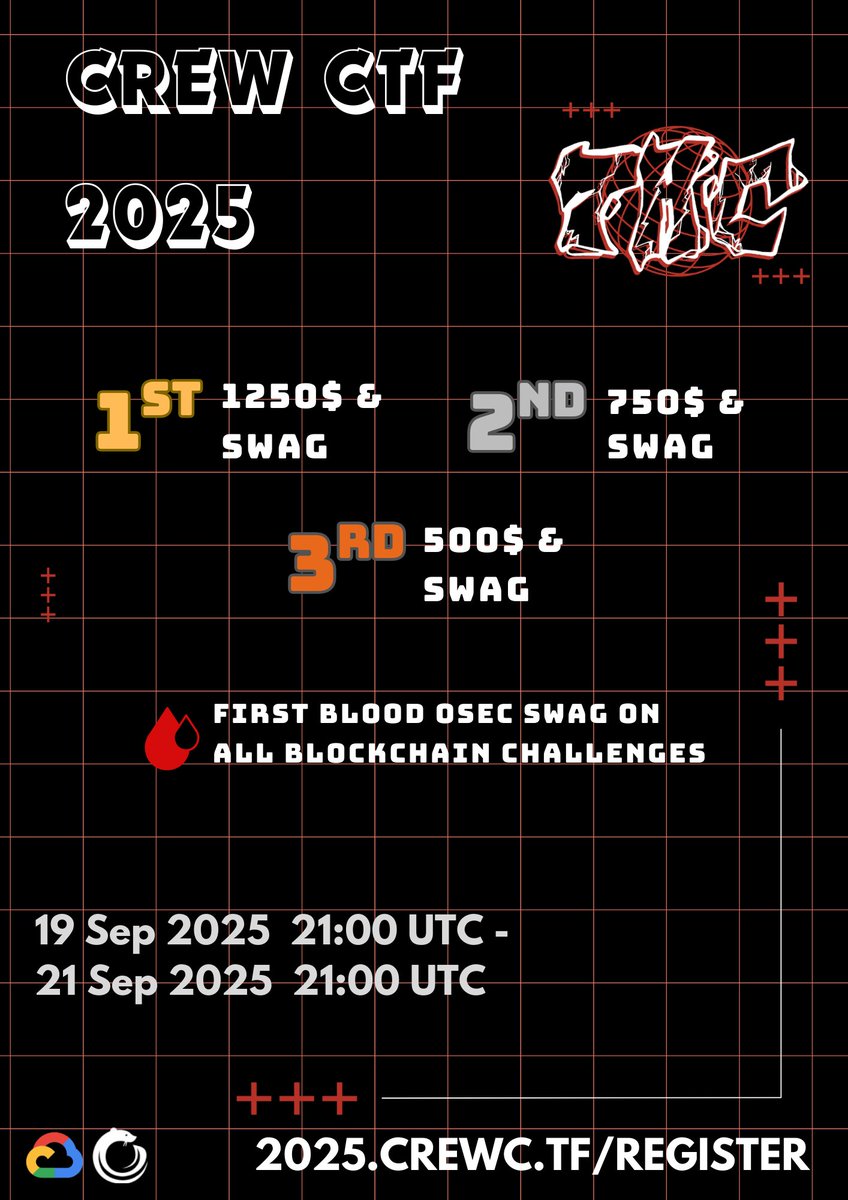
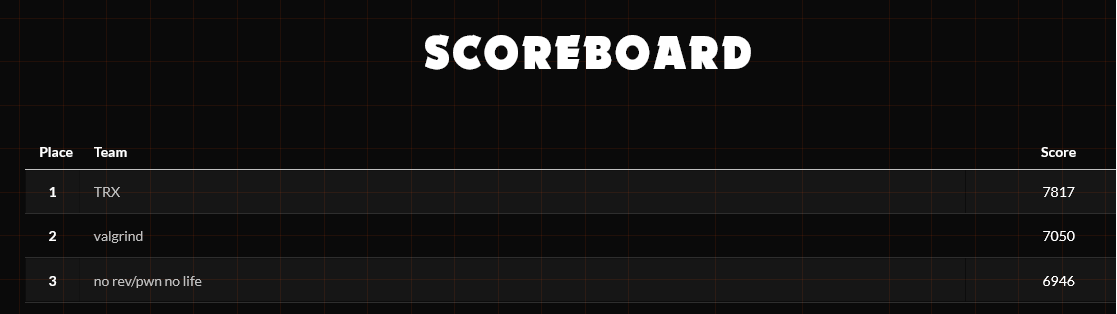
We are excited to announce that we played sardinia Cybercamp CTF 2025 organized by Sardinia Len (Srdnlen) last weekend and placed 🥈 Congratulations to other winners and thank you Sardinia Len (Srdnlen) for organizing such an awesome event. We are looking forward to playing the next edition.



Every retweet i see is to make Ayla Croft win, run for president next 😼👀