Ricerca Security
@ricercasec
Offensive Security Professionals | VAPT, R&D, Consulting, Training | Recognized by government agencies, Fortune 500s | Japanese: @RicercaSec_JP
ID: 1235115096528936960
https://ricsec.co.jp 04-03-2020 08:09:37
38 Tweet
2,2K Takipçi
0 Takip Edilen
















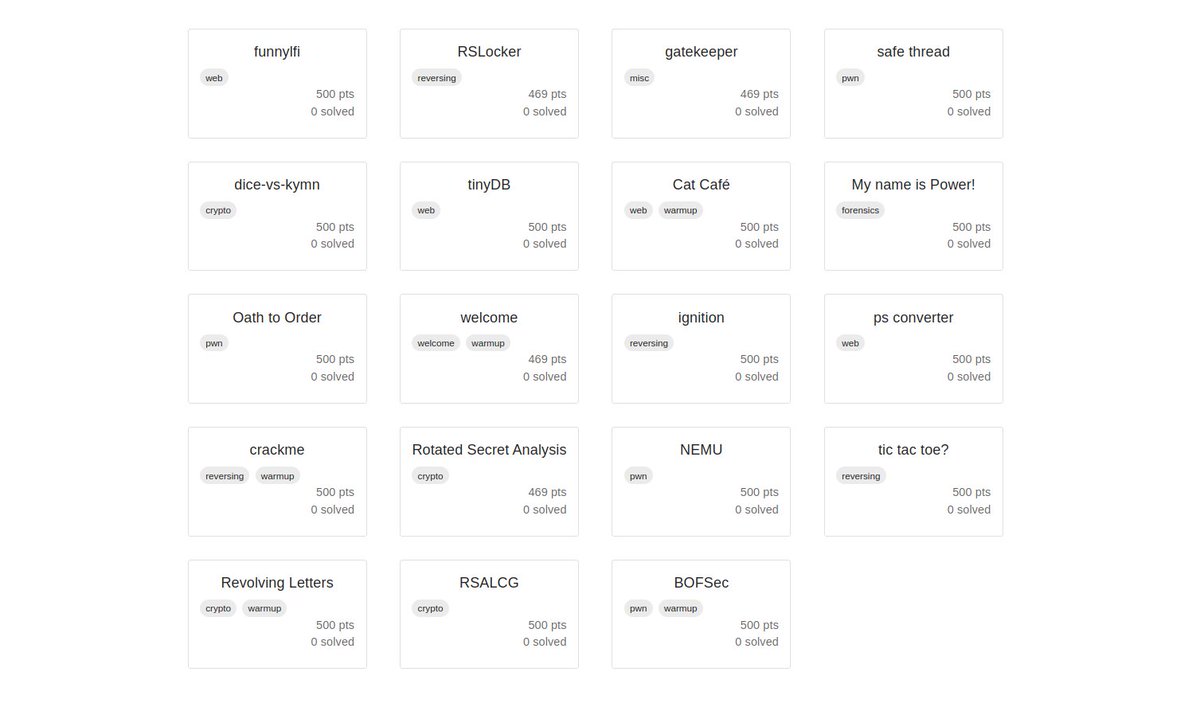
This is part 3 of our Fuzzing Farm series. Our team is also working on 1-day and 0-day exploits. In this article, we explain the process of developing a Proof of Concept (PoC) for undisclosed bugs, using a CVE of Google Chrome as an example. ricercasecurity.blogspot.com/2023/07/fuzzin…

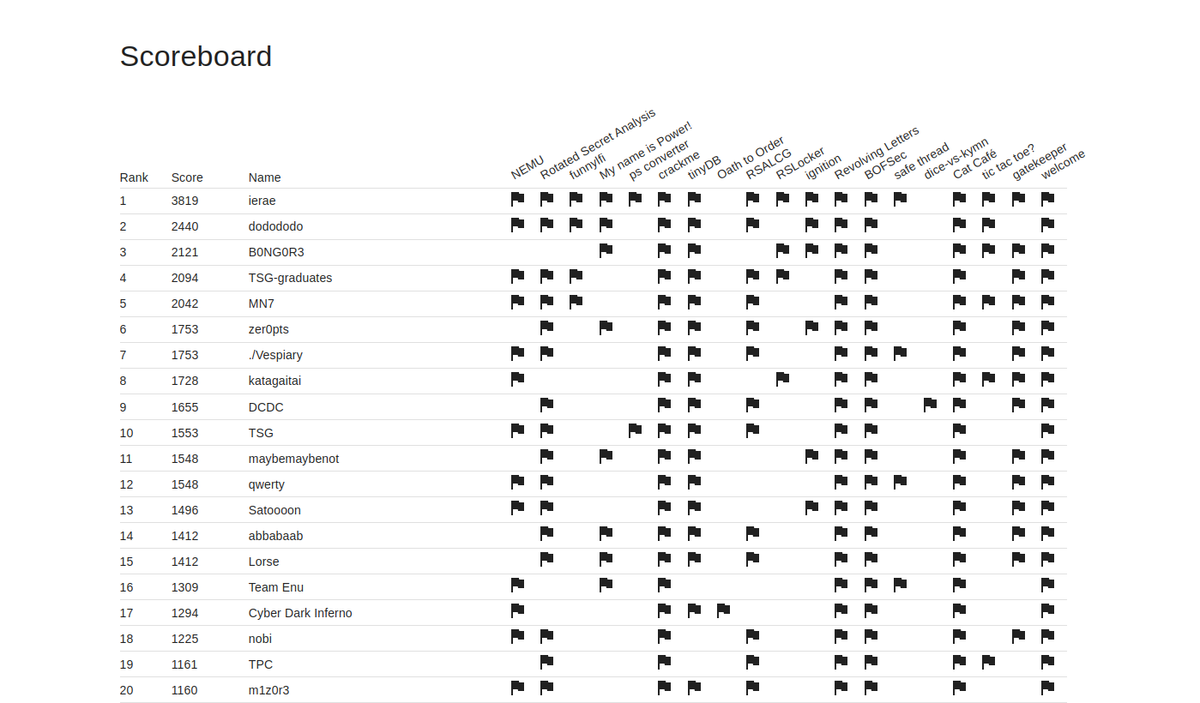
In the final part of our Fuzzing Farm series, we provide technical analysis and a PoC for CVE-2022-24834, an RCE vulnerability in Redis we found. While we reported it in 2022, the bug detail was disclosed last week. If you use Redis, patch it immediately. ricercasecurity.blogspot.com/2023/07/fuzzin…