
Hussam Linux
@hussamlinux
ID: 2576556256
02-06-2014 03:59:58
3,3K Tweet
614 Takipçi
2,2K Takip Edilen


Attacks on Maven proxy repositories, nice finding leading to stored XSS, by Michael Stepankin github.blog/security/vulne…

Leak HTTP Requests through Service Worker and XSS, an interesting XSS use-case, by Abdullah Al-Sultani tech.alsultani.me/2025/02/10/lea…



1. The target had an "Add Contact" feature. It was used to add contacts to an account, but those contacts could be given a wide range of permissions. The request to add a contact looked like this: POST /addcontact?accountId=123 { "accountId": 123, "email": "[email protected]" }






Find the origin servers of websites protected by Cloudflare, Sucuri, or Incapsula with a misconfigured DNS. ⚔️ - github.com/MrH0wl/Cloudma… Credit: Md Ismail Šojal 🕷️ #infosec #bugbountytips #Cybersecurity


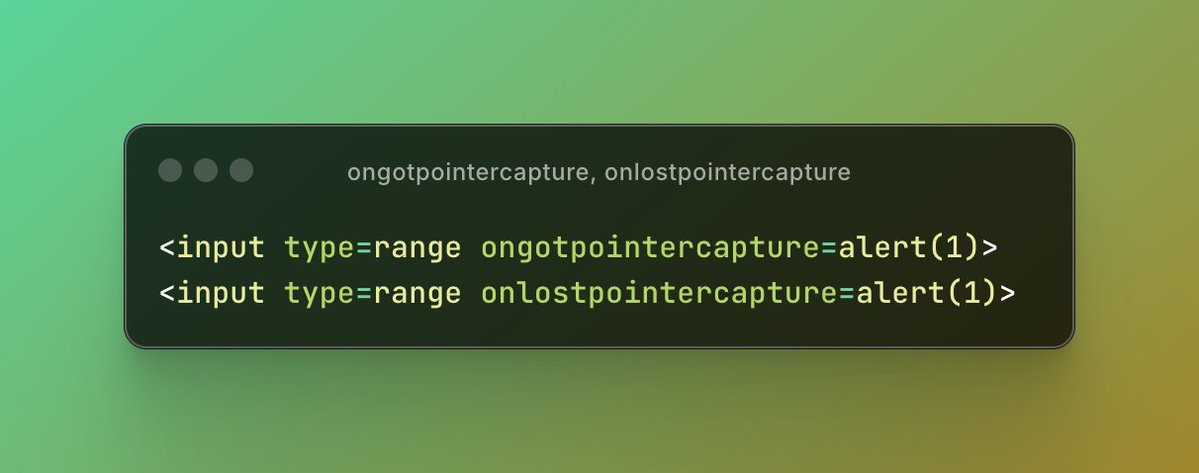
WAFs still blocking your payloads? Try our newest pointer capture tricks. Our XSS cheat sheet just got an upgrade thanks to Ahsan Shahid. portswigger.net/web-security/c…




How to access servers behind Cloudflare by bypassing the firewall? FearsOff Cybersecurity #bugbountytips #cloudflare #firewall #bypass 1) Found a sweet hostname but Cloudflare Firewall blocks you? There's a neat trick attackers can use if the origin is misconfigured.




Kirill Firsov FearsOff Cybersecurity I wrote two writeups about cloudflare: The first one about bypassing WAF rules if it only allows cloudflare ips only 0vulns.medium.com/rip-cloudflare… The second one about finding the origin server behind cloudflare using cookies name 0vulns.medium.com/a-deep-dive-in…






