Aditya Soni
@hetroublehacker
~ Your friendly neighbourhood hacker ¯\_(ツ)_/¯
ID: 439225648
https://www.youtube.com/@HeTroubleHacker 17-12-2011 14:26:40
1,1K Tweet
2,2K Takipçi
860 Takip Edilen


RFC 2047 "encoded-word" is crazy! It lets you smuggle encoded payloads into email addresses and the craziest thing is that some parsers decode it before validation 👇 Shout out to Gareth Heyes \u2028 for this 🔥





HackerOne Clubs across Asia-Pacific are adding fresh energy. Welcome to these new Brand Ambassadors! 🇮🇩 ZeeAgil & 🇮🇩 root_geek280 (Indonesia—new club!) 🇮🇳 Aditya Soni & 🇮🇳 Yash Sharma (India North) 🇮🇳 charan (India South) 🇮🇳 Debangshu 🇮🇳🥷 & snifyak (India East) 🇧🇩




When HTTP/1.1 Must Die lands at DEFCON we’ll publish a Web Security Academy lab with a new class of desync attack. One week later, I’ll livestream the solution on air with Off By One Security! You’re invited :) youtube.com/live/B7p8dIB7b…

When applying for a job at McDonald's, over 90% of franchises use "Olivia," an AI-powered chatbot. We (Ian Carroll and I) discovered a vulnerability that could allow an attacker to access the over 64 million chat records using the password "123456". ian.sh/mcdonalds








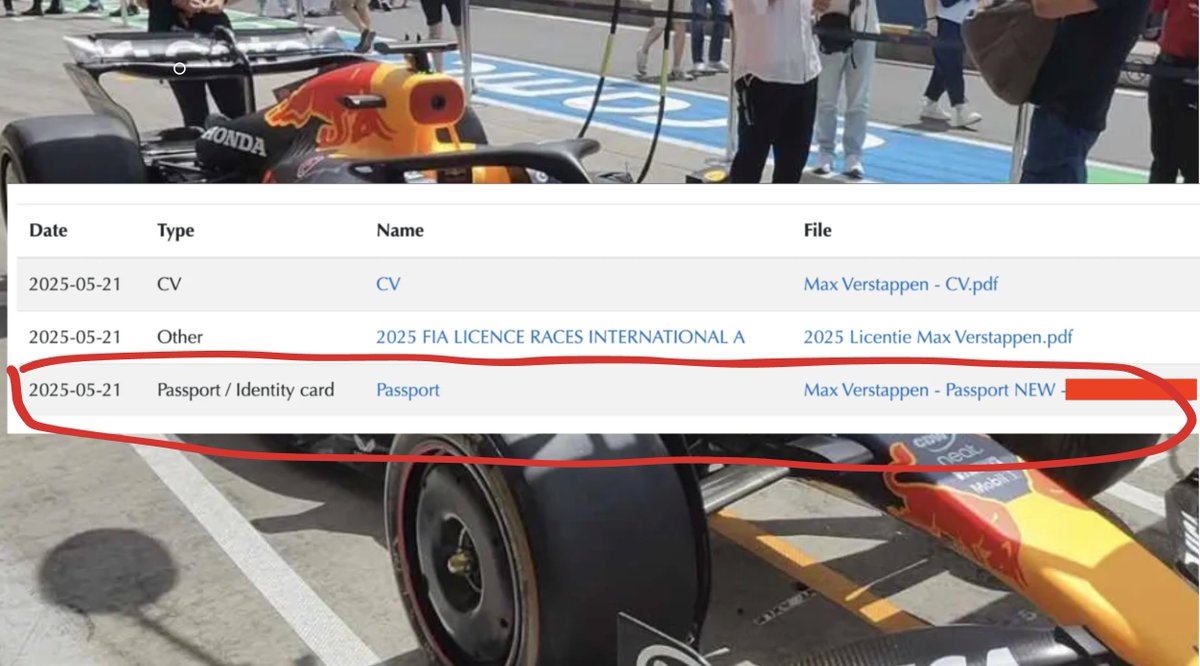
We found a way to access Max Verstappen's passport, driver's license, and personal information. Along with every other Formula1.com driver's sensitive data. It took us 10 minutes using one simple security flaw 🧵

You found a bug. You wrote the PoC. You hit Submit. …but what happens next? 👀 Join Sameer Sameer Bhatt (Debugger) , Senior Triager @HackerOne, as he breaks down what really goes on behind triage, reports, reviews, rejections & rewards! 🎯 Pure triager insights + 🎁 PentesterLab