bounty_hunter1412
@cutiechenny
OSCP | OSWP | OSEP | CRTP | CRTE | CRTO | Security professional
ID: 1680259566
18-08-2013 09:22:03
374 Tweet
1,1K Takipçi
621 Takip Edilen








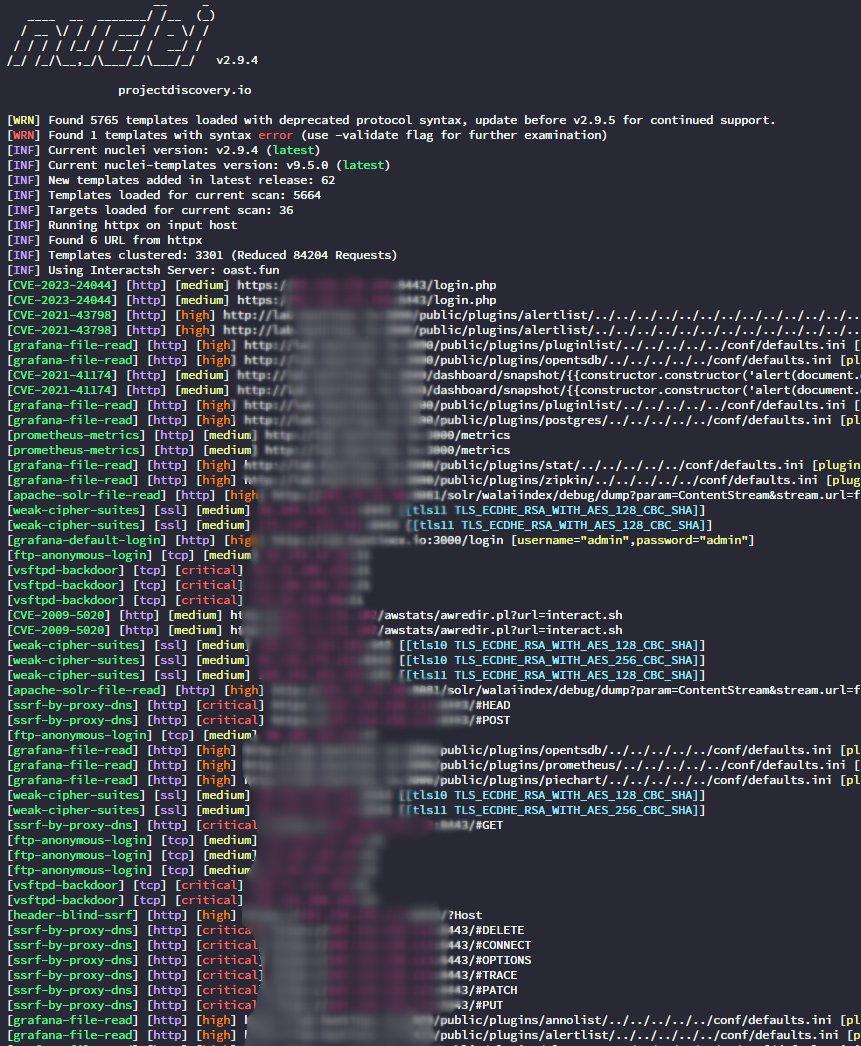
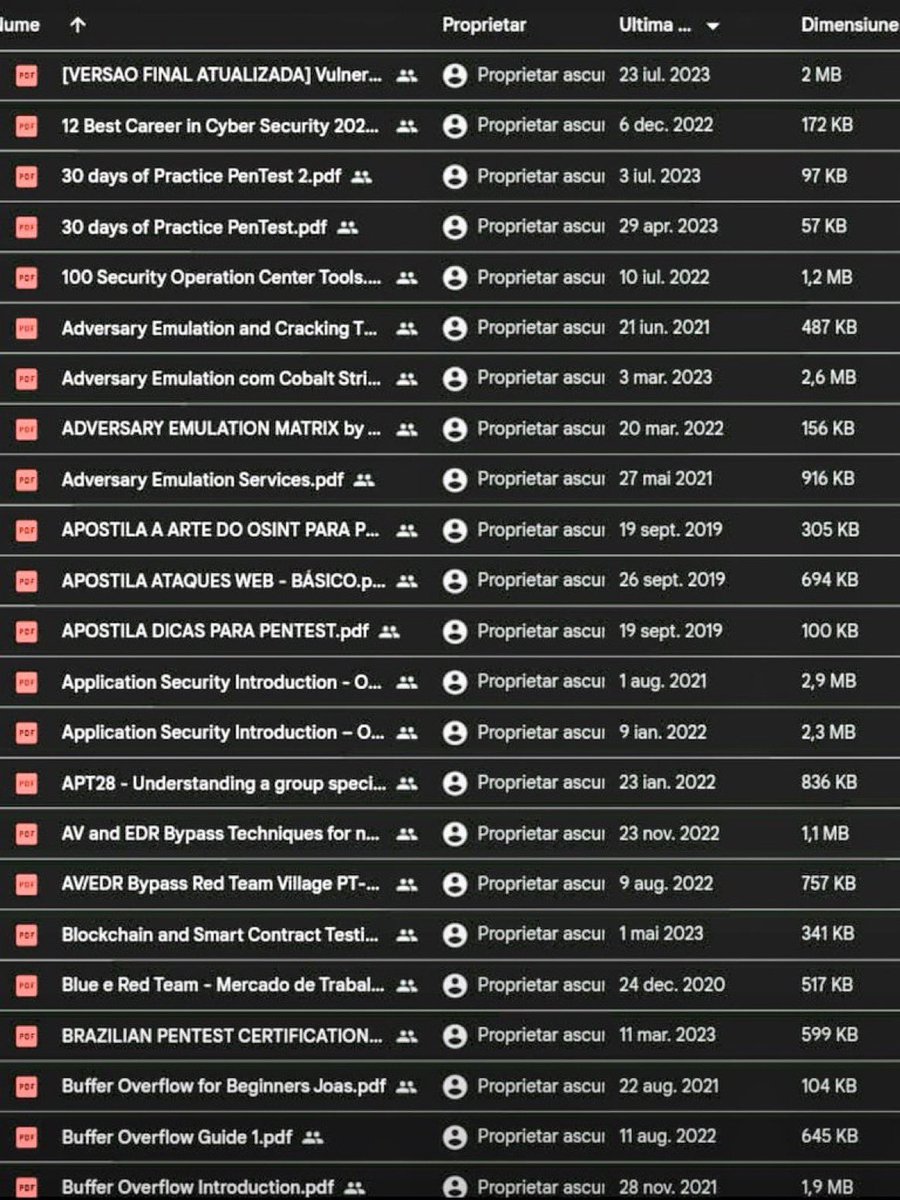
200+ Hacking / Infosec pdfs Source: drive.google.com/drive/u/0/mobi… Credit: Joas Antonio #infosec #Hacking #infosecurity #Malware #bugbountytips #CTF #BugBounty #vulnerability #pwn #CyberSecurityAwareness #CyberSecurity #cybersecuritytips

🔥 Data Leak Alert! #Microsoft accidentally exposed 38TB of private data, including secrets, keys, passwords, and 30K+ internal Teams messages, on AI #GitHub repository due to a security glitch. Read more in this article: thehackernews.com/2023/09/micros… #ArtificialIntelligence #Tech