Ben Brigida
@the_real_benb
ID: 894771821165256708
08-08-2017 04:06:41
18 Tweet
89 Takipçi
56 Takip Edilen








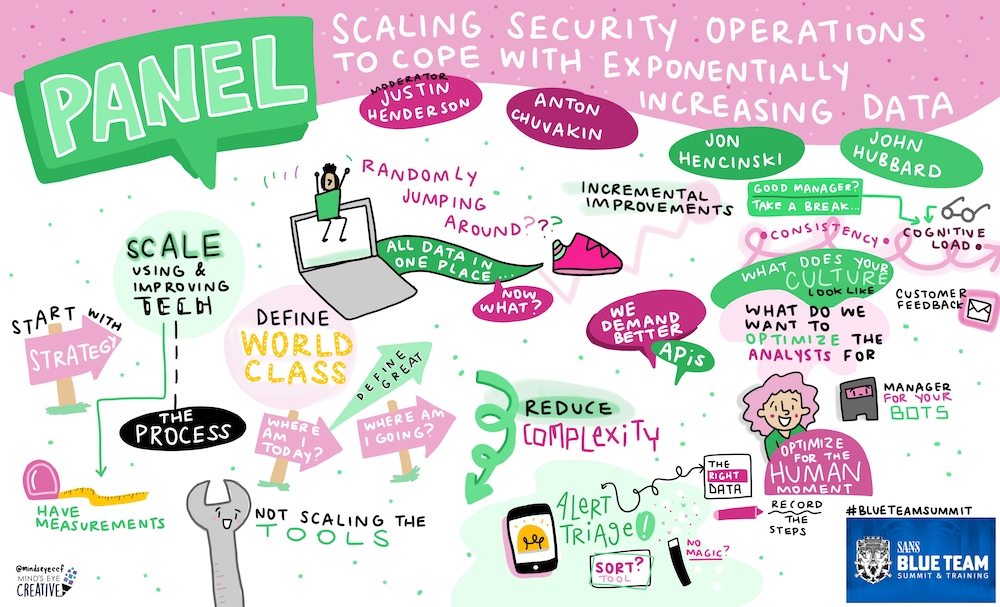
Jon Hencinski Sounds a lot like diagnostic inquiry chrissanders.org/2016/05/how-an…




Another awesome #BlueTeamSummit panel, another great visual summary from Ashton Rodenhiser !