Aloïs Thévenot
@techbrunchfr
Jack of all trades, master of some. CTO / Pentester @vaadata - Bluesky: @techbrunch.fr
ID: 231532644
https://www.techbrunch.fr 28-12-2010 19:58:54
5,5K Tweet
1,1K Takipçi
965 Takip Edilen


FIDO downgrades are still possible, in reverse proxy phishing attacks, if you manage to convince the server that your device does not support strong MFA. 🪝🐟 Research from Proofpoint: proofpoint.com/us/blog/threat…


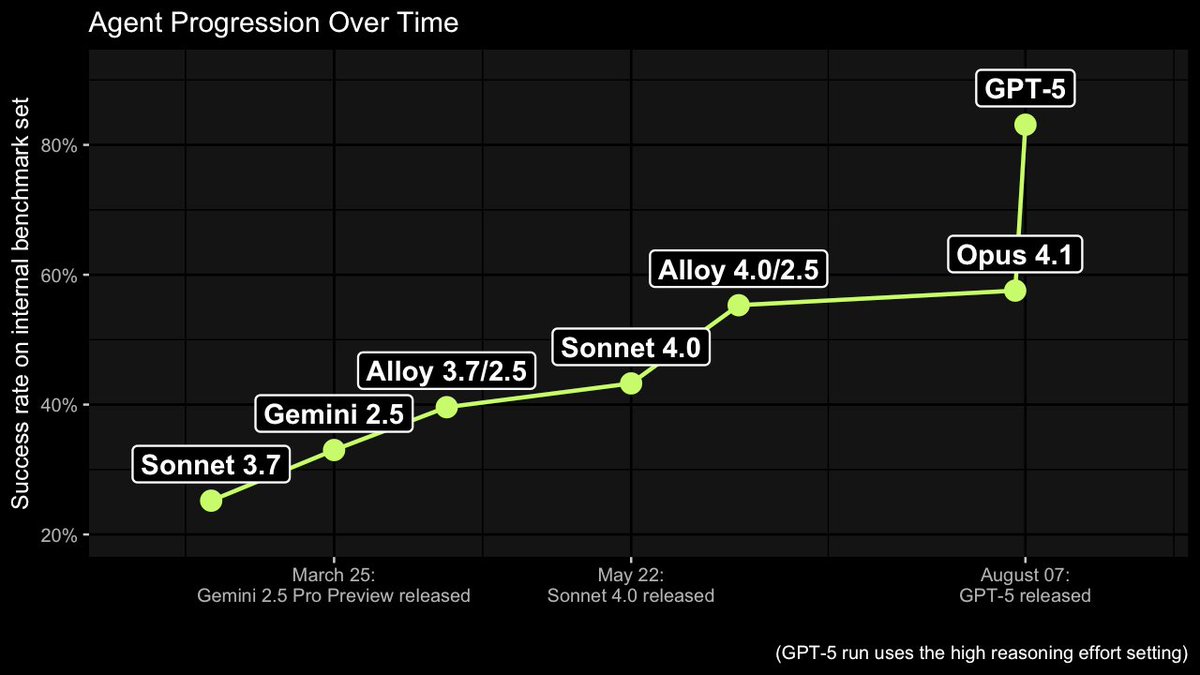
Xbow raised $117M to build AI hacker agents, in Alias Robotics open-sourced it and made it completely free. Github: github.com/aliasrobotics/… Paper: arxiv.org/abs/2504.06017








Trying to fly under EDR's radar? Logan Goins explains how to use HTTP-to-LDAP relay attacks to execute tooling completely off-host through the C2 payload context. Perfect for when you need LDAP access but want to avoid being caught stealing creds. ghst.ly/41mjMv7