

Are you ready to take your defense against supply chain attacks to the next level? Join Jim Manico @ AllAroundTheWorld, @JavaJulius & S Smith tomorrow for this exciting webinar on WAF & Runtime Protection!
Register: mergebase.com/waf-vs-java-ru…
#waf #runtimeprotection #softwaresupplychain


Join Jim Manico @ AllAroundTheWorld , @JavaJulius & S Smith in this mini-webinar series on MergeBase’s patented Java Runtime Protection.
Starting next Tuesday, January 17th at 10 am PST.
Check more info and register: mergebase.com/runtime-webina…
#runtimeprotection #sca #softwaresupplychain


🔔 Last chance to register for our 'Safeguarding Software: Supply Chain in 2024' webinar, happening today at 10am PT!
Equip yourself with #DevSecOps and #SoftwareSupplyChain knowledge directly from the forefront of industry research.
🔗 Register now: jfrog.co/3VLPTmb




Kubernetes Community Days Istanbul 2023
#redhat #secure #softwaresupplychain #kubernetes
red.ht/trusted

SoK paper: Taxonomy of Attacks on Open-Source Software Supply Chains accepted at IEEE Symposium on Security and Privacy (S&P) 2023
For the full article: assuremoss.eu/en/resources/P…
#OpenSourceSecurity , #SoftwareSupplyChain , #Attacks , #IEEES &P2023

With the increase of #cyberattacks , securing the #SoftwareSupplyChain is crucial.
If 56% of respondents applying #security scans at both the code & #binary levels enough?
Download the full JFrog Software Supply Chain State of the Union 2024 report: jfrog.co/3TzsVNg


AEGIS leads #RESCALE as the Scientific and Technical Coordinator, ensuring scientific integrity, technical excellence, and the successful execution of the project. #CyberSecurity #AEGIS #SoftwareSupplyChain

We are happy to say that our CTO is a panelist at the upcoming #OpenSource Exchange event hosted by Revenera. If you’re interested in hearing more about the #softwaresupplychain and application #security , join us on June 7th!
info.revenera.com/SCA-EVNT-OpenS…

We'll be at Open Source Summit North America!
#opensourcesoftware #SoftwareSupplyChain #CyberSecurity #OpenSource Security #SecureCoding #Sigstore #OpenSource #DeveloperCommunity


Discover how to protect your organization against unauthorized code execution attacks in our blog.
ow.ly/G8rp50RfCGM
#Cybersecurity #CodeSign ing #CodeSign
#SoftwareSupplyChain #SoftwareSupplyChain Security #SupplyChain Attack #SupplyChain


Securing the Software Supply Chain: Key Strategies Revealed!
Discover expert tips to ensure your software supply chain is secure in Dark Reading's latest Tech Insights report.
#CyberSecurity #SoftwareSupplyChain #SecurityTips - darkreading.com/cyber-risk/tip…

Learn from the notable #softwaresupplychain attacks of 2022, with the help of:
AmitaiBs3
Cesar Cerrudo
Mike Hanley
Scott Gerlach
Sherrod DeGrippo 🦓

dzone.com/articles/platf… Chainguard ⛓️ #softwaresupplychain #devsecops #cloudnative #kubernetes #containers #chainguard

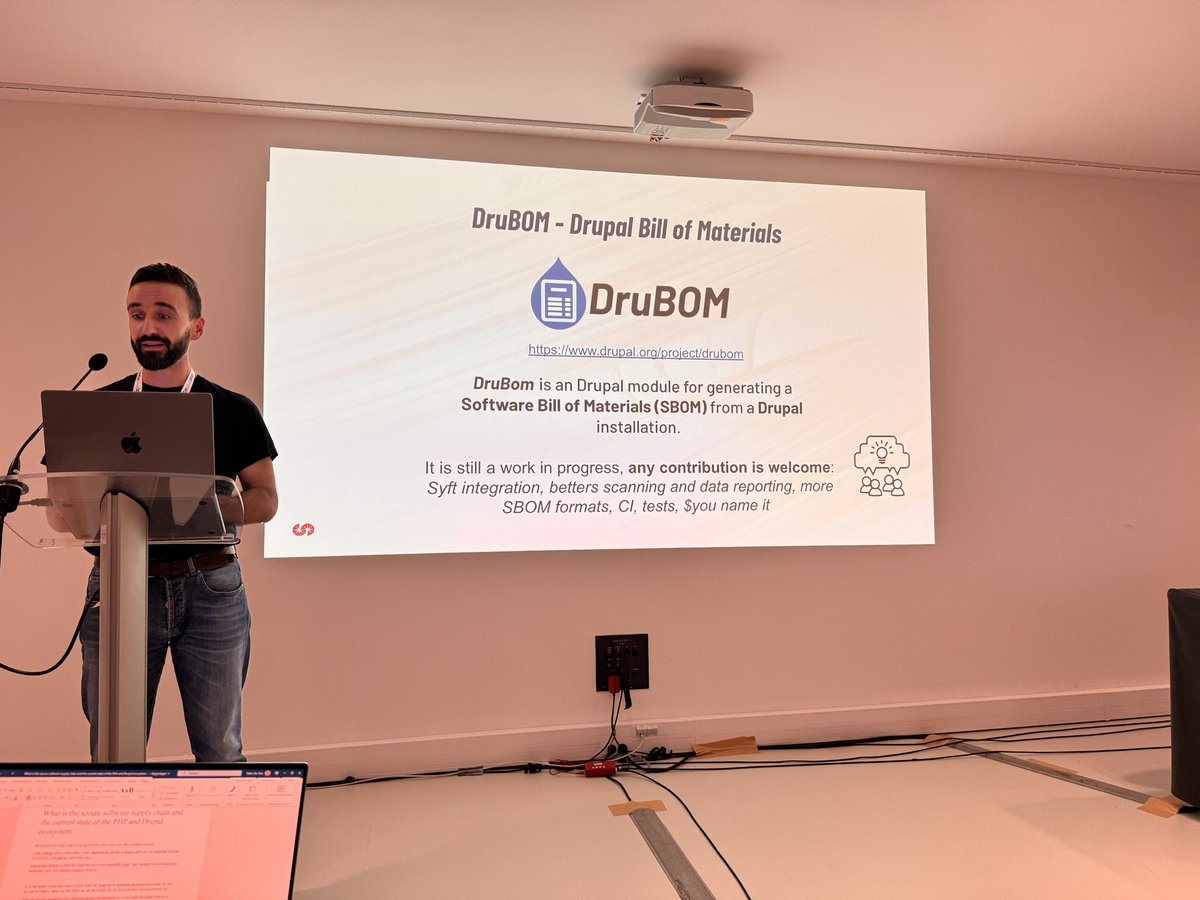
It was a blast, thanks DrupalCon Barcelona 2024 for having me. For anyone interested just uploaded the slides here: paolomainardi.com/talks/
#softwaresupplychain #sbom #sigstore

New software composition analysis tool Black Duck Supply Chain Edition released by Synopsys admin-magazine.com/News/Black-Duc… #SoftwareSupplyChain #security #tools #BlackDuck #SBOM #licensing

📣 SIGHUP and Chainguard ⛓️ joined forces to deliver Cutting-Edge #SoftwareSupplyChain #Security in the European Market 🚀
blog.sighup.io/sighup-and-cha…

.Docker Build Cloud is here! 🐳🧱☁️ Scout GA leads 'Local + Cloud' push at #DockerCon . Features Rob Strechay #SASinnovate, Katie Norton, Larry Carvalho #Seattle, Dan Lorenc, Mohammad-Ali A'RÂBI, Scott Johnston and more. #DockerScout #softwaresupplychain security #softwaresupplychain techtarget.com/searchsoftware… via @techtargetnews

