LIVE 🚨
The first #MultiversX smart contract written in the Swift language has been successfully deployed on the devnet 🔥
This contract has one endpoint called 'echoHelloWorld' which always returns 'Hello World!'
The entire experiment was conducted during tonight's



📌 How to Use OMNIA Protocol - DeFi RPC:
1️⃣ Launch app.omniatech.io
2️⃣ Connect your wallet
3️⃣ Generate endpoint
4️⃣ Select a blockchain and customize the subscription
Choose 'help me' if unsure.
5️⃣ Enable Frontrunning & Honeypot protection
6️⃣ Sign the request in the MetaMask wallet




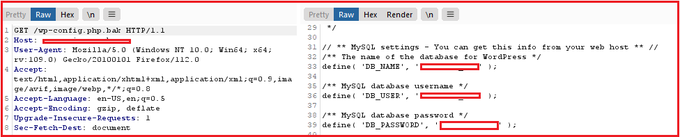
How I almost got 2k$ through multi endpoint race condition
medium.com/@0x3adly/how-i…
#CyberSecurity #bugbountytips #infosec



The Liquit and Recast Software team had a great time at the Modern Endpoint Management Summit in Paris! 🙌
#MEMSummit


Thought your firewall was enough?
Guess again... AiTM phishing, OAuth exploits, SSO attacks...hackers are getting creative targeting cloud identities.
Understand the next wave of cyberattacks – read this article: thehackernews.com/2024/04/showca…
#cybersecuritytips #infosecurity