

In order to issue #ISO certifications with the seal of an accreditation body, accredited #auditors undergo a rigorous process, including being audited themselves. Learn why it's crucial to choose accredited auditors in our latest blog by BARR Advisory. e.cloudsecurityalliance.org/l/908632/2024-…


The indispensable nature of email makes it the primary attack vector for bad actors - email attacks have been the leading cause of cybercrime losses for the past 7 years. Abnormal Security shares 10 considerations to shape your email #cloudsecurity strategy: e.cloudsecurityalliance.org/l/908632/2024-…

The treasure hunt for #DataSovereignty poses a challenge in today's global marketplace. Dive into the complexities of #CloudSecurity and vendor relationships with insights from the Security Sessions Podcast by Thales Cloud Security. Read more here: e.cloudsecurityalliance.org/l/908632/2024-…


As your business grows, you also outgrow your existing #cybersecurity processes. Recognizing when and how to audit these outdated processes is essential for keeping your org secure. Explore a template created by Vanta to help with these audits → e.cloudsecurityalliance.org/l/908632/2024-…

#CloudGaming 🎮 has changed the game industry, allowing users to stream their favorites with unprecedented ease. But it’s also opened the door to new risks for #DataSecurity . Ashwin Chaudhary, CEO Accedere, offers advice for striking that balance: e.cloudsecurityalliance.org/l/908632/2024-…


The days of the #CISO as the lone wolf 🐺 are over. #Cybersecurity today demands a business-savvy superhero 🦸 who understands the intricate dance of protecting the organization while supporting its growth. Zscaler CISO Ben Corll explores what this means: e.cloudsecurityalliance.org/l/908632/2024-…

Stop talking to your #AI —start collaborating with it! #PromptEngineering is the key to unlocking the full potential of #LLMs . Dr. Chantal Spleiss, CSA AI Governance & Compliance Working Group Co-Chair, breaks down how to get the most bang for your AI buck. e.cloudsecurityalliance.org/l/908632/2024-…

#RemoteCodeExecution (RCE) is a straightforward concept with profound implications and the potential for severe damage. A prime example is the infamous #Log4j flaw. In this Uptycs - CNAPP for Hybrid Cloud Security blog, gain a deeper understanding of RCEs within the #AWS environment 👇 e.cloudsecurityalliance.org/l/908632/2024-…


With people working from anywhere and everywhere on all kinds of devices, #IdentityAndAccessManagement is kind of a big deal these days. If you’re just starting out on your IAM journey, we’ve got you covered. Review 10 essential IAM terms → e.cloudsecurityalliance.org/l/908632/2024-…

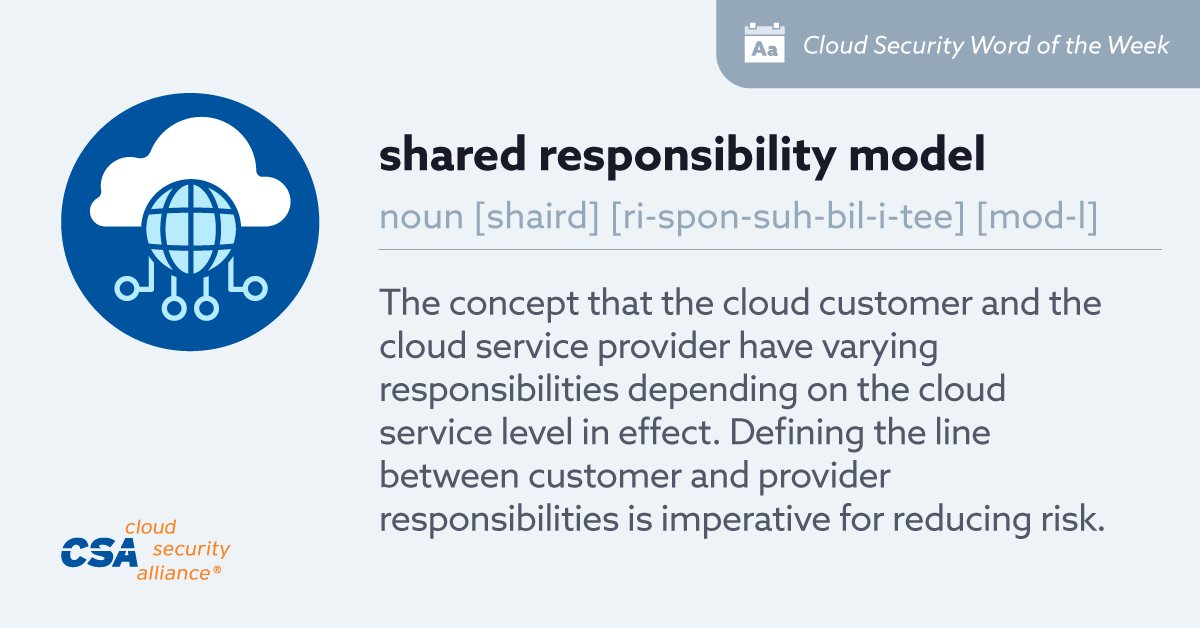
Today’s Word of the Week is: #SharedResponsibilityModel ☁️🙋🏿♂️🙋🙋🏽♀️. This is the concept that the cloud customer and the cloud service provider have varying responsibilities. Discover how the model is applied to GRC and BCDR → e.cloudsecurityalliance.org/l/908632/2024-…

#GenAI , with its ability to create seemingly magical outputs from text to code, is undeniably exciting. However, lurking beneath this shiny surface lies a Pandora's box 📦 of potential risks that demand immediate attention. Get an overview of the risks → e.cloudsecurityalliance.org/l/908632/2024-…



For today’s CSA Community Spotlight 🔦, we’re interviewing Dr. Ricci Ieong, Principal Consultant at Hatter Company and eWalker Consulting. Get Ricci’s perspective on CSA standards, the development of our CCAK program, and CSA’s long-lasting legacy: e.cloudsecurityalliance.org/l/908632/2024-…