
Stuart Ashenbrenner 🇺🇸 🇨🇦
@stuartjash
Principal macOS Security Researcher at @HuntressLabs | Creator of @Crash_Security | Reviewer at @bestthrillbooks | @MillennialGirlDad on @SubstackInc
ID: 712111281558331394
22-03-2016 02:58:54
7,7K Tweet
1,1K Takipçi
1,1K Takip Edilen







North Korean hackers deepfake execs in Zoom call to spread Mac malware - Bill Toulas bleepingcomputer.com/news/security/… bleepingcomputer.com/news/security/…


Not only is Huntress a generous supporter of our Foundation, they also consistently publish top-notch research on emerging macOS threats 🤩 Their latest (by alden & Stuart Ashenbrenner 🇺🇸 🇨🇦): "Feeling Blue(Noroff): Inside a Sophisticated DPRK Web3 Intrusion": huntress.com/blog/inside-bl…



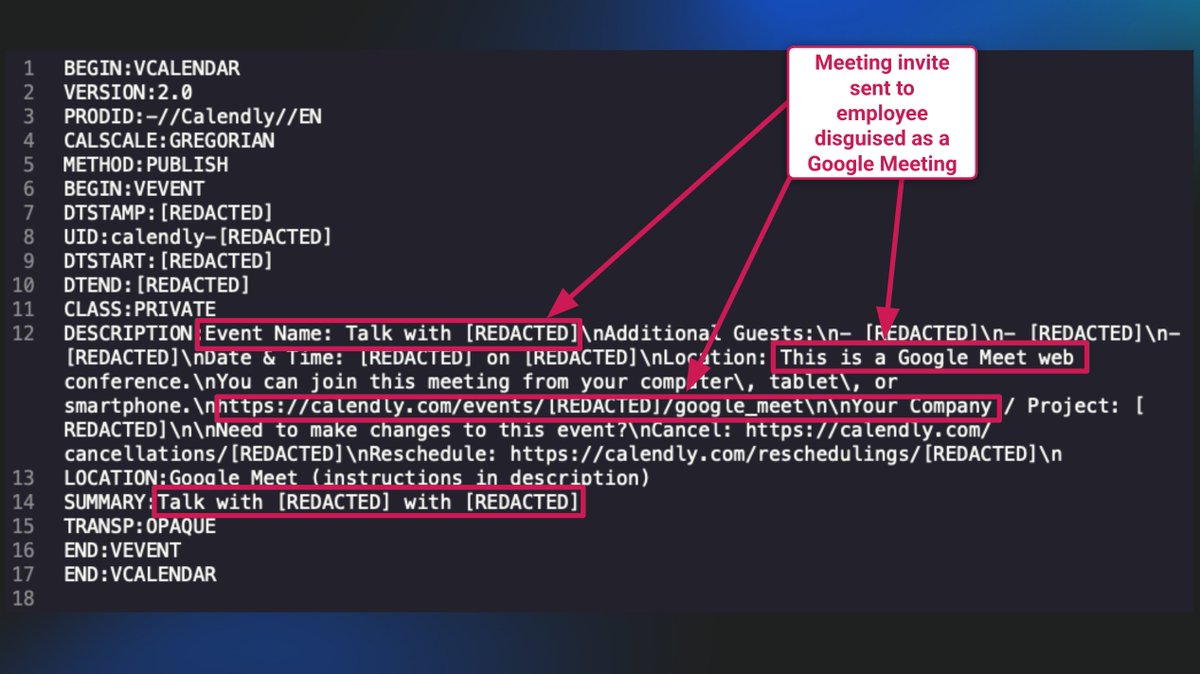
Initial access started with social engineering: 📱 Telegram DM 📆 Fake Calendly invite 🎭 Deepfake Zoom call 🧵 “The threat actor impersonated senior leadership and convinced the victim to install a malicious Zoom extension.” —Stuart Ashenbrenner 🇺🇸 🇨🇦


Related to the write-up that Moonlock Lab published recently. Another handful of stealers that are fully code signed and notarized. IOCs (DMGs) - 672f9b63a2c00a1376ab22589c05d8f7aef19a1dfc50cc6ea66d75aa741793d6 - b62dc580707d0d968c7070a05b04ca7ec61d5ad14333df1c4f327f3c0e6ed3fb



Jamf Threat Labs uncovered a new variant of the Odyssey Infostealer — signed and notarized at the time of discovery. This variant includes backdoor functionality and techniques that align with recent Atomic Stealer research by Moonlock Lab. More here: jamf.com/blog/signed-an…

im so pumped to be talking through some fun north korean malware with Stuart Ashenbrenner 🇺🇸 🇨🇦 at #OBTS v8 🤠 it's truly a goated lineup and i'm very humbled to be speaking along side so many sick researchers (also dw i will be dressed up in a blues clues onesie for the talk)



With "The Art of Mac Malware" Vol II now out, I’ve integrated its content into my #OBTS training: "The Art of Mac Malware: Detection & Analysis" 🍎🐛🔬 So if you want to learn the tools & techniques to uncover & analyze the latest macOS threats, sign up! objectivebythesea.org/v8/taomm.html
![Raaz (@solostalking) on Twitter photo Found multiple #Clickfix domains connecting to odyssey1[.]to:3333 AMOS Malware
45[.144.233.192
83[.222.190.250
185.39.206.183
appmacosx[.com
financementure[.com
appsmacosx[.com
macosxapp[.com
macosapp-apple[.com
macapps-apple[.com
macapp-apple[.com
republicasiamedia[.com Found multiple #Clickfix domains connecting to odyssey1[.]to:3333 AMOS Malware
45[.144.233.192
83[.222.190.250
185.39.206.183
appmacosx[.com
financementure[.com
appsmacosx[.com
macosxapp[.com
macosapp-apple[.com
macapps-apple[.com
macapp-apple[.com
republicasiamedia[.com](https://pbs.twimg.com/media/GswzdR1XcAAqH5b.jpg)

