Sideway
@sidewayre
Reverse-Engineering, low level stuff and goats. Pwning stuff @Synacktiv
ID: 961963106359496704
https://sideway.re 09-02-2018 14:00:51
140 Tweet
870 Followers
187 Following







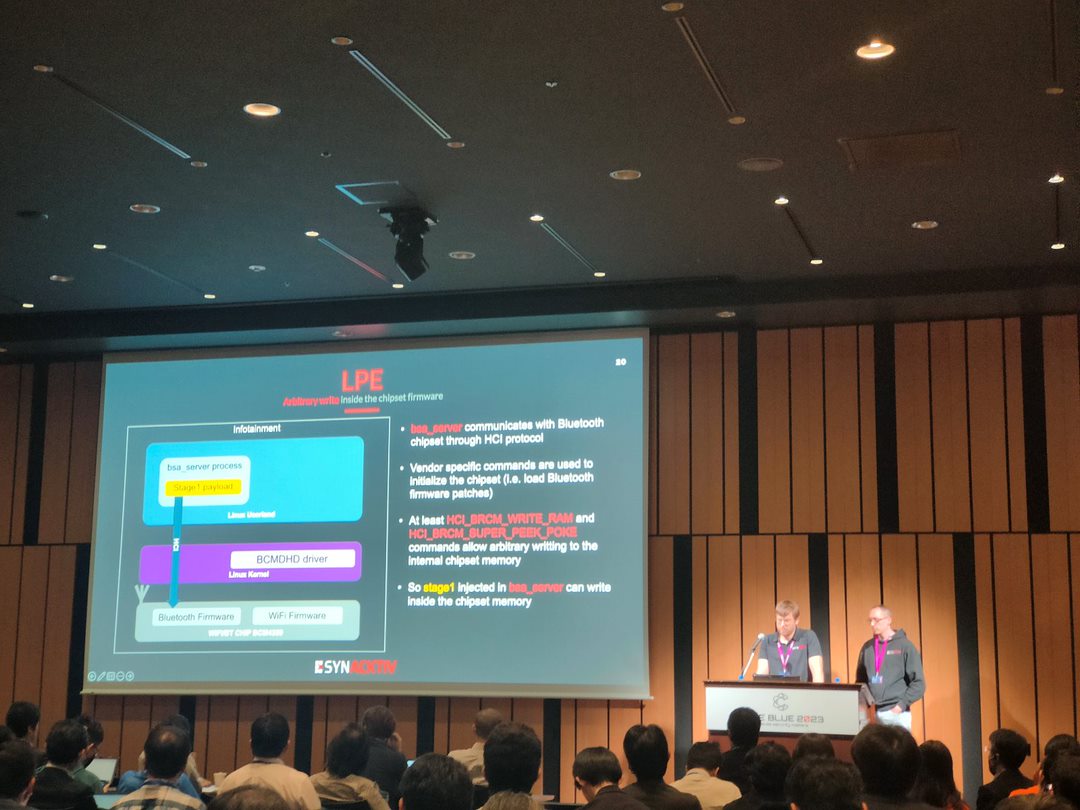
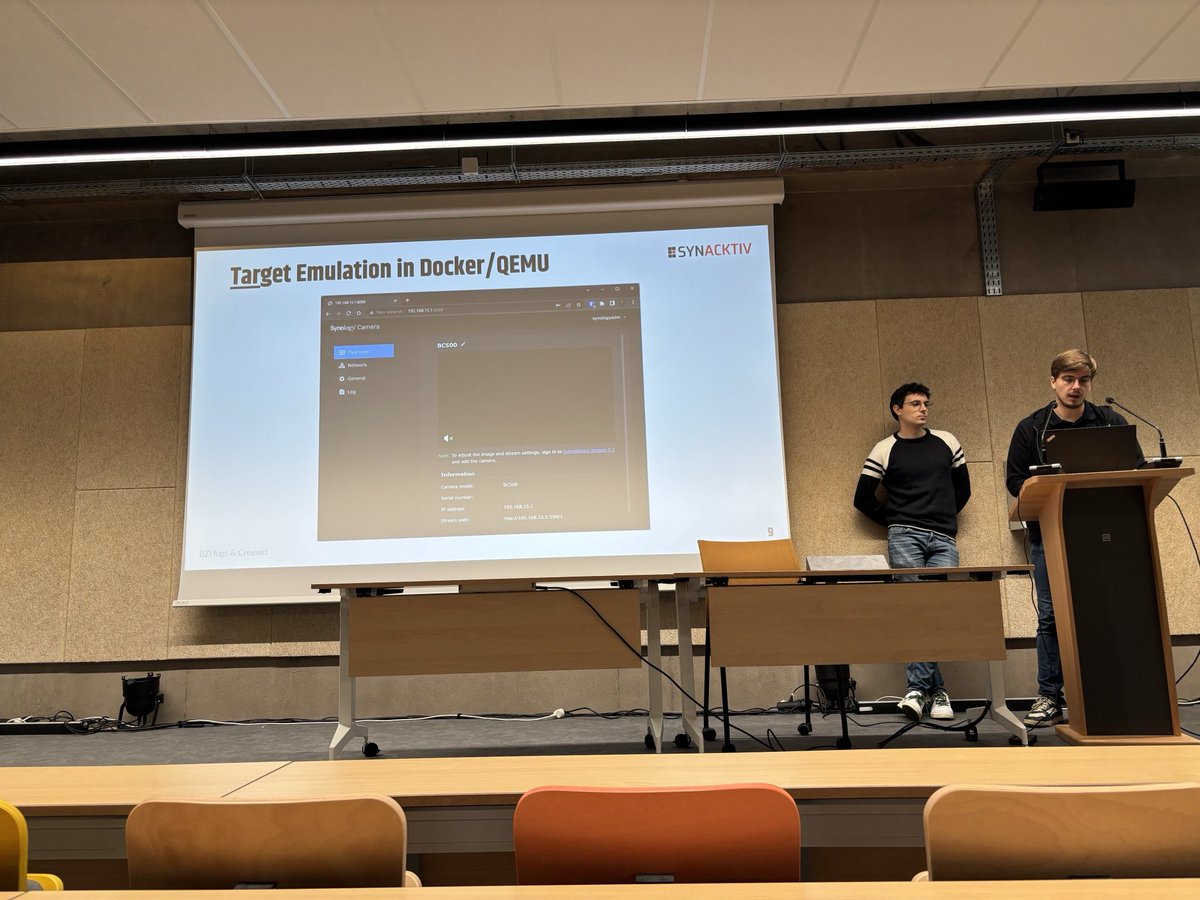
A few months ago, the FreeBSD Foundation appointed us to audit two #FreeBSD critical components: the Bhyve hypervisor and the Capsicum sandboxing framework. Today, related advisories and patches have come out 🧵 1. Multiple vulnerabilities in libnv freebsd.org/security/advis…





Last month Arizona State University I presented my work on formalizing automated bug discovery, developing a framework to characterize the full spectrum of approaches - from fuzzing to human analysis. I'm sharing my evolving perspective on the fundamental nature of the bug finding problem. Full