
Shweta Shinde
@shw3ta_shinde
Assistant Professor at ETH Zurich @CSatETH, Security Researcher.
@[email protected]
ID: 191548401
http://shwetashinde.org 16-09-2010 18:38:43
120 Tweet
1,1K Followers
676 Following





Apr 18 Collegium Helveticum workshop "Real-life impacts of security vulnerabilities" zisc.ethz.ch/events/economi… featuring Daniel Gruss Eduardo Vela Rainer Böhme, Lucas Engl, Sebastian Bonhoeffer Hans Gersbach Anders Fogh Kav & Mark Brands; organized w/Shweta Shinde and Kari Kostiainen
A highly relevant workshop, organized by our Senior Fellow N. Asokan, Associate Fellow Shweta Shinde and Kari Kostiainen.

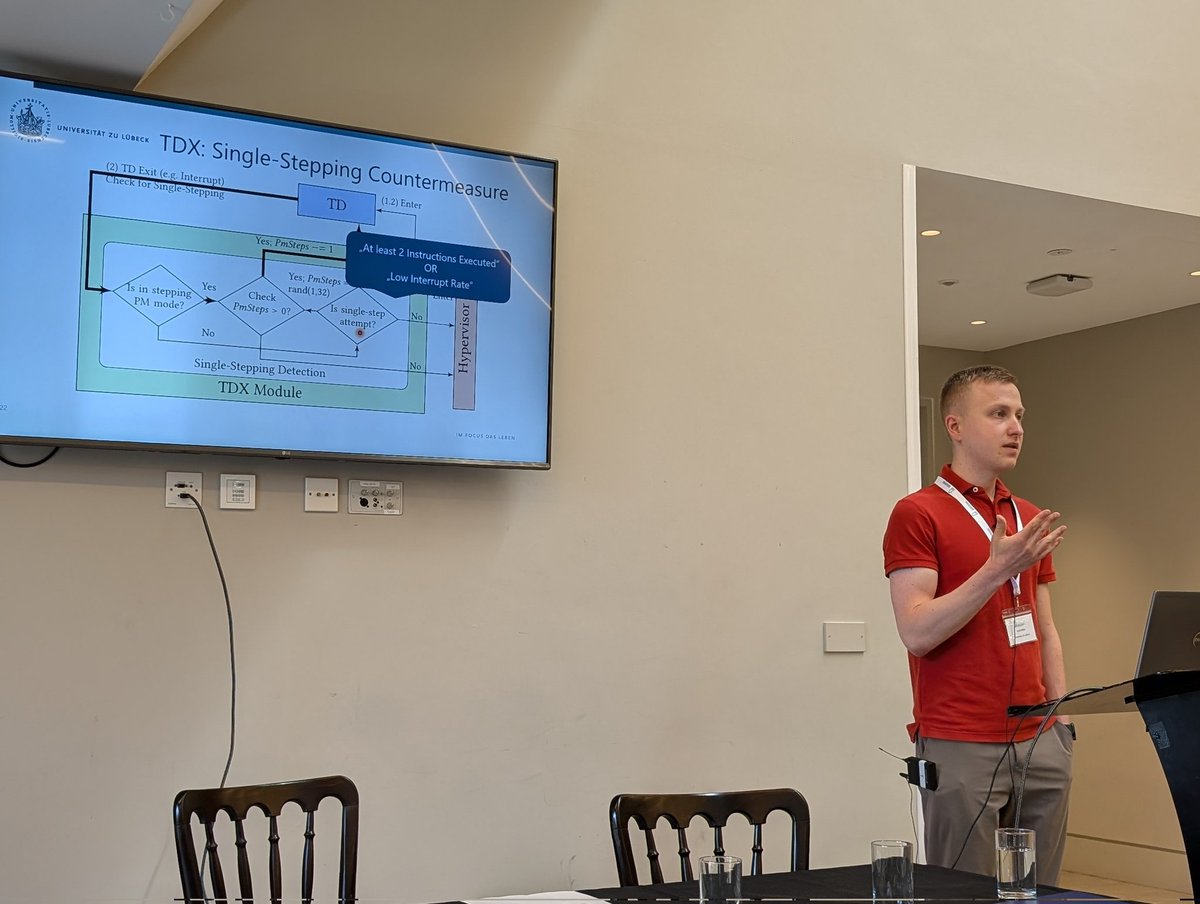
WeSee: Using Malicious #VC Interrupts to Break AMD SEV-SNP got the Distinguished Paper award at IEEE #SP24! Blog & artifacts: ahoi-attacks.github.io/wesee/ Our talk is on May 22, Wed in Track 2, Ballroom 5 @ 1:25 PM #ahoi Congrats Benedict Schlueter Supraja Andrin Bertschi

Excellent talks on the insecurity of Confidential VMs and mitigations against attacks at the UKRISE Summer School by Shweta Shinde ETH Zurich and Luca Wilke.

We will be presenting two papers today at USENIX Security Track 3 Salon E @ 1:30pm Supraja Acai connects Arm CCA confidential VMs to accelerators (eg Nvidia H100) efficiently Benedict Schlueter Heckler, another Ahoi attack, breaks AMD SEV-SNP and Intel TDX with interrupts

📢 We have a faculty opening in ETH CS Department Zurich in Systems for Data Science: ethz.ch/en/the-eth-zur… The position is open-rank (i.e., for an assistant or tenured professor). Feel free to reach out if you have questions. Looking forward to growing the ETH Systems Group! 😃

ETH CS Department (ETH Zurich) is hiring a tenure-track assistant professor in Theory B: Logic, SMT/SAT, decision procedures, theorem proving, semantics, type systems, etc.; please apply by 15 January 2025! More info at: ethz.ch/en/the-eth-zur…


Excited to share our Usenix Security 2025 paper with the #riscv & #ConfidentialComputing community! Zauney will present Dorami: approach to protect RISC-V security monitors in TEEs like keystone-enclave, joint work with Stavros Volos (Azure). Join us! community.riscv.org/events/details…

Another milestone in our vision of sovereign smartphone Outstanding Cybersecurity Contribution award at the Cyber Defence Campus 5-year celebration to our team: Friederike Groschupp Zauney Moritz Schneider Ivan Puddu Srdjan Čapkun Thanks armasuisse for the support & recognition!


It's a great pleasure to co-chair with Anjo Vahldiek-Oberwagner the 8th edition of SysTEX collocated with IEEE European Symposium on Security and Privacy CfP is out: systex-workshop.github.io/2025/cfp.html Deadline: February 20th, 2025 We welcome contributions on the broad spectrum of TEEs. Spread the word and see you all in Venice!

No public Arm CCA hardware? No problem. Learn how #OpenCCA makes CCA research possible on $250 boards, driving open innovation in confidential computing. #CCSummit #ArmCCA Opaque Systems Andrin Bertschi hubs.la/Q03lqnzd0

SysTEX'25 program is out: systex-workshop.github.io/2025/program.h… Including a keynote from Shweta Shinde Shweta Shinde , tools to enable CCA research, symbolic validation of enclaves, ML provenance, evaluating trust in TEEs, and many additional topics. Look forward to see you all in Venice!

#SysTEX wrapped up. Thanks to Marios Kogias for making co-chairing fun. Thanks to all the authors, or keynote speaker Shweta Shinde and participants. Great to see this friendly community advancing an important security technology for the next years.

🔓 Heracles ACM CCS 2025'25: Breaking AMD’s Confidential Computing! We show that the hypervisor can read and move hardware-encrypted memory on AMD SEV-SNP. We build a chosen-plaintext oracle to leak kernel memory, auth keys, and cookies from "confidential" VMs heracles-attack.github.io

🚨Breaking AMD’s Confidential Computing (again!) — Meet RMPocalypse 🚨 Thrilled to share our 2nd paper at ACM CCS 2025 🎉 We break AMD SEV-SNP’s guarantees—with just one write! Forge attestation & enable debug, with 100% success 👥Work with Benedict Schlueter 📄rmpocalypse.github.io