Mr Anon
@shieldifyanon
Founder of @ShieldifySec🛡️Blockchain security audits. Your security partner, for the long term. We have audited Lido, IPOR, Colb, Ion, Kroma, Pear and more.
ID: 1639613128701779969
https://shieldify.org/ 25-03-2023 13:00:13
1,1K Tweet
5,5K Followers
478 Following

To uphold the highest security standards as we scale, we've onboarded Shieldify Security as one of our Security Partners. Together, we're ensuring Multipli stays secure, transparent, and resilient for every Multiplier out there.


New security partnership, this time for Multipli.fi 🤝 With close to $80M in TVL, they're growing fast. We're now their security partners, protecting their journey toward success. Thank you for your trust! 🫡






New Bera security partnership, this time is for Jiko (by Beraji) powered by Beraji 🐻⛓️ 🐻 🤝 Thank you for your trust! 🦾




New audited protocol, this time is for Harmonix Finance from the Hyperliquid ecosystem 🤝 Read the report below👇 github.com/shieldify-secu…


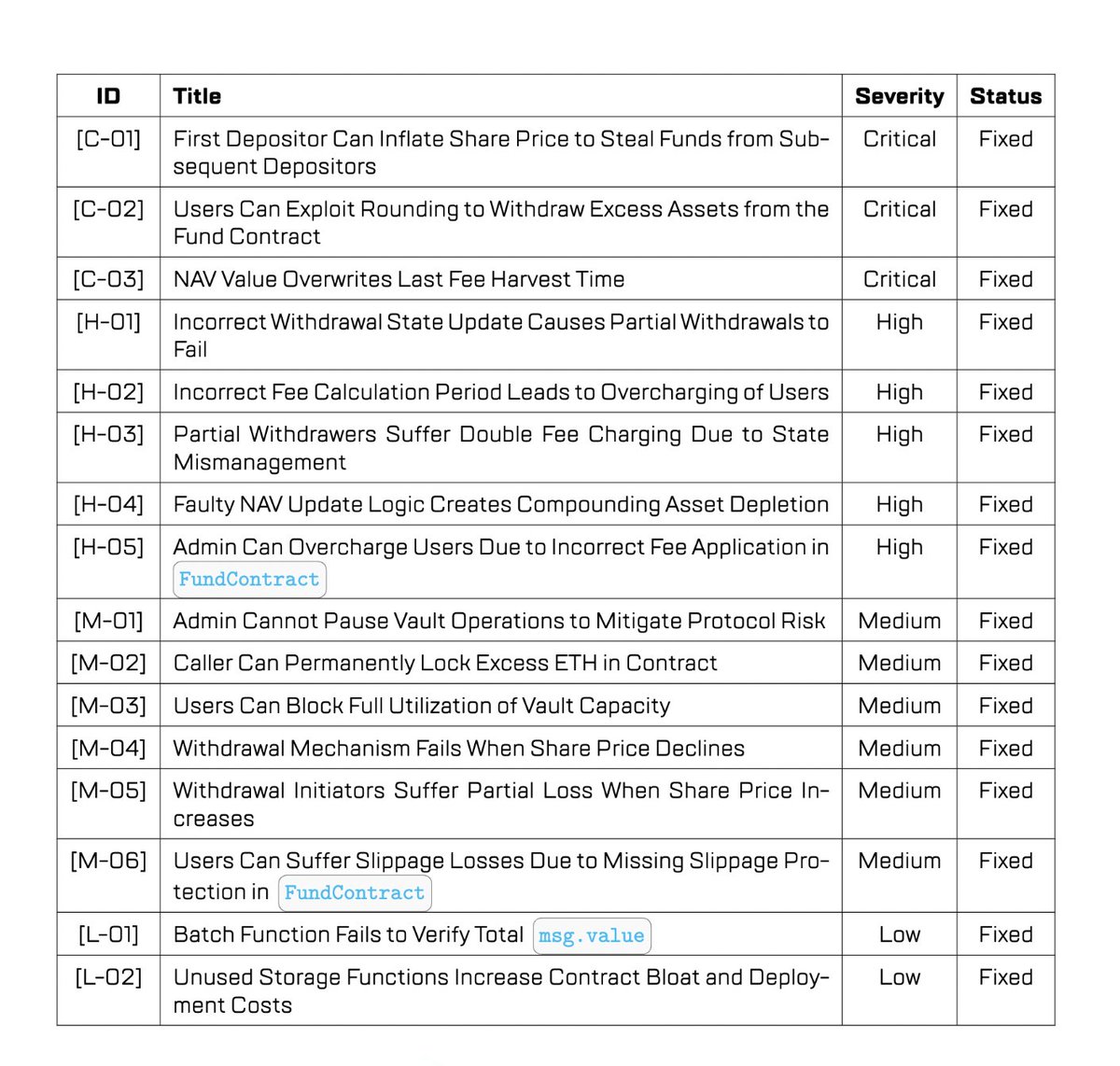
Shieldify Security — Our Auditor #2 of 5 on our 2024-26 Security Roadmap - 2 senior experts, 80 hrs over 5 days reviewed every line of our Hyperliquid vaults, - 16 issues found, all patched pre-launch Here is how your funds get one more layer of safety 👇



13/16 Harmonix Finance partners with Shieldify Security, becoming the second auditor in the 2024-26 security roadmap. Two senior experts spent 80 hours across 5 days reviewing the entire Hyperliquid vault codebase. 16 issues were discovered and all were patched before launch. One more





You can check our audit report for Harmonix Finance with a 16 findings, of which 8 are Critical/High, 6 are Medium and 2 are Low 🫡 Report link: github.com/shieldify-secu…