SecHawk
@sec_hawk
InfoSec | Bug Hunter | Entrepreneur | Futurist •••
Scroll my feed for 1337+ #InfoSec resources 💎 Building @ZSecurityHQ #DataPrivacyActivist
ID: 1387275552101257221
28-04-2021 05:20:49
3,3K Tweet
1,1K Followers
2,2K Following






30 Blogs to Learn 30 System Design Concepts: 1. APIs: blog.algomaster.io/p/whats-an-api 2. JWTs: blog.algomaster.io/p/json-web-tok… 3. Webhooks: blog.algomaster.io/p/what-are-web… 4. API Gateways: blog.algomaster.io/p/what-is-an-a… 5. Load Balancing: blog.algomaster.io/p/load-balanci… 6. Proxy vs Reverse Proxy:






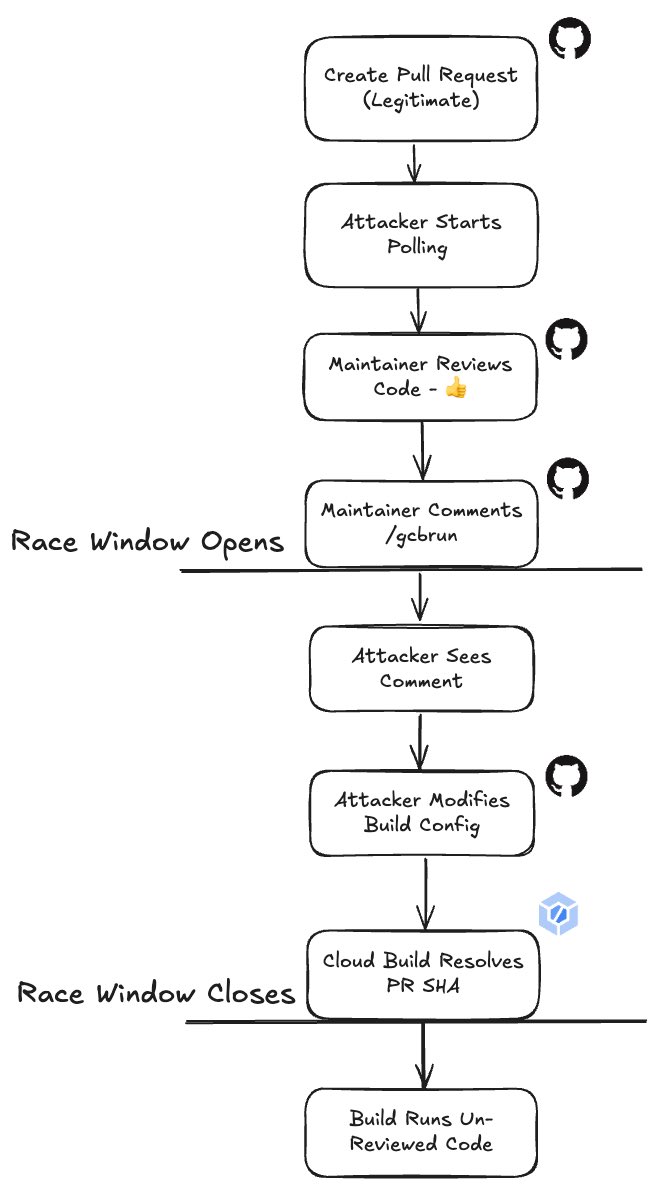
Who's SHA is it Anyway: Bypassing Google Cloud Build Comment Control for $30,000 by Adnan Khan adnanthekhan.com/posts/cloud-bu…