Ru Campbell
@rucam365
Microsoft Security MVP • Dad, metal, lifting, wrestling, cars • Author, Mastering Microsoft 365 Defender • https://t.co/CaVgOm8IvJ • @Threatscape • @M365SandCUG
ID:3113942740
https://campbell.scot 25-03-2015 08:33:42
6,0K Tweets
6,0K Followers
1,3K Following
Follow People





Hosting the M365 Security & Compliance User Group next week. Online only, on recordings.
Hope you can join us for two deep dive sessions with Eric Woodruff | MVP | CIDPRO on SAML and Denis Isakov on AD security.
Register: meetup.com/m365sandcug/ev…



Wondering why use this instead of the WDAC Wizard?
Here is the comparison👇
github.com/HotCakeX/Harde…
Jordan Geurten would love to know your thoughts about this 😊








Just over 1 week to go until some cracking content from Dan Gough and Viktor Hedberg 🛡💻 🔥🔥Don't forget to sign up or you'll miss out on the content and the refreshments from Patch My PC 🔥🔥




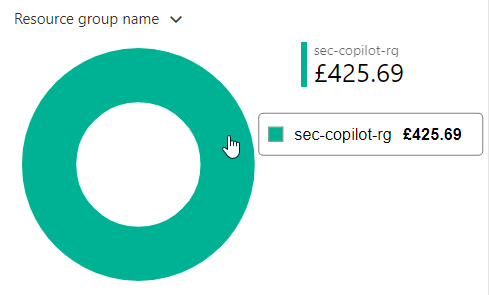
Great fun joining Zoe 💃🏼MVP & RD #CopilotConnection #VivaExplorer and Kevin McDonnell #CollabSummit on Copilot Connection to talk about Copilot for Security.
Covered use cases, experience so far, cost-benefit, separating hype from reality, and optimism about the product's future.
Catch it here: youtube.com/watch?v=YxDFsn…