Soumyani1
@reveng007
Content absorber | CRTP | @BlackHatEvents Asia, USA, SecTor, Europe 2024 Arsenal and @WWHackinFest 2024 Presenter
ID: 1288758525896740864
https://reveng007.github.io 30-07-2020 08:49:31
2,2K Tweet
1,1K Takipçi
1,1K Takip Edilen



AdminSDHolder prevents Account Operators from directly controlling Tier Zero. But most orgs grant Tier Zero privileges to unprotected principals. Jonas Bülow Knudsen explores an attack technique & path from Account Operators → Domain Admin in stock AD forests. ghst.ly/4niCixR






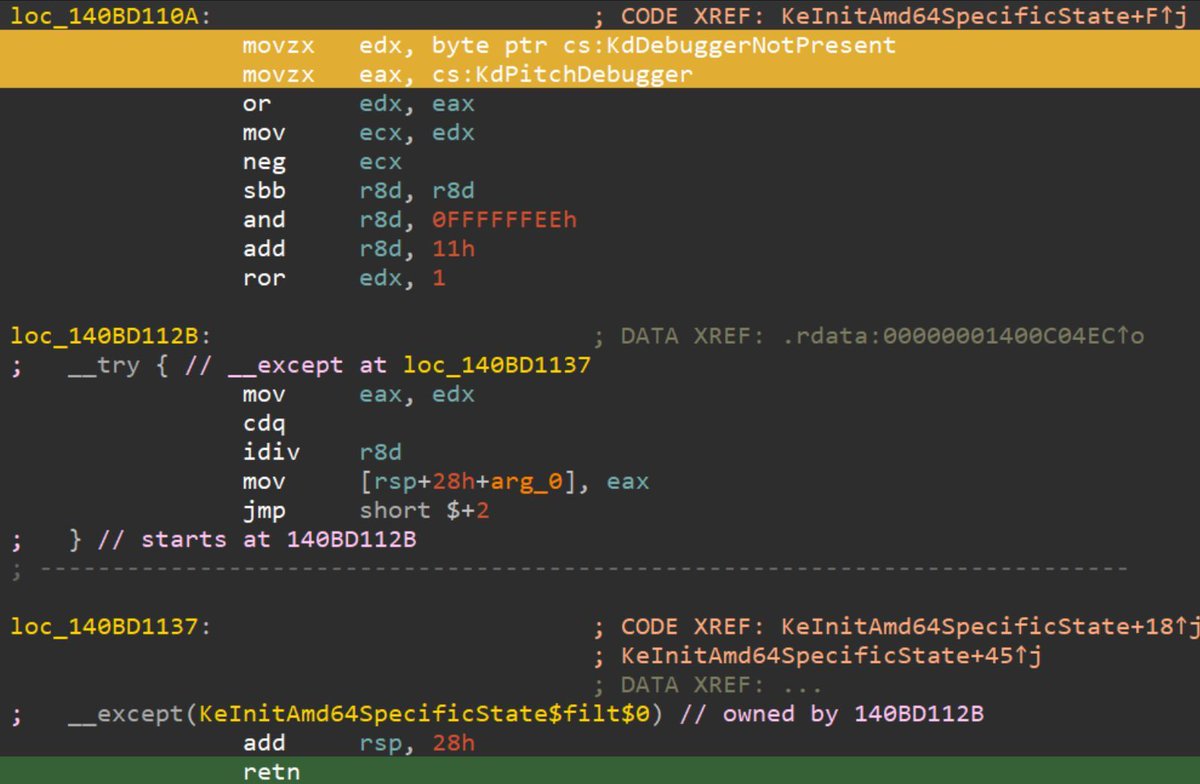
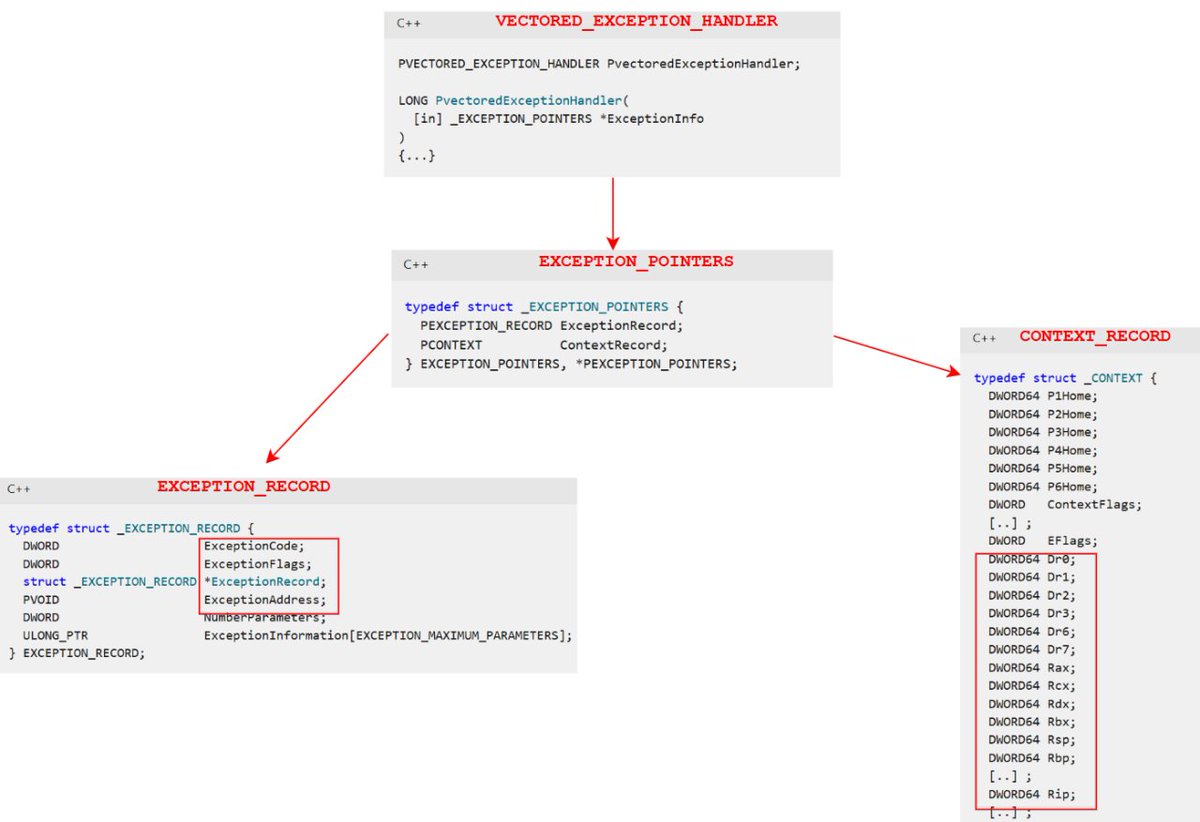
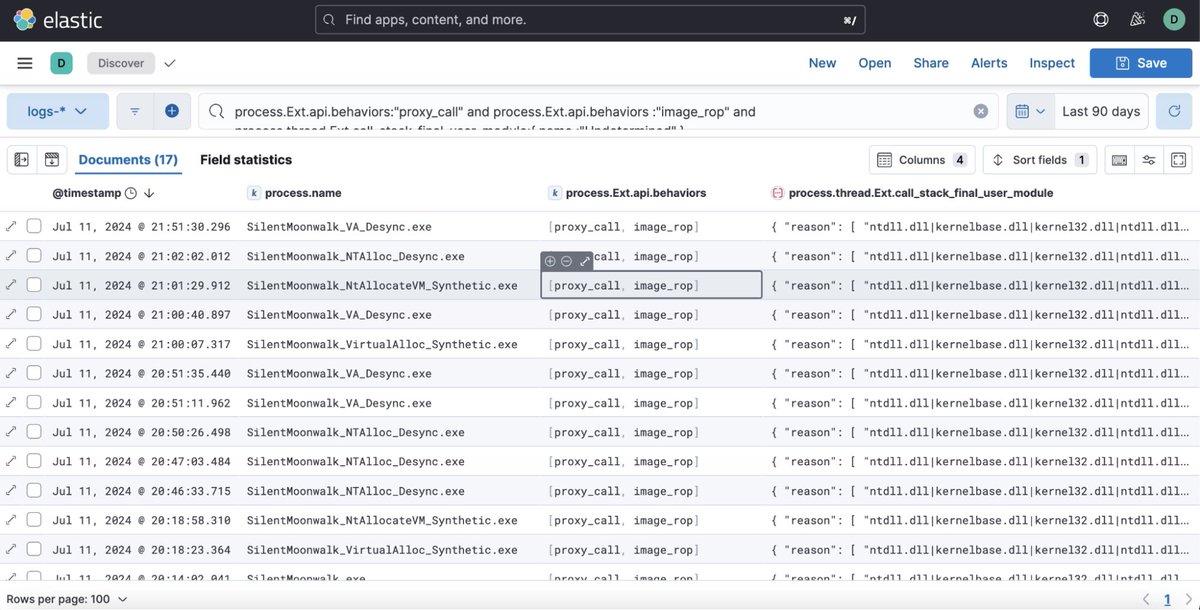
An increased visibility into threads' call stacks helps with more reliable malware detection. The approach is based on ETW telemetry and module's Export Directory data for information enrichment. A post by John Uhlmann of Elastic Security Labs. Great read! #redteam #blueteam #maldev




Awesome talk from Roberto Rodriguez 🇵🇪 on AI Agents... this for me is the immediate future of LLM's and it's so exciting! youtube.com/watch?v=zoAPS1…