ö
@r0keb
low level enthusiast
ID: 1664055744457592839
https://r0keb.github.io 31-05-2023 23:46:32
89 Tweet
43 Followers
105 Following

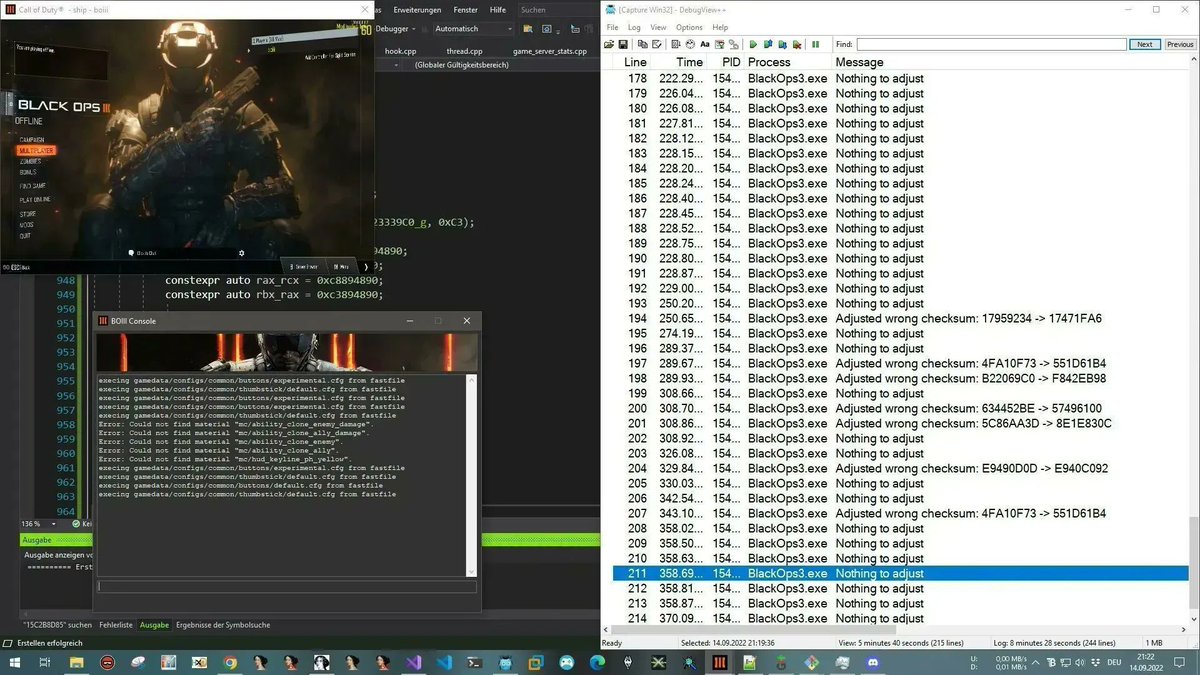
Reverse engineering of runtime code integrity protection in Call of Duty: Black Ops 3 momo5502.com/posts/2022-11-… Credits: Maurice Heumann #reverseengineering





I created a hypervisor-based emulator for Windows x64 binaries. This project uses Windows Hypervisor Platform to build a virtualized user-mode environment, allowing syscalls and memory accesses to be logged or intercepted. elastic.co/security-labs/… Project: github.com/x86matthew/Win…