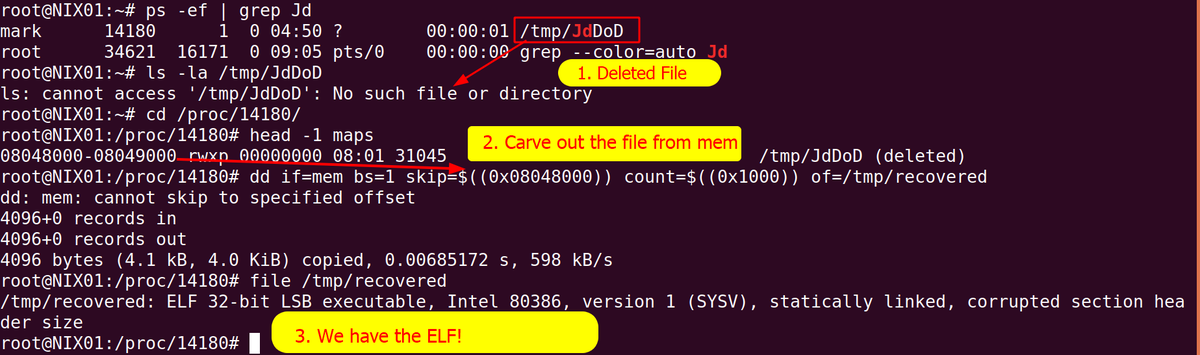
poprbx
@pop_rbx
ID: 1371420806115381251
15-03-2021 11:19:47
15 Tweet
14 Followers
560 Following


Computer hacking advice from superstar RonnieColeman, compliments of Chris Valasek.




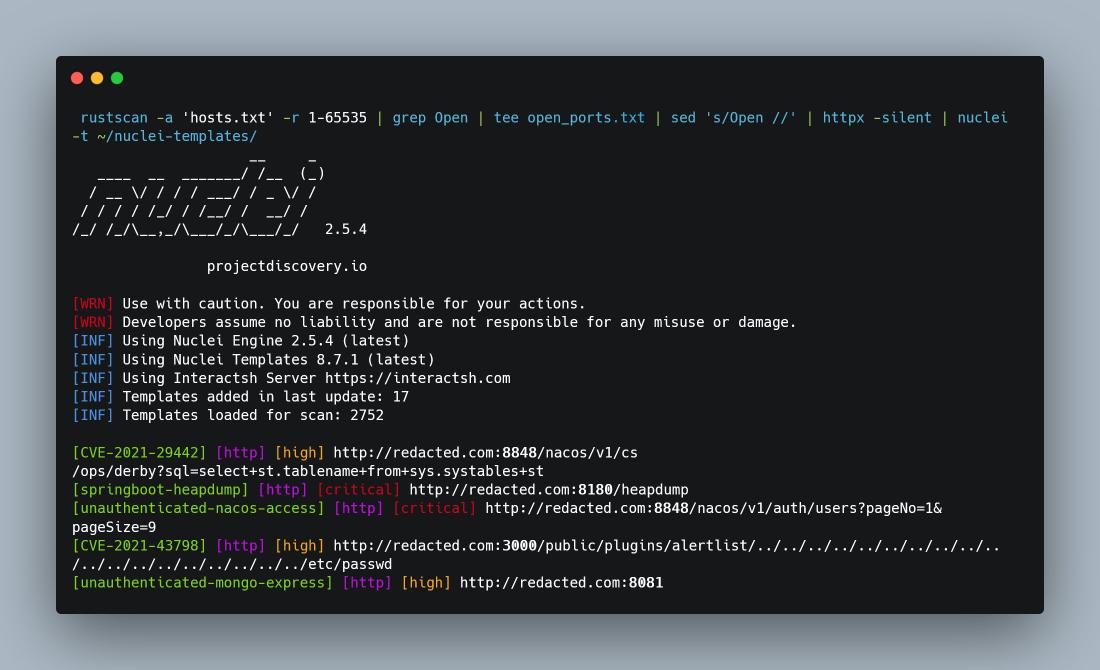
If you collected a bunch of alive IP addresses. Don't run Nuclei by ProjectDiscovery directly on it, Firstly make a Full port scanning then run it, maybe you find some juice stuff on other ports like what I got XD !! The command: carbon.now.sh/?bg=rgba%28171… #bugbountytips #BugBounty #CyberSecurity
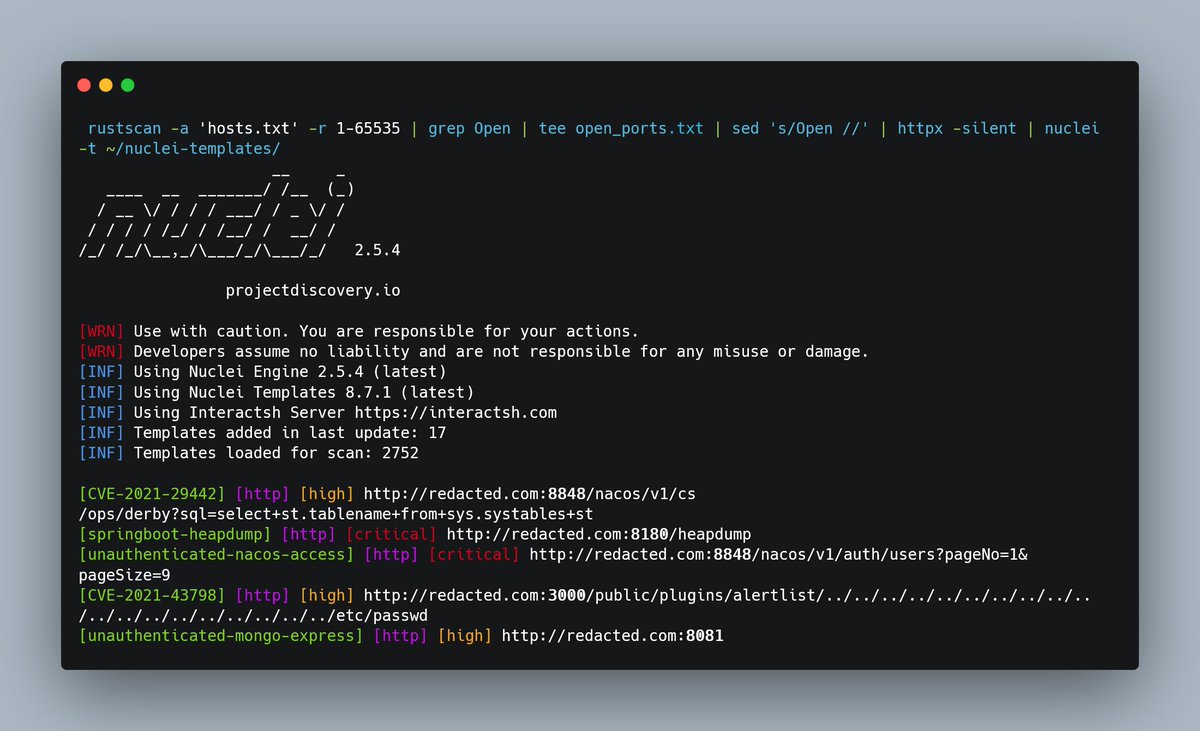

Firstly make a Full port scanning then run it Nuclei by ProjectDiscovery Mahmoud Youssef command: rustscan -a 'hosts.txt' -r 1-65535 | grep Open | tee open_ports.txt | sed 's/Open //' | httpx -silent | nuclei -t ~/nuclei-templates/ #bugbountytips #BugBounty #CyberSecurity

Bug Bounty Hunting Search Engine - Made by payloadartist 🔗bugbountyhunting.com #bugbounty #cybersecurity #infosec






![B:\a.zza (@mcbazza) on Twitter photo Red-Teamers:
[lazy]People like me use Notepad++ as a note-taking thing. We create a 'new', then never get around to saving them.
They get cached here:
C:\Users\{username}\AppData\Roaming\Notepad++\backup
If you hit a dev/sysadmin, you'll find all kinds of crazy stuff. Red-Teamers:
[lazy]People like me use Notepad++ as a note-taking thing. We create a 'new', then never get around to saving them.
They get cached here:
C:\Users\{username}\AppData\Roaming\Notepad++\backup
If you hit a dev/sysadmin, you'll find all kinds of crazy stuff.](https://pbs.twimg.com/media/FDbIXuMXEAAfmBr.png)