PhD. Phuc
@phd_phuc
Malware Researcher @TrellixArc. Former: @CNRS @EMSEC35 @ThreatFabric Mac-A-Mal. AHMA. ULTRA.
ID: 54639955
http://babyphd.net 07-07-2009 18:52:19
4,4K Tweet
1,1K Followers
810 Following

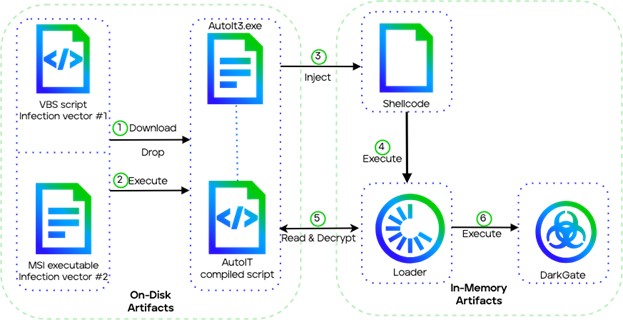
Check out the latest research of Trellix Advanced Research Center in which I took part. The blog deeps dive in the many differences of DarkGate latest versions. trellix.com/about/newsroom…




New research from our team Trellix Advanced Research Center & Northwave. Intelligent Security Operations. expose RansomHouse's TTP. Group demanded $2.56M from a victim, negotiated down to $1.25M. Payment tracked on blockchain. RansomHouse "advised" victim to adopt zero trust, 2FA, update systems etc.




Iranian threat groups, such as APT35, MuddyWater, and more, continue to intensify activities targeting critical sectors and interfering with U.S. elections. Ernesto Fernández, PhD. Phuc, and John Fokker with Trellix Advanced Research Center provide an overview. bit.ly/4deoSws



Insightful research into macOS malware trends & growth in the context of the enterprise! 🤗 (And do appreciate the many citations to Objective-See Foundation blog posts! 🥰)




🚨 New APT uncovered! 🚨 Trellix Advanced Research Center reveals #OneClik, targeting energy, oil, & gas via #phishing & Microsoft #ClickOnce. Stealthy "living off the land" tactics make it tough to detect. Full details here: bit.ly/4kYFblU