Mobile Security Researcher @starlabs_sg
ID: 863769508967727106
https://github.com/Peterpan0927 14-05-2017 14:54:33
382 Tweet
2,2K Followers
353 Following










After 6 months of responsible disclosure, proud to announce our team discovered 13 (mostly exploitable) vulnerabilities in Samsung Exynos processors! Kudos to Billy, Ramdhan, [email protected] & rainbowpigeon CVE-2025-23095 to CVE-2025-23107 📍 semiconductor.samsung.com/support/qualit…








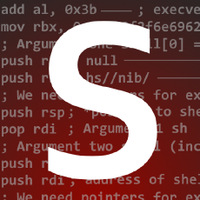
Our newest Dataflow Security blog post is live, thanks to Tomi from Dataflow Forensics for putting this together :-) blog.dfsec.com/ios/2025/10/14…