Perey Bao
@pereybaos
ID: 1788254363108225024
08-05-2024 17:07:30
43 Tweet
5 Followers
199 Following

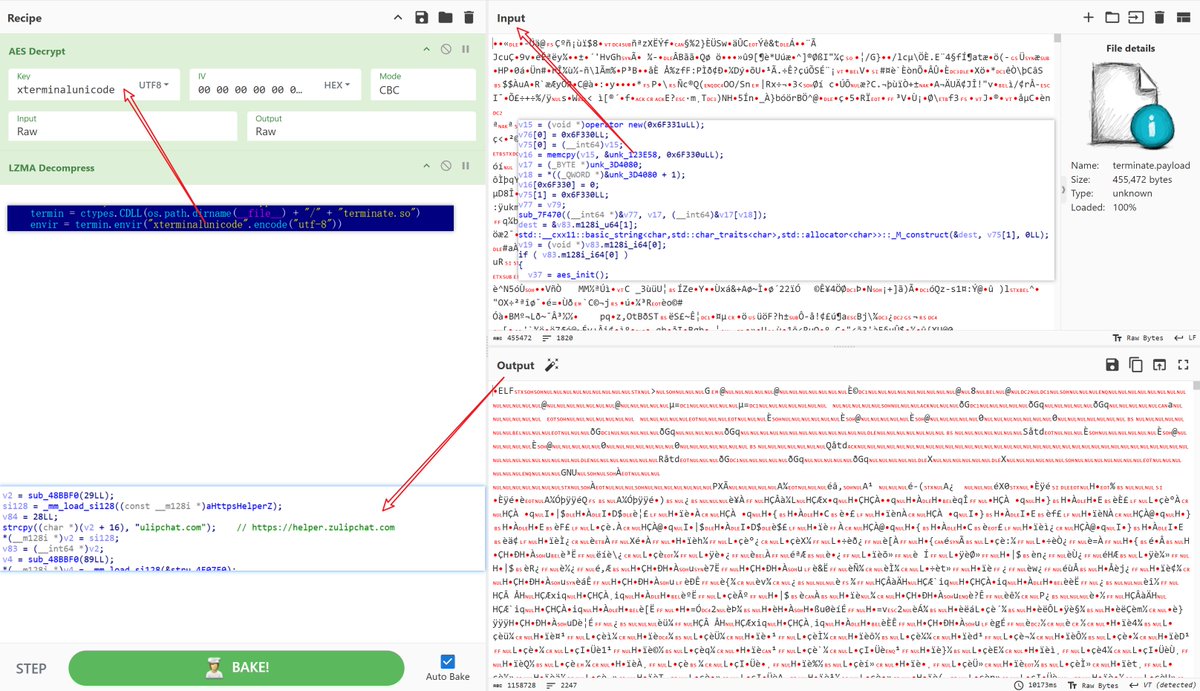
"Credit Card Frauder.exe": 819190f5d012d3267c1bc6294da9f50060316bb146aacbc61863094959e1afe7 "computer has been seized by the Federal Bureau of Investigation" "We notice also your illegal activity online, to get your files back you must e-mail us at [email protected]" 😂















How do LLMs actually work? LLMs power AI applications like ChatGPT, Grok, and Claude to generate human-like text and assist with complex tasks. Credit to Nikki Siapno #infosec #cybersecurity #cybersecuritytips #CyberSec #networking #infosecurity #cybersecurityawareness