Arnold Osipov
@osipov_ar
Security Researcher @Morphisec | Former - Check Point Research | RE, Malware & Threat hunting | Software Engineer.
ID: 2860316952
17-10-2014 13:21:23
267 Tweet
1,1K Followers
421 Following



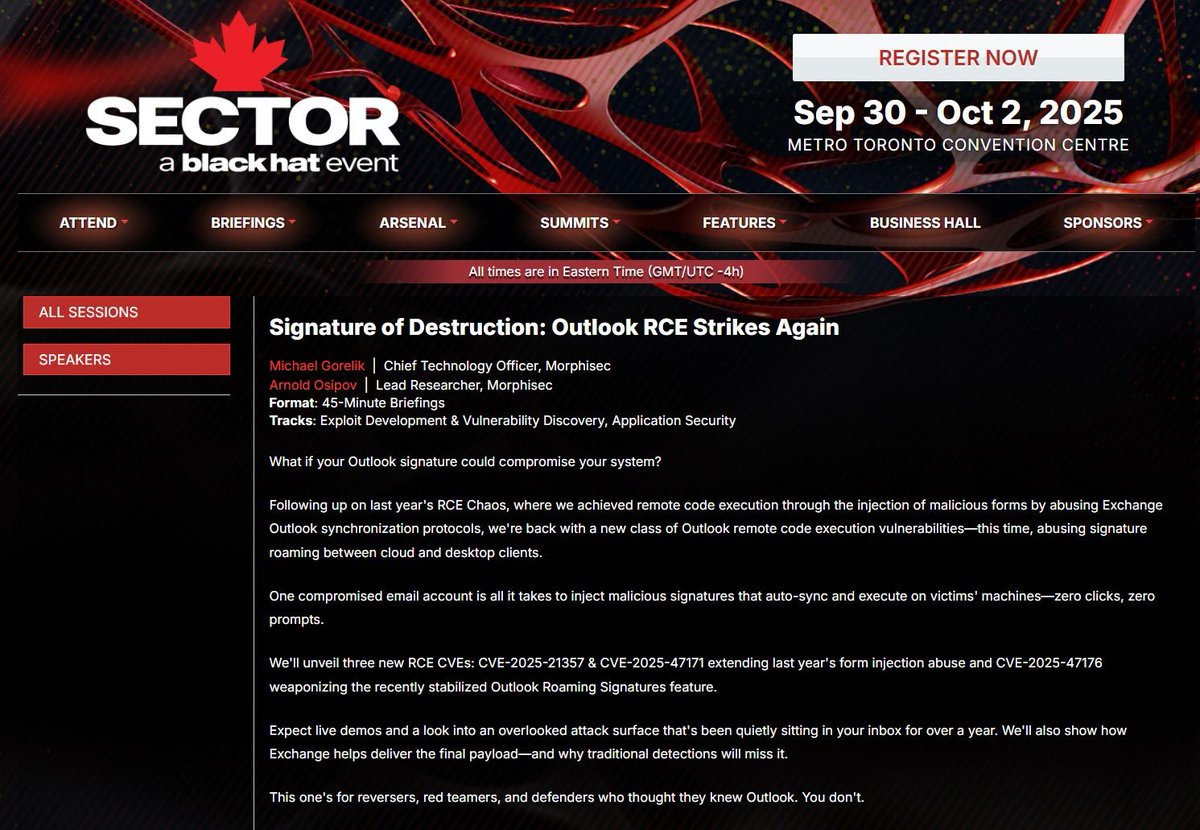
Join me, Arnold Osipov and Shmuel Uzan at #DEFCON32 this year for our presentation, "Outlook Unleashing RCE Chaos: CVE-2024-30103" where we'll share technical details and a POC. We will be revealing additional RCEs once they are patched. You should patch your devices today!



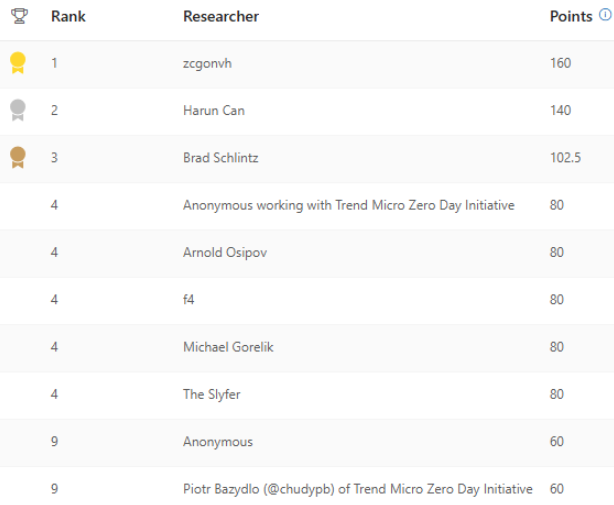
Super excited to get into the Q2 top 10 Office researchers! 🎉 Security Response - Thank you for the opportunity 🙏 #CyberSecurity #Research #Microsoft



📩 Arnold Osipov & Michael.Gorelik have uncovered and aided Microsoft in patching another Outlook vulnerability, CVE-2025-21357. 🔎 See the details in our brand new web experience: bit.ly/40AqTA3 #cybersecurity #outlook #microsoft #cyber #patchtuesday


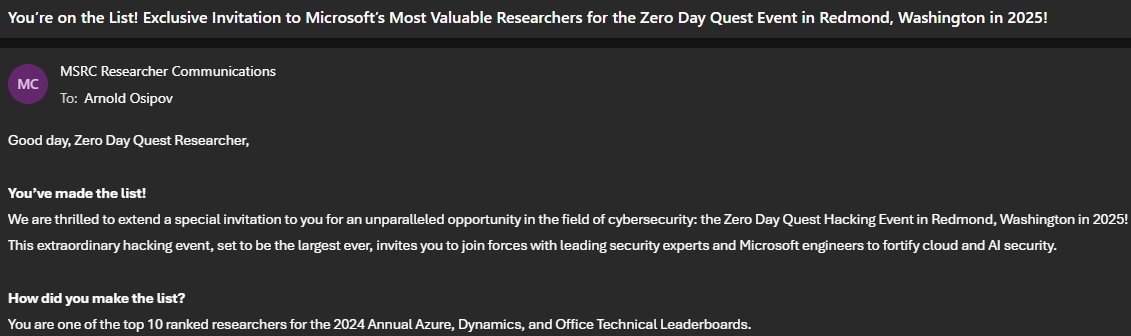
🚀 Thrilled to share that I’ve been invited to Microsoft’s Zero Day Quest event in Redmond, Washington in 2025! 🔥 Over the past year, I’ve reported 4 RCE vulnerabilities and several other security issues to MSRC. Big thanks to Security Response for organizing this unique event!

Having time off from a long exciting day hacking Microsoft products. With Arnold Osipov and Shmuel Uzan at #ZeroDayQuest Security Response





Day 2 of #ZeroDayQuest brought together brilliant minds from around the world for more hands-on hacking and meaningful community connections. Catch the energy in our recap video! Tom Gallagher Jeremy Tinder Wendy [email protected]