Naacbin
@naacbin
Maldev, forensic and reverse makes me happy.
ID: 1048638572956450816
https://naacbin.gitlab.io/ 06-10-2018 18:18:13
160 Tweet
164 Followers
159 Following

Time to make volatility 3 compatible with modern Windows hibernation file analysis. Blog post : forensicxlab.com/posts/hibernat… Feature : tinyurl.com/5n8u4nr9 Special thanks to Chad Tilbury who gave me the motivation and Joe Sylve 🐘 @[email protected], Vico Marziale, Golden G. Richard III for the incredible work











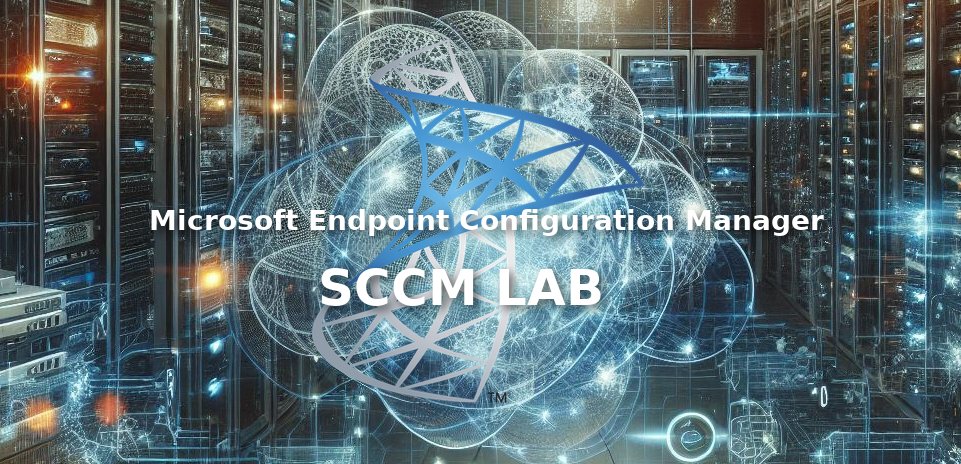
New lab 🏰 for the GOAD project 🥳: SCCM You can now test the SCCM/MECM attacks locally on Virtualbox or Vmware. More information here: mayfly277.github.io/posts/SCCM-LAB… Repository here : github.com/Orange-Cyberde… Thx again Kenji Endo for your help to building this !

Exciting news: VolWeb 2.0 is out! This digital forensics memory analysis platform leverages the capabilities of volatility 3 framework. With significant enhancements, it now offers improved flexibility and scalability! github.com/k1nd0ne/VolWeb. 1/8