n00py
@n00py1
Retweeter of InfoSec/Offsec/Pentest/Red Team. Occasional blogger/Independent security research.
ID: 3094485998
https://www.n00py.io/ 17-03-2015 20:12:21
6,6K Tweet
13,13K Followers
963 Following





The original BadSuccessor research by Yuval Gordon was too good to ignore, I couldn't wait to replicate it in my lab. I wrote a short post on operationalizing the technique with real-world, stealthy abuse paths. medium.com/p/429cefc36187

I'm super happy to announce an operationally weaponized version of Yuval Gordon's BadSuccessor in .NET format! With a minimum of "CreateChild" privileges over any OU it allows for automatic escalation to Domain Admin (DA). Enjoy your inline .NET execution! github.com/logangoins/Sha…


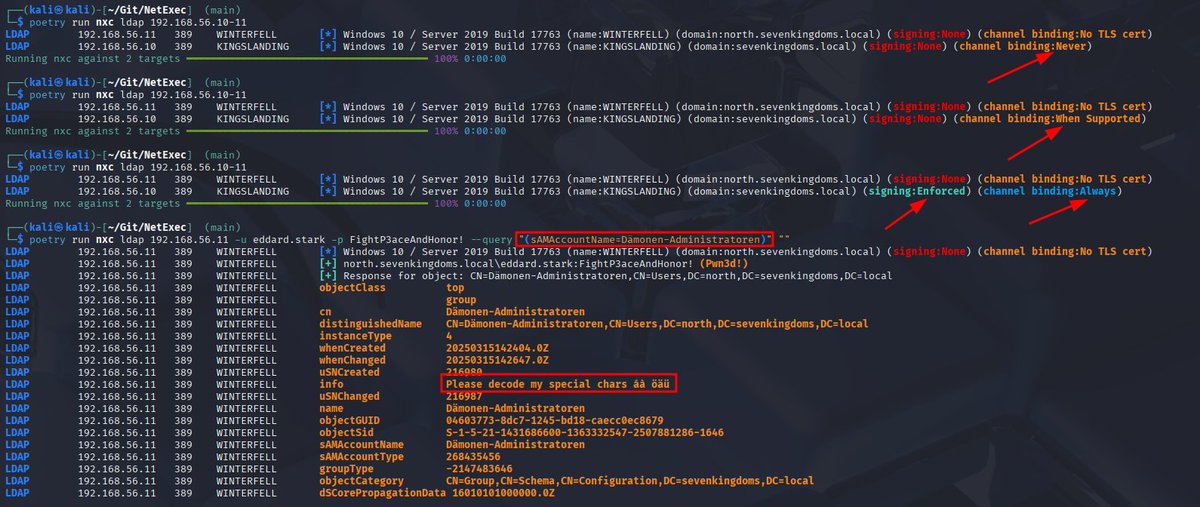
NetExec now has native checks for LDAP signing and channel binding capabilities of the target DC, thanks to the implementation of Thomas Seigneuret 🚀 I also fixed querying LDAP with non-ASCII characters, so you can finally query groups such as "Dämonen-Administratoren"🎉









Introducing the BloodHound Query Library! 📚 Martin Sohn & Joey Dreijer explore the new collection of Cypher queries designed to help BloodHound users to unlock the full potential of the BloodHound platform by creating an open query ecosystem. ghst.ly/4jTgRQQ

#HuntingTipOfTheDay: @OddvarMoe of TrustedSec shows how you can run a full C2 implant from Outlook - just setting a few registry keys does the trick. Any activity concerning these registry keys should be consider suspicious. Full story here: youtu.be/7MDHhavM5GM