Mitja Kolsek
@mkolsek
CEO of ACROS Security; Co-founder of 0patch (0patch.com)
Bluesky: bsky.app/mkolsek.bsky.s…
Mastodon: @[email protected]
ID: 470234530
http://www.acrossecurity.com 21-01-2012 13:30:32
23,23K Tweet
4,4K Followers
665 Following

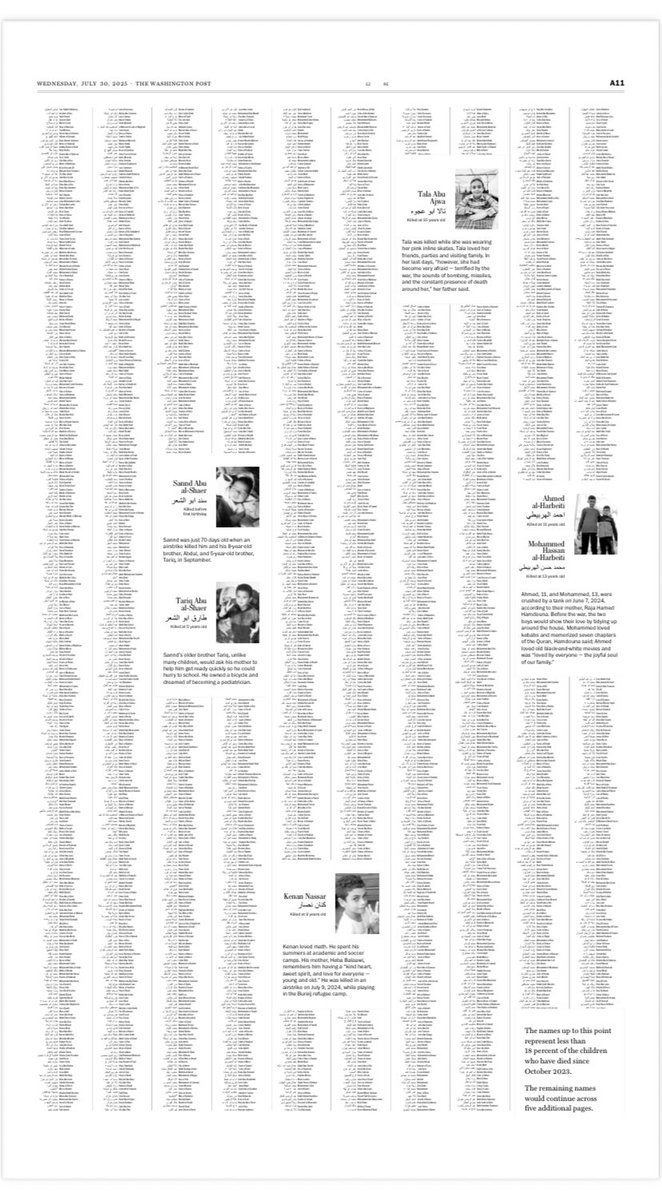
In the The Washington Post today, we have published every one of the 18,500 known names of children killed by Israel’s military operations in Gaza.








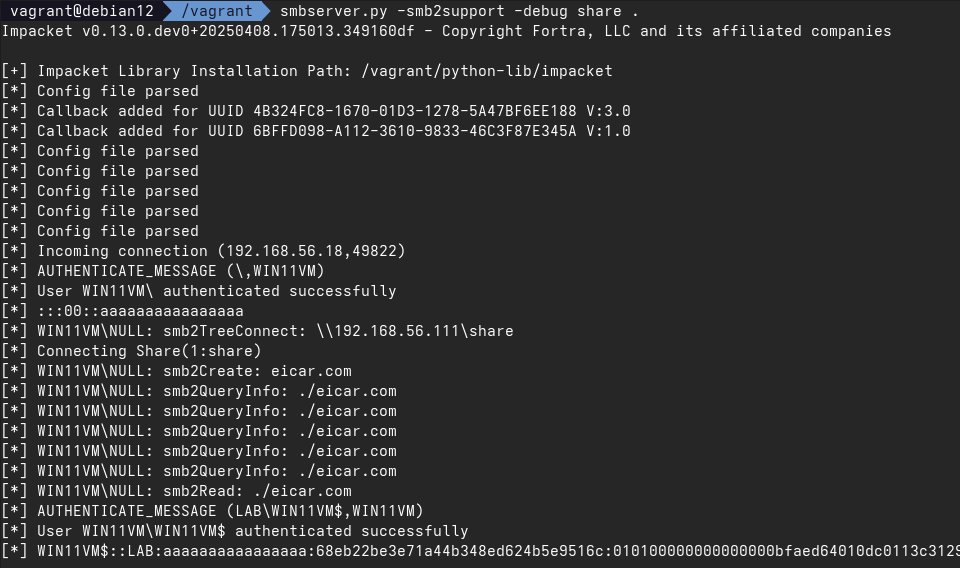
We'd like to thank Filip Dragović (Filip Dragovic). for sharing their finding and their POC, which allowed us to reproduce the issue and create patches for our users.









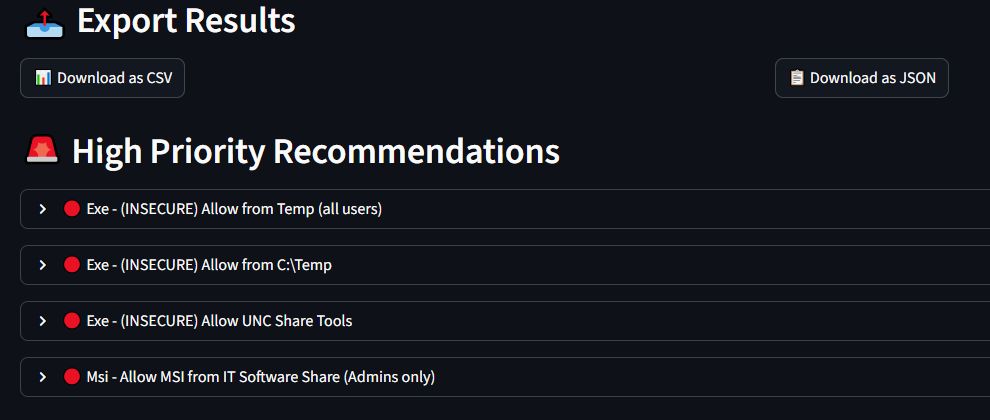
What comes after the patch? Bypass of course! 😜 Delinea Protocol Handler RCE - Return of the MSI. By my colleague Johnny Fishcake blog.amberwolf.com/blog/2025/augu…