Michael Schwarz
@misc0110
InfoSec Faculty @ #CISPA. Side-channel attacks. Exploiting microarchitectures. #Meltdown #Spectre #ZombieLoad #SGX #JavaScript #Rowhammer
ID: 2419140080
https://misc0110.net 30-03-2014 15:16:04
684 Tweet
7,7K Followers
466 Following


Exciting work from my newest PhD Fabian Thomas! He just started at the beginning of the year, and this was his first project in his PhD. If you are Black Hat, don't miss his talk starting in 10 minutes!


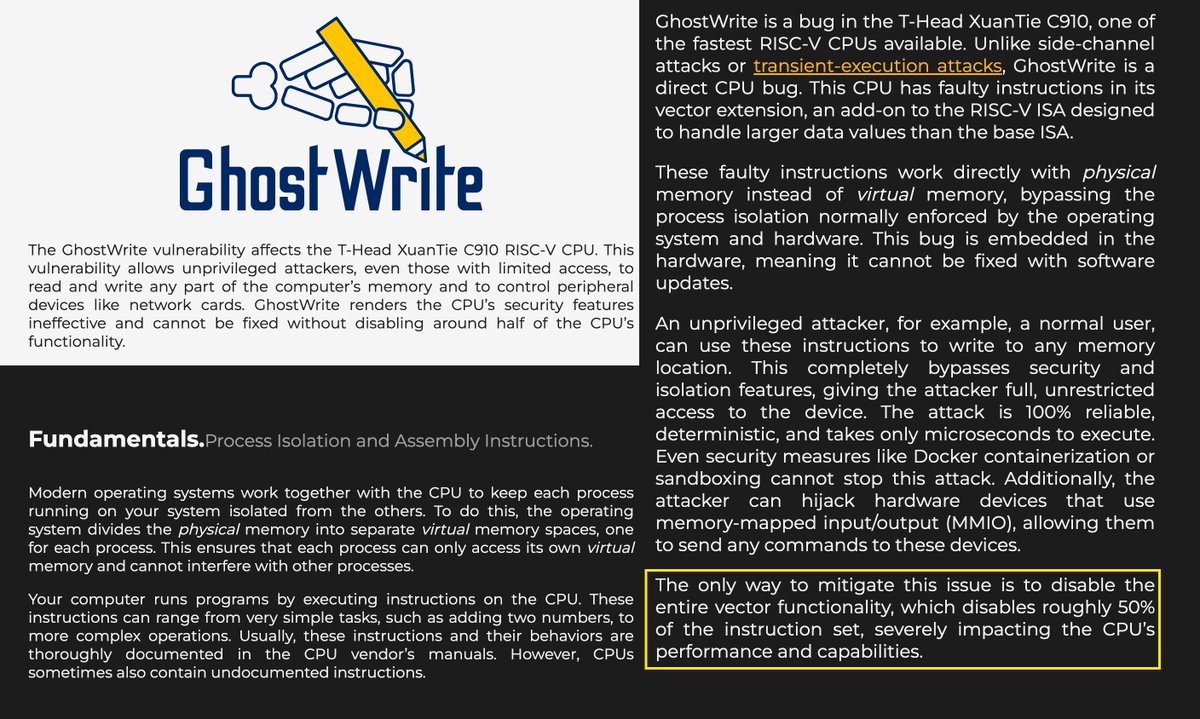
SCMagazine: A pair of researchers told #BHUSA attendees of a vulnerability they uncovered dubbed "GhostWrite," capable of allowing an attacker to pull memory contents from RISC-V International chips. #BlackHat2024 #cybersecurity #infosec #ITsecurity bit.ly/3yklRwx




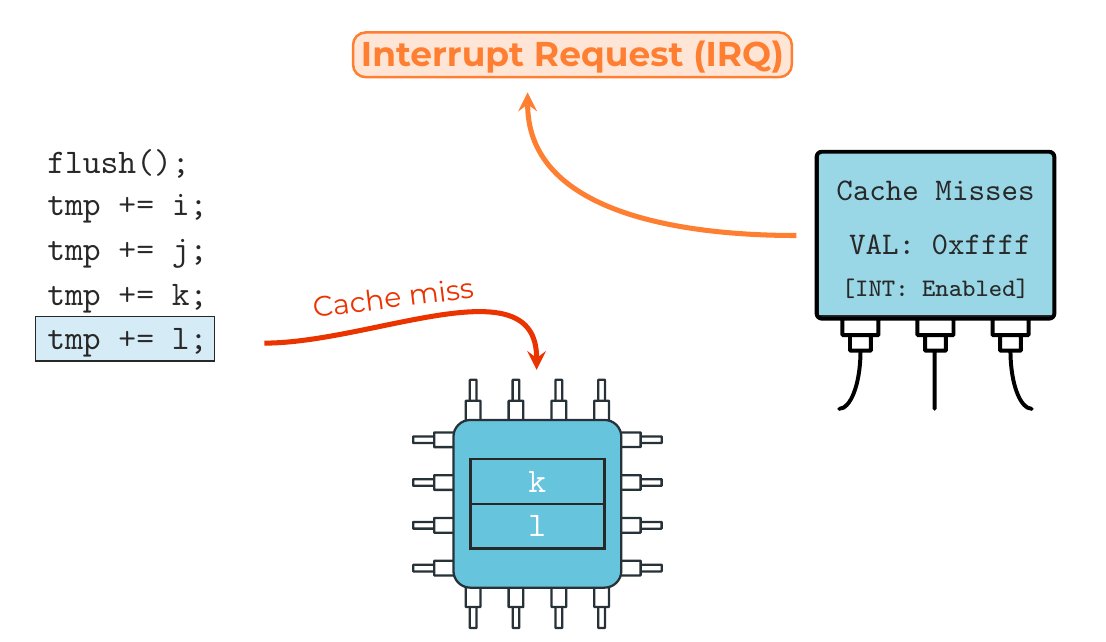
The first #ACSAC2024 #PaperPreview today is by Weber et al., who show that HW features can be used to stop #SideChannel #attacks almost immediately by monitoring the victim: openconf.org/acsac2024/modu… #cybersecurity Daniel Weber @____salmon____ Jan Reineke Michael Schwarz Cispa (degen)
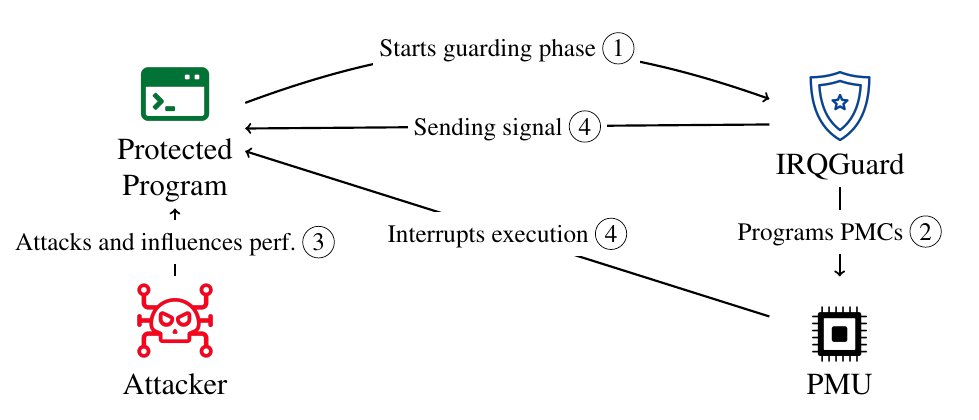


Super excited to present our (L. Niemann, @____salmon____, Jan Reineke, Michael Schwarz) newest paper at #ACSAC2024! We show how modern CPU hardware can be leveraged to stop side-channel attacks almost instantly (~200 CPU cycles)! Code/Paper: github.com/cispa/IRQGuard





Heading to Black Hat Asia now! Leon Trampert and I will give a briefing about deanonymizing users not only on the web but also in their email clients! #BHASIA


✅ Write constant-time crypto code ☠️ Compiler introduces timing side-channels Do Compilers Break Constant-time Guarantees? fc25.ifca.ai/preproceedings… TL;DR: Yes!🥲 👏👏👏Great work Michael Schwarz & team!



Thrilled to present our (Lukas G., Leon Trampert ,Youheng L, Jo Van Bulck ,Michael Schwarz) newest paper ("SCASE: Automated Secret Recovery via Side-Channel-Assisted Symbolic Execution") at #USENIX Security this week! 1/n