📔 Michael Grafnetter
@mgrafnetter
IT Security Researcher and Trainer, Author of the DSInternals PowerShell Module, Microsoft MVP
ID: 3934604253
https://github.com/MichaelGrafnetter/DSInternals 12-10-2015 06:20:25
349 Tweet
2,2K Followers
116 Following

My new blog post on getting plaintext gMSA secrets available at o365blog.com/post/gmsa/ Credits to Sean Metcalf, 📔 Michael Grafnetter, Charlie Bromberg « Shutdown », and Andrew Mayo!




Maybe #mimikatz3 will be signed by Burger King France

Here’s a recap from the CyberGen Conference with our expert 📔 Michael Grafnetter 👀 Michael was there with a workshop on AD security, a panel discussion on emerging trends & mitigation tactics, and a keynote presentation on how to ruin your security with a printer 📠 #CyberGen2025




The DSInternals PowerShell module just got an upgrade! 🔥 Updates include: ✅ Golden dMSA Attack ✅ Full LAPS support ✅ Trust password & BitLocker recovery key extraction ✅ Read-only domain controller database compatibility Read more from 📔 Michael Grafnetter. ghst.ly/412rZ7F







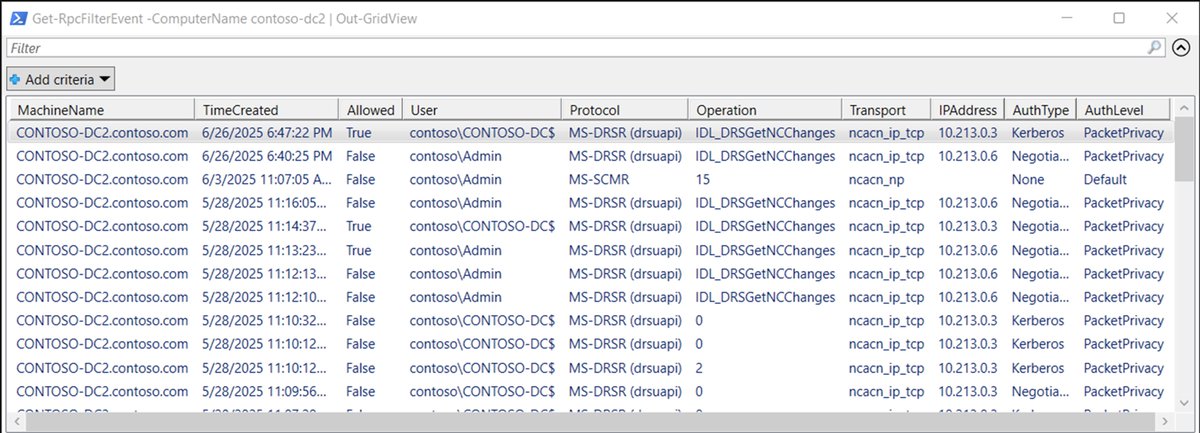
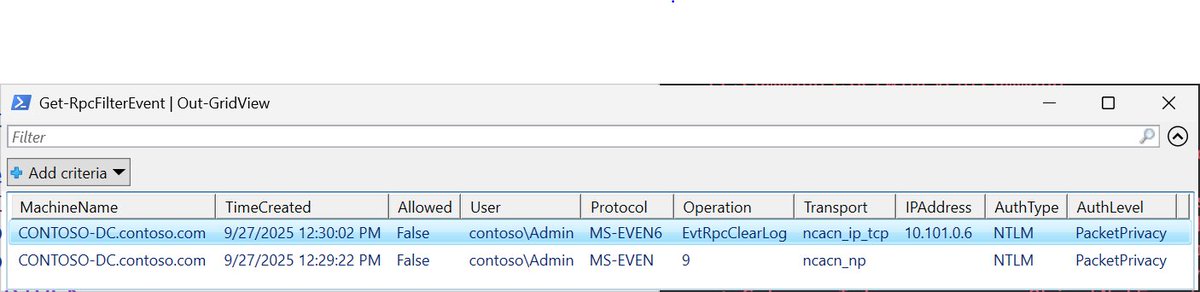
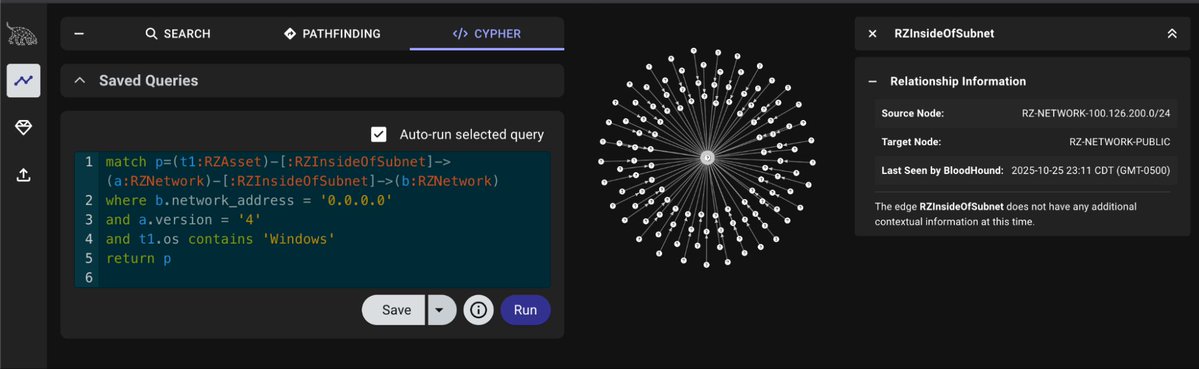
Securing Domain Controllers without breaking AD is harder than it sounds. 📔 Michael Grafnetter at Hybrid Identity Protection covers: ✅ IaC approach to Windows Firewall policy ✅ RPC filters & outbound traffic controls ✅ Hybrid environment challenges ✅ Network service discovery hipconf.com/agenda/



"It’s easier said than done, blocking outbound traffic. Inbound rules work, but outbound rules don’t cover everything. There are some issues, some gotchas." - 📔 Michael Grafnetter speaking on how to secure Domain Controllers without breaking Active Directory at #HIPConf25.