Blacksolo , Sp00f3dByt3
@mblacksolo
Security Researcher , Bughunter, Student.
ID: 1226905642587148288
10-02-2020 16:28:07
188 Tweet
690 Followers
944 Following



Time for another giveaway! We are going to send a t-shirt and a few goodies to one person who follows PentesterLab and retweets this tweet!! And we are going to give a 12-month voucher to someone who follows PentesterLab and likes this tweet!!




🔍GitLab CVE-2023-7028 - Uncover account takeover potential with a simple password reset method. Known POC: user[email][][email protected]&user[email][][email protected] Identifying vulnerable targets: 1️⃣ Utilize the nuclei template at github.com/projectdiscove… to spot exposed
![Jayesh Madnani (@jayesh25_) on Twitter photo 🔍GitLab CVE-2023-7028 - Uncover account takeover potential with a simple password reset method.
Known POC:
user[email][]=valid@email.com&user[email][]=attacker@email.com
Identifying vulnerable targets:
1️⃣ Utilize the nuclei template at github.com/projectdiscove… to spot exposed 🔍GitLab CVE-2023-7028 - Uncover account takeover potential with a simple password reset method.
Known POC:
user[email][]=valid@email.com&user[email][]=attacker@email.com
Identifying vulnerable targets:
1️⃣ Utilize the nuclei template at github.com/projectdiscove… to spot exposed](https://pbs.twimg.com/media/GECJK5aWkAAnnL0.png)


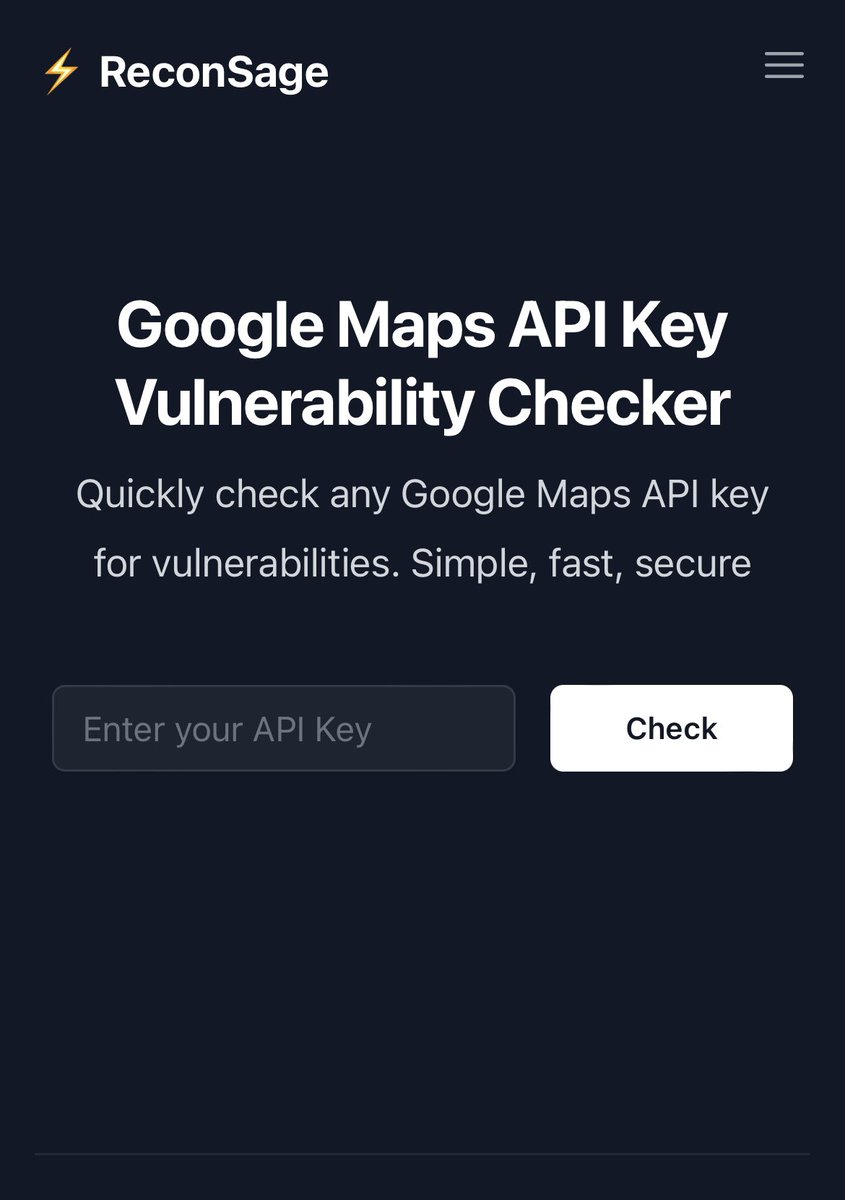
First tool added in ReconSage ⚡️ by Ravindra Lakhara 🇮🇳 Join the waitlist to get access to the new generation reconnaissance platform reconsage.com/tools/scan-gmap #bugbounty #bugbountytips #bugbountytip









We launched the Full-Time Hunters' Guild this week via the Critical Thinking - Bug Bounty Podcast community. Accountability, collaboration, data, and support staff for full-time hunters (or part-time w/ 100k+/year). Very excited to see how this boosts my BB performance in 2025. ctbb.show/full-time-rhyn…


For heavy recon bug bounty hunters: - if you go wide, connect the dots. (Bálint Magyar, BSidesBUD 🇭🇺)

![ProjectDiscovery (@pdiscoveryio) on Twitter photo [NEW-PROJECT] 🥳🥳
Katana –– A next-generation crawling and spidering framework.
→ Standard / Headless
→ Customizable Config
→ Scope control
→ Output Filters
GitHub Project –– github.com/projectdiscove…
#hackwithautomation #cybersecurity #crawler #opensource #bugbounty [NEW-PROJECT] 🥳🥳
Katana –– A next-generation crawling and spidering framework.
→ Standard / Headless
→ Customizable Config
→ Scope control
→ Output Filters
GitHub Project –– github.com/projectdiscove…
#hackwithautomation #cybersecurity #crawler #opensource #bugbounty](https://pbs.twimg.com/media/Fg99QVPaMAAYm0k.jpg)