LadyBug 🐞
@leaviljanen
Full stack cybersecurity at lavsecurity.fi and #bugbounty @hackrfi . Occasional medievalist. Tweets EN & FI. She/her. Started to move to other platforms.
ID: 262826768
08-03-2011 21:01:28
6,6K Tweet
998 Followers
750 Following










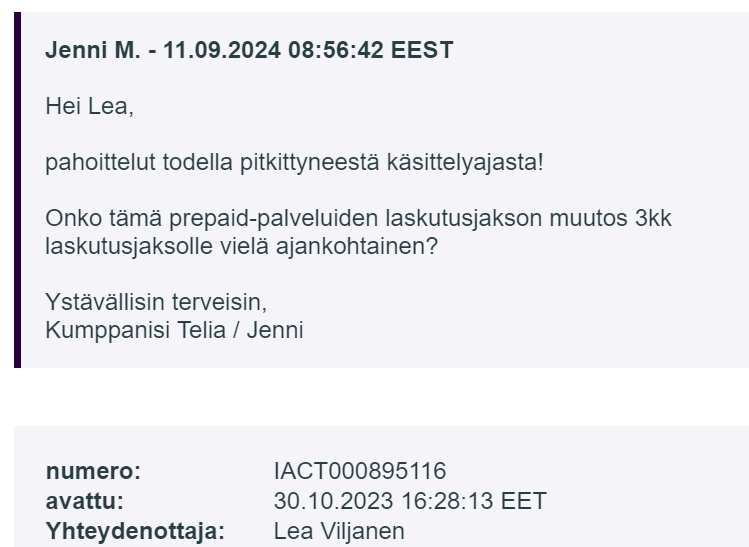
Hyvin sä vedät, Telia Finland, tiketti ei ehtinyt täyttää edes vuotta! En ymmärrä miksi kukaan firma lähtisi #Telia asiakkaaksi. Kyse ei ollut liittymistä, vaan muista IT-palveluista.






As much as I like PortSwigger #BurpPro the new API scan is a joke. One can't deselect parameters for scanning, as you do for endpoints, nor can one give any static parameter strings (for example, dates or valid object ids). The value of 404/403 returns isn't great, GIGO.