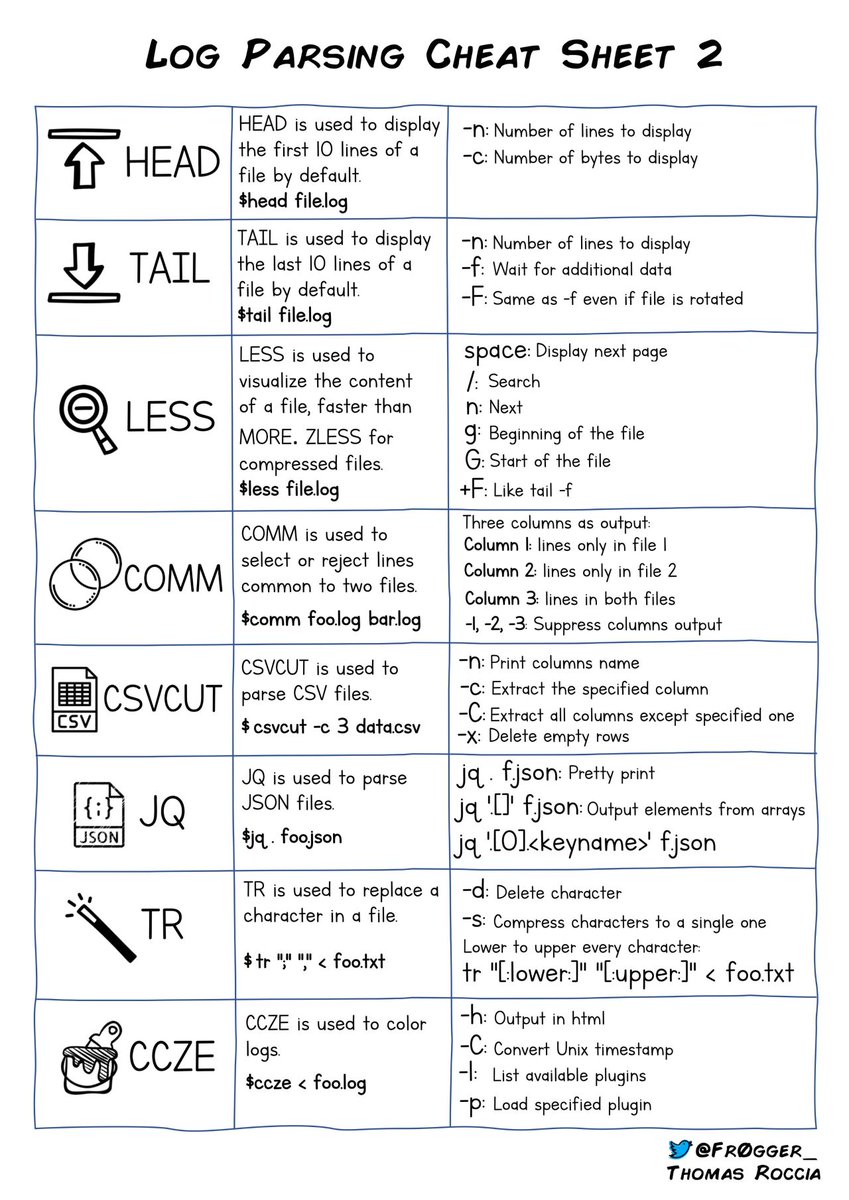
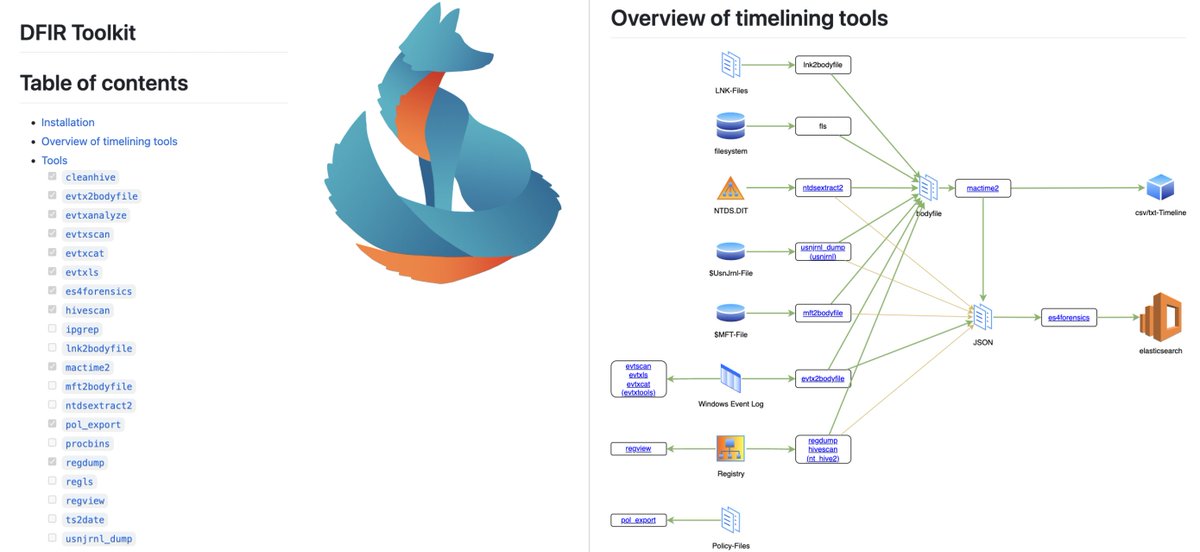
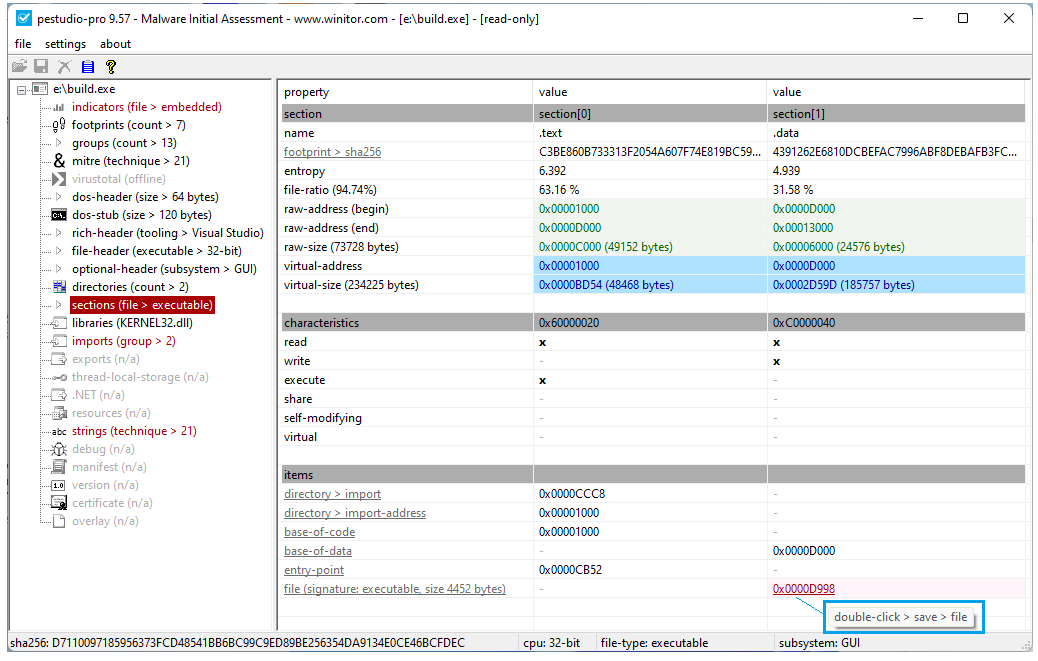
Kenneth Hunt
@kennethbhunt
Specializing in Cyber Defense 'Certified Fraud Examiner' 'Qualys Certified Specialist, Vulnerability Management'
ID: 195816506
https://huntITsolutions.com/ 27-09-2010 17:02:07
780 Tweet
1,1K Takipçi
3,3K Takip Edilen








The speech I gave at Authenticate 2022 is now available for all audiences here: youtube.com/watch?v=CWzWwh…