Jonny Johnson
@jsecurity101
Principal Windows Security Researcher @HuntressLabs | Windows Internals & Telemetry Research
ID: 746411413074116608
https://linktr.ee/jonny.johnson 24-06-2016 18:35:23
2,2K Tweet
7,7K Followers
403 Following

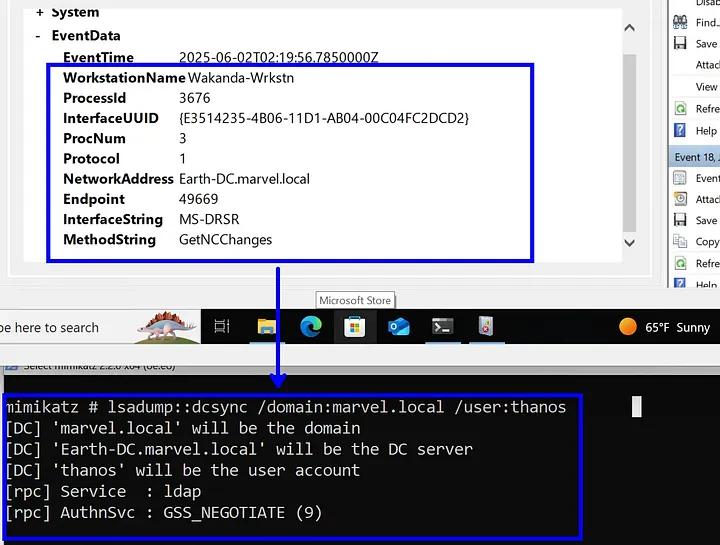
Excellent post by Johnathan Johnson (Jonny Johnson) on leveraging PLA (Performance Logs and Alerts) DCOM library to get to ETW telemetry remotely. We touched the same topic in our RTO: Evasion course, when TraceDataProvider interface was used to locate a "hidden" SysMon



Happy to finally share a new blog with Charlie Clark on our work revisiting the Kerberos Diamond Ticket. ✅ /opsec for a more genuine flow ✅ /ldap to populate the PAC 🆕 Forge a diamond service ticket using an ST We finally gave it a proper cut 💎 huntress.com/blog/recutting…



New video out 😊 showing how you can take control of port 445 and perform those magical relay attacks toward AD CS when working from a C2 agent. Way easier than before thanks to some great research by Nick Powers youtube.com/watch?v=e4f3h5…

Enroll now for our 40-hour live workshop “EDR Internals: R&D,” co-taught with Uriel Kosayev. Starts 23 Oct 2025. Dissect & build EDR drivers, master evasion techniques. Early-bird $1,450 ends 30 Sep. Details: trainsec.net/courses/edr-in… #EDR #WindowsInternals




Olaf Hartong is ridin' into Wild West Hackin' Fest - Deadwood 2025 with his talk, "I'm In Your Logs Now, Deceiving Your Analysts and Blinding Your EDR" Don't ya go missin' it, grab yer tickets to the con today: wildwesthackinfest.com/register-for-w… #WWHF #Deadwood2025 #TheFutureIs







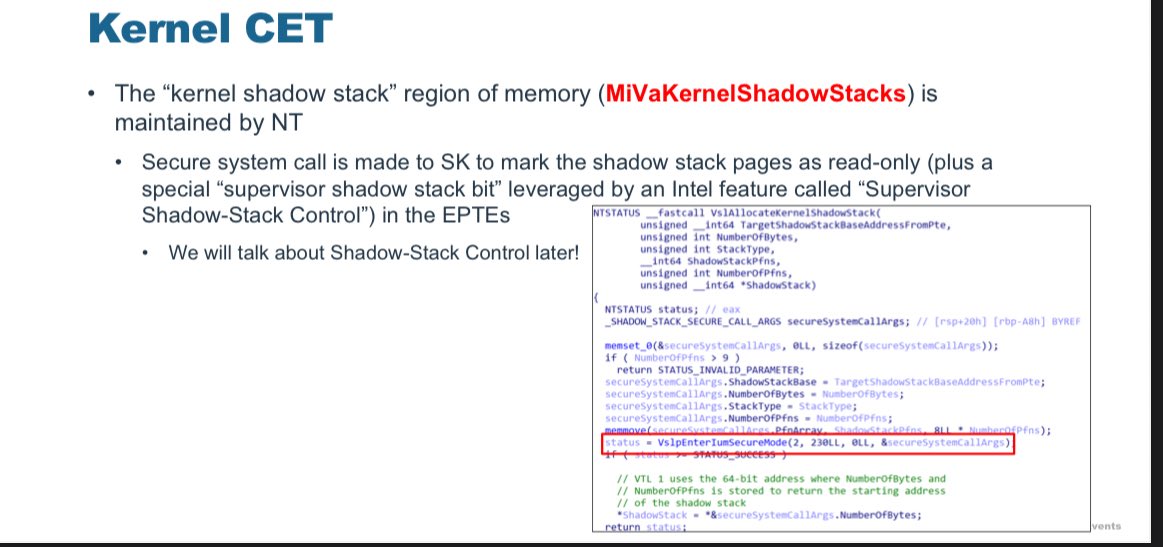
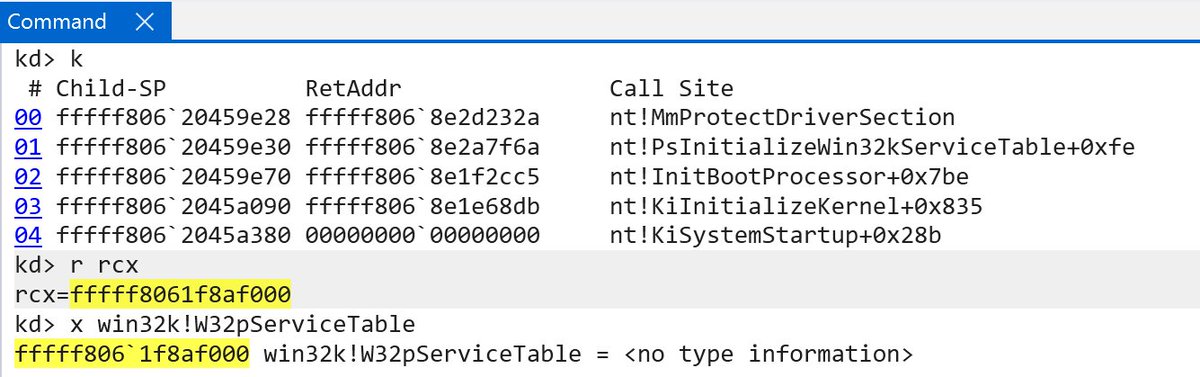
Out Of Control: How KCFG and KCET Redefine Control Flow Integrity in the Windows Kernel by Connor McGarr i.blackhat.com/BH-USA-25/Pres…