ZeusBox
@zeusb0x
Playing with Pandora's box. Sometimes it's better not to open it. Sometimes, it's better not to know.
ID: 965529099547631616
19-02-2018 10:10:50
348 Tweet
782 Takipçi
352 Takip Edilen



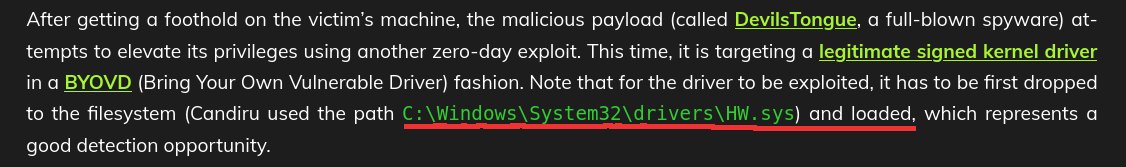
In this post "Corrupting memory without memory corruption" Man Yue Mo is showing how a powerful kernel bug, CVE-2022-20186, can be used to root a Pixel 6 from a malicious app github.blog/2022-07-27-cor…





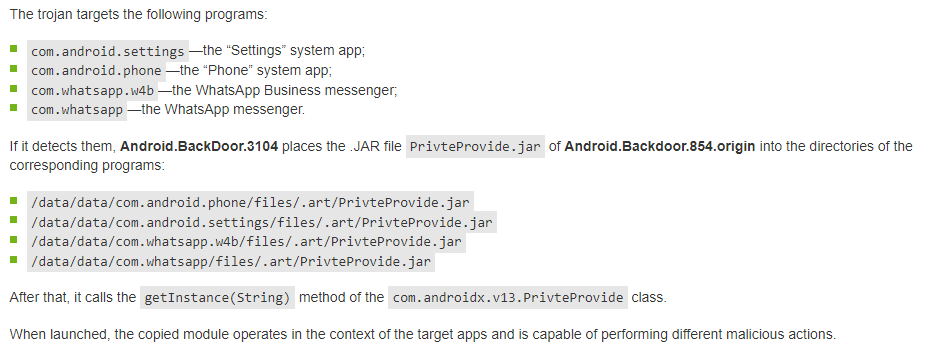
Android Universal Root: Exploiting Mobile GPU / Command Queue Drivers #MobileSecurity #AndroidSecurity #BlackHatUsa2022 [SLIDES] by 1ce0ear ExploitDr0id Jon Bottarini i.blackhat.com/USA-22/Wednesd…
![Mobile Security (@mobilesecurity_) on Twitter photo Android Universal Root: Exploiting Mobile GPU / Command Queue Drivers
#MobileSecurity #AndroidSecurity
#BlackHatUsa2022 [SLIDES] by <a href="/1ce0ear/">1ce0ear</a> <a href="/ExploitDr0id/">ExploitDr0id</a> <a href="/jon_bottarini/">Jon Bottarini</a>
i.blackhat.com/USA-22/Wednesd… Android Universal Root: Exploiting Mobile GPU / Command Queue Drivers
#MobileSecurity #AndroidSecurity
#BlackHatUsa2022 [SLIDES] by <a href="/1ce0ear/">1ce0ear</a> <a href="/ExploitDr0id/">ExploitDr0id</a> <a href="/jon_bottarini/">Jon Bottarini</a>
i.blackhat.com/USA-22/Wednesd…](https://pbs.twimg.com/media/FaC7OnQXoAEq3hw.jpg)






💥 And another new RCA up today: CVE-2022-2294, the itw 0-day in WebRTC that targeted Chrome! Authored by Natalie Silvanovich googleprojectzero.github.io/0days-in-the-w…