Vulcainreo
@vulcainreo
ID: 1499683826
https://github.com/Vulcainreo 10-06-2013 23:22:14
1,1K Tweet
420 Takipçi
679 Takip Edilen

















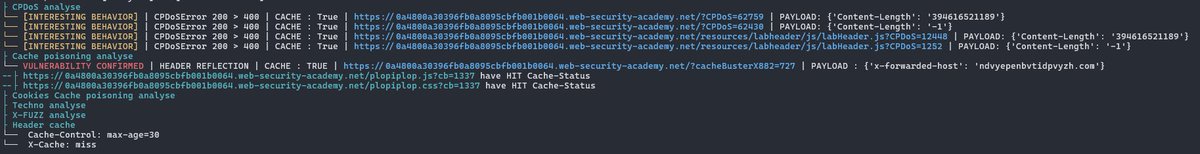
How I hacked hackers at LeHack 2025 - 7h30th3r0n3 flavien 7h30th3r0n3.fr/how-i-hacked-h… linkedin.com/posts/flavien-…


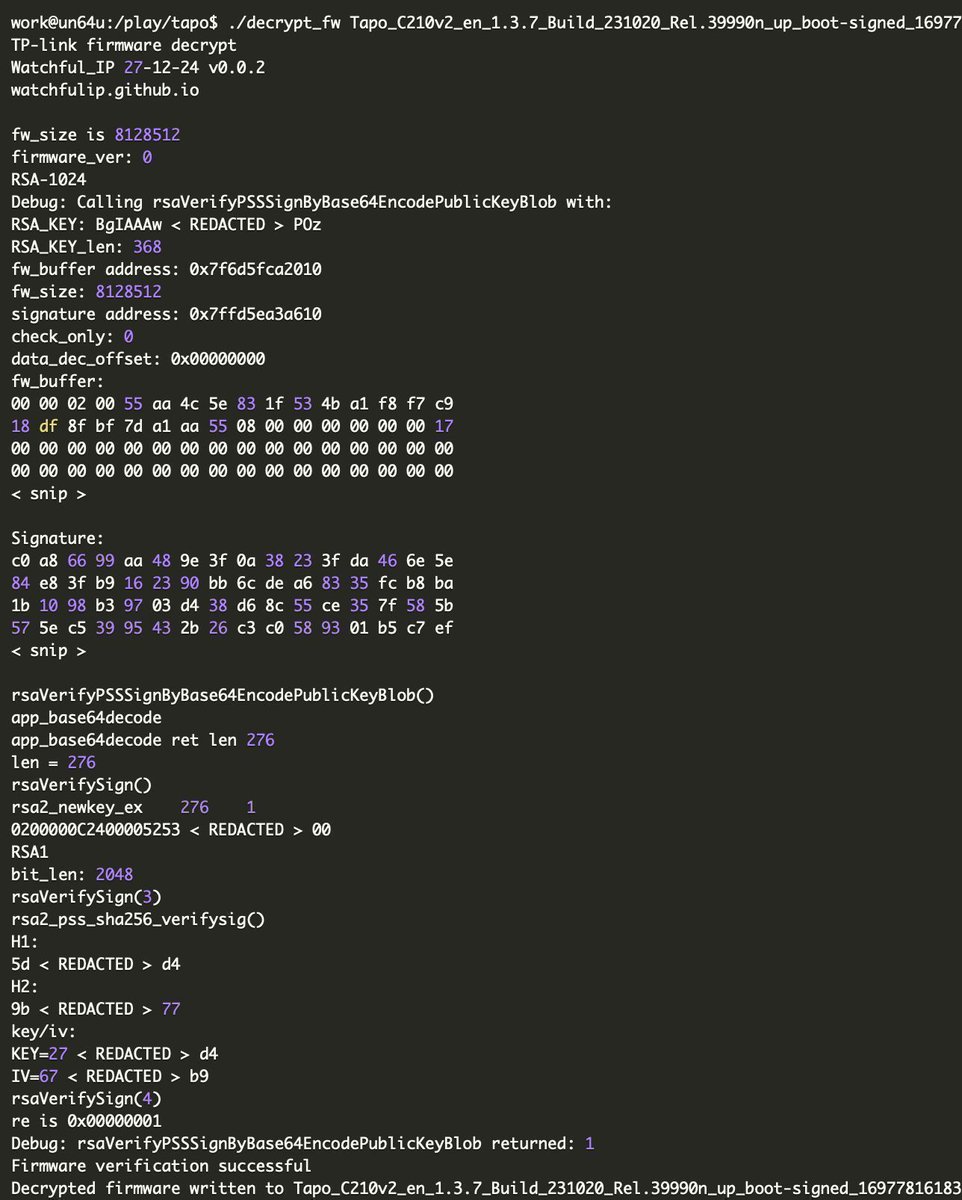
Bootloader vulnerability and firmware decryption in TP-Link (Tapo) C210 cloud cameras watchfulip.github.io/28-12-24/tp-li… Credits Watchful IP #embedded #infosec