Vishal Sharma
@vishne0
Hacker, Hustler, Security expert, Influencer, Author (Beginning Elastic Stack). #Security #infosec #Author #appsec #cybersecurity
ID: 443557785
http://www.hashmetrics.digital 22-12-2011 09:06:24
184,184K Tweet
6,6K Takipçi
4,4K Takip Edilen



TeamViewer's corporate network was breached in alleged APT hack - Lawrence Abrams bleepingcomputer.com/news/security/… bleepingcomputer.com/news/security/…






Secure Your Network with Nftables Nftables is a modern Linux firewall tool, that replaces iptables for powerful and efficient traffic management. Block IPs, restrict ports, or manage rules with simple commands - all FREE. hackers-arise.net/2024/09/04/lin… OccupytheWeb




How to bypass Cloudflare WAF? FearsOff Cybersecurity #bugbountytips #cloudflare #waf #bypass 1. Found an SQL injection but getting blocked by Cloudflare? Here's a pro tip 😏








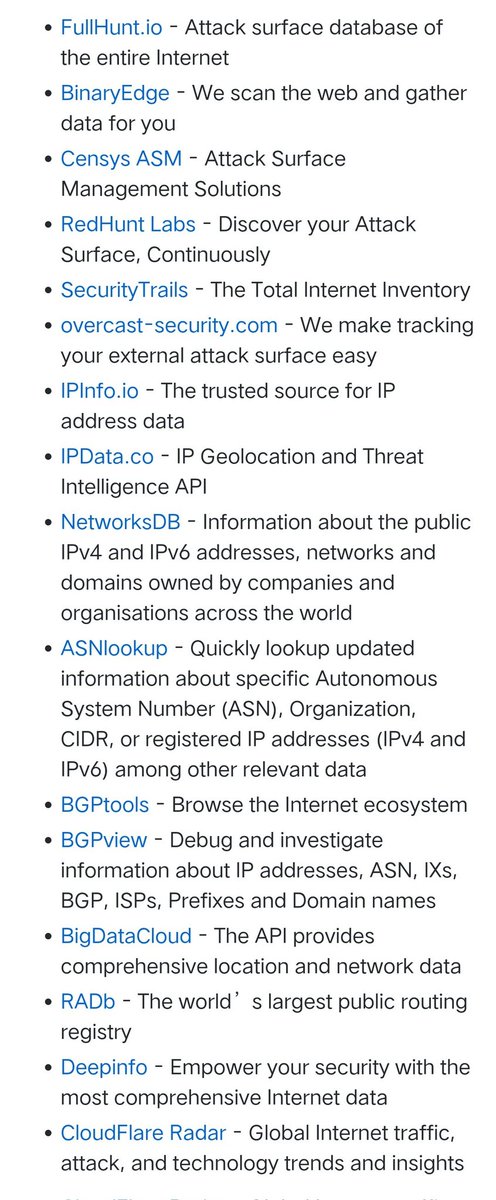
25 Essentials Every Bug Bounty Hunter Should Have Resource: thexssrat.podia.com/full-house-bun… - A Linux-ready laptop (Kali or Parrot) - Burp Suite Pro - Nmap - ffuf - SecLists - Subfinder - Amass - httpx - Naabu - dnsx or MassDNS - Nuclei - Interactsh or Burp Collaborator - Crunch or