truff
@truffzor
ID: 45525499
08-06-2009 08:22:06
132 Tweet
263 Takipçi
499 Takip Edilen







A few weeks ago I found a vulnerability in Apache Allura while reading an excellent paper from Sonar Research and the according fix. CVE has been published today. allura.apache.org/posts/2024-all… #offensivesec #infosec










My french team, for the world cup, and in collaboration with my wife, printed me a hoodie with a redacted payload on it. That bug was super fun, but quite hard to exploit! If encoded words, RFC2047 and so on are strange words to you, Gareth Heyes \u2028 presented at the same time their


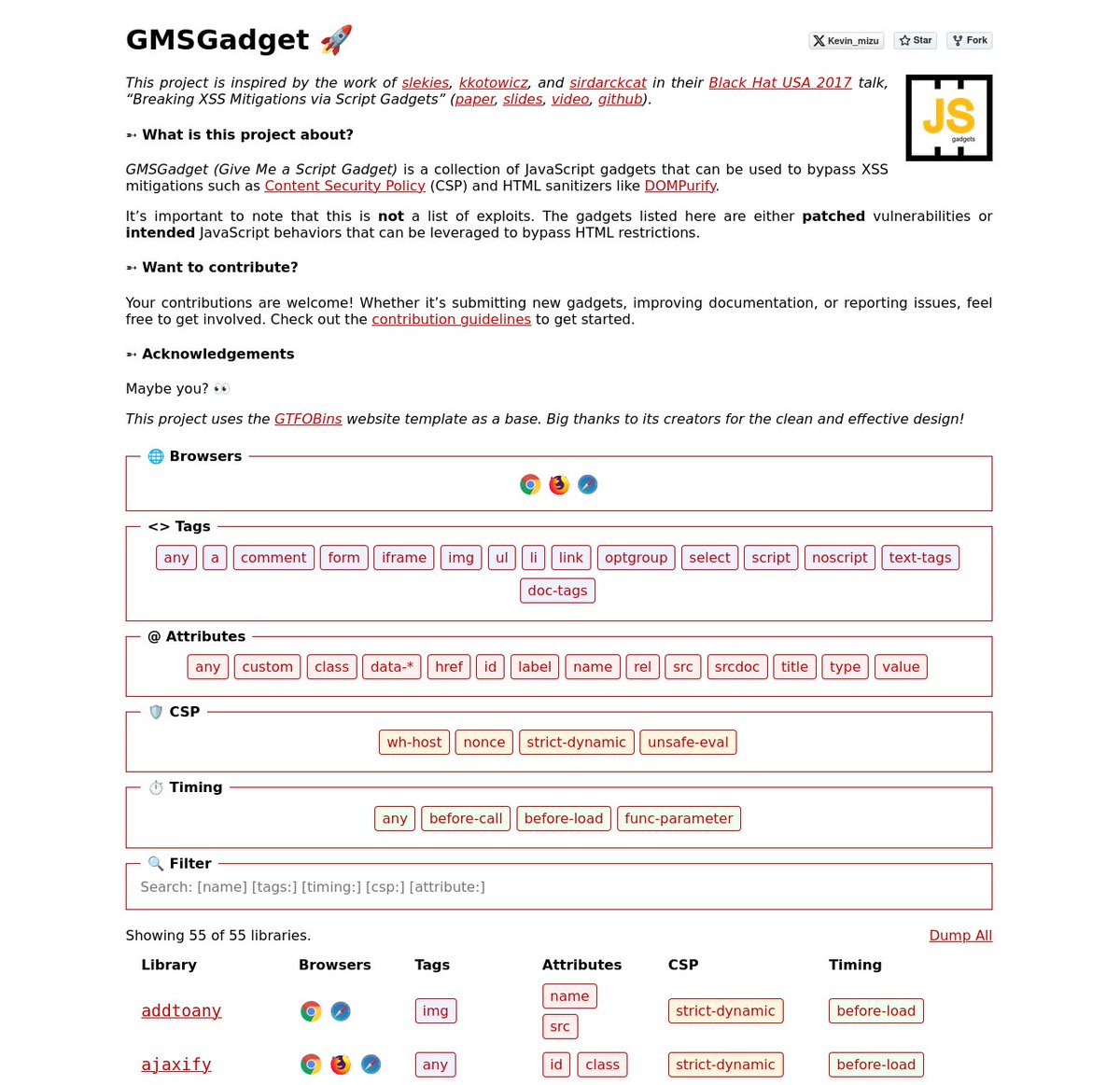
I'm happy to release a script gadgets wiki inspired by the work of Sebastian Lekies, koto, and Eduardo Vela in their Black Hat USA 2017 talk! 🔥 The goal is to provide quick access to gadgets that help bypass HTML sanitizers and CSPs 👇 gmsgadget.com 1/4